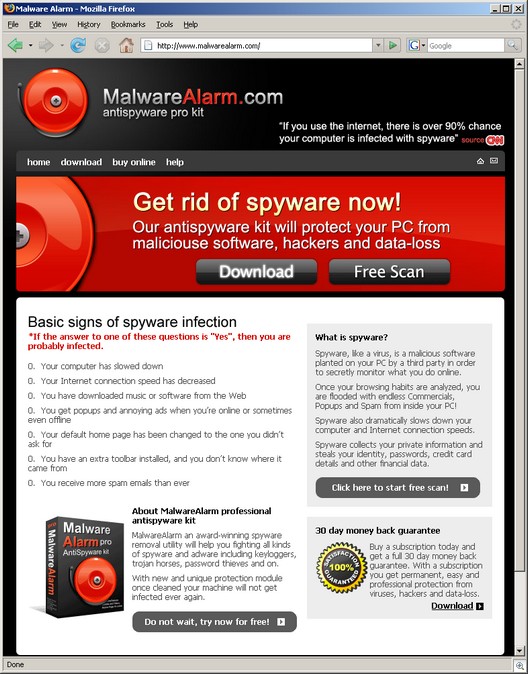
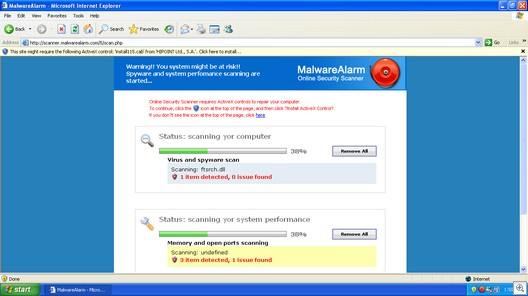
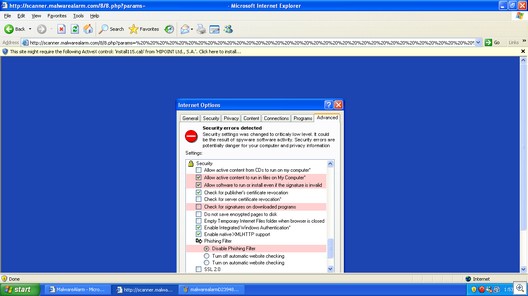
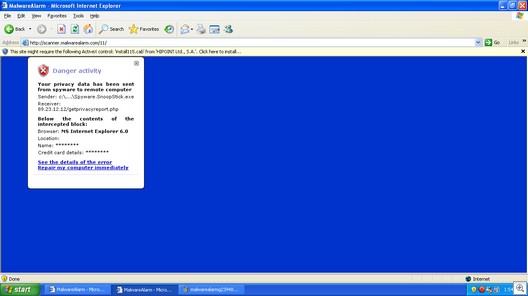
Internet Laws: the Good, the Bad and the Ugly
For a long time, lawmakers left the Internet alone. Not anymore; state and federal governments are introducing legislation left and right to try to tame cyberspace. Some of these regulations (such as the moratorium on new taxes) are good. Others, not so much. For a good synopsis of the best and worst laws affecting the Internet, see Eric Goldman’s article here.
Windows XP Back by Popular Demand at Dell
(Alex says: “Oh, thank you!) Dell announced last week on their web site that consumers will now be given the choice between XP and Vista with more desktop and laptop models. Read more here.
Get The Classic Menu Back in Office 2007
Not everyone is happy with Office 2007’s new “ribbon” interface. Some people (like me) like it; others don’t. Well, in another case of “you asked for it, you got it,” a Chinese developer has come up with an Add-on for Office 2007 that reportedly gives back the standard toolbars in Word, Excel and PowerPoint. I installed it today on the “tank” (our monster laptop) and so far, no problems. It does indeed restore the menus on a Menus tab, and you still have the ribbon tabs, too – the best of both worlds. I’ll be testing it more next week and will report any problems, but if you’re in hurry, you can download a free trial at your own risk here.
Fix Outlook 2007 Performance Problems
I like Office 2007 but I don’t like the way Outlook slowed down when I upgraded. I get hundreds of messages per day and most of my business is conducted via email; I’m also heavily dependent on my calendar. Outlook is the interface in which I “live” for a good part of every day, so performance problems in that application cost me time – and money. And I’m not the only one who’s been experiencing this problem. Well, there’s good news: Microsoft recently released an update that helps to fix some of Outlook 2007’s performance issues. I installed it on both my desktop and my laptop (the latter suffered most from this problem) and noticed immediate improvement. If you’ve been disappointed in Outlook’s performance, give it a try. You can read more about it and find links to the download here.
Does Windows Mail Censor your Messages?
I received a question from a reader who said Windows Mail won’t allow him to send outgoing email messages that contain four letter words. I’ve tried to duplicate the problem, but haven’t been able to do so – my test messages with bad words went right through. My guess is that Chris’s messages are being blocked either by his or the recipients’ ISP or local spam filters. But if you’ve had the same problem with Windows Mail and can send messages containing the same words from another email program, please let us know.
New Help Format in Vista
Instead of relying on static Help information installed when the operating system is installed, Vista defaults to Online Help, so that when you ask for help on a topic, you’ll get the latest updated content from the Microsoft servers (assuming your computer is connected to the Internet). If you’re offline, you can still use Help content stored on your hard disk. The Help and Support window has a down arrow in the lower right corner that you can click to select either Online or Offline Help.
The bad news is that Vista won’t open the old style Help files (.hlp format) that you might still have around for some applications. Previous Windows operating systems included the WinHlp32.exe program that’s used to open them, but Vista doesn’t. However, if you need it, you can download and install the program in Vista. You’ll find it here.
How to Set Password Expiration in XP Home
For better security, you can force users to change passwords periodically. In XP Pro, passwords expire every 42 days by default, but there is no default expiration period in XP Home. However, you can set one using the command line. Here’s how:
- Click Start Run and type cmd to open a command prompt window.
- At the prompt, type net accounts /maxpwage: followed by a number representing the number of days for which you want passwords to be valid.
Note this also works for Vista (all editions) and XP Pro.
Easier Way to Set Password Expiration in XP Pro
You can change the password expiration period in XP Pro by using the Group Policy Editor. Here’s how:
- Click Start Run and type gpedit.msc, then click OK to open the Group Policy Editor console.
- In the left pane under Computer Configuration, expand Local Computer Policy and then Windows Settings, then Security Settings, then Account Policies.
- Double click Password Policy.
- In the right pane, double click Maximum Password Age.
- In the Properties dialog box, enter the number of days in the field labeled Password Will Expire In.
- Click OK.
How can I get Vista to stop being an overprotective mother?
Vista’s “overprotective” behavior is one of the biggest complaints I hear. Just like with an overprotective mom, User Account Control (UAC) really is for your own good – but if you want to take the risks, you can disable the prompts.
This is done through the Local Security Policy settings in Vista Business, Enterprise and Ultimate editions. At the command prompt or in the Search/Run box on the Start menu, type secpol.msc to open the LSP console. Vista will, of course, ask for your permission to continue (but this could be the last time). In the left pane, expand Local Policies, then click Security Options.
In the right pane, scroll down to User Account Control: Behavior of the Elevation Prompt for Administrators in Admin Approval Mode. Double click it, and on the Local Security Setting tab, click the down arrow in the drop-down box and select Elevate Without Prompting. Now, when you’re logged on with an administrative account, you won’t get that annoying “are you sure?” dialog box (and you also won’t know when programs are elevating privileges). Click OK, and you’re done.
Recover from corrupt registry that prevents XP from starting
If your XP computer won’t start because of corruption in the registry, this Guided Help article will help walk you through the process of resolving the problem. Find out more in KB article 307545.
Folder doesn’t open when you click it in the All Programs list in Vista
If you click a folder to open it in the All Programs list in Windows Vista and it won’t open, this could be because the folder is stored in a certain location. There is a hotfix available to fix the problem, but you have to contact Customer Support Services to get it. For more info, see KB article 932404.
Until next week,
Deb Shinder