This recent video shows 180 Solutions is now installing Zango Search Assistant (the replacement for 180 Search Assistant) via ActiveX installs at third-party web sites.
Why is this notable?
1. The user goes to the site and gets a confusing Active/X control thrown into their face.
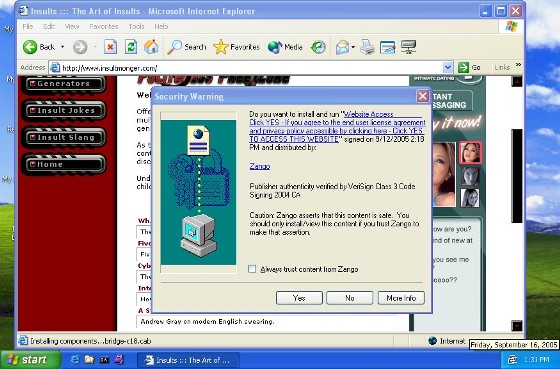
Click to enlarge
Even under Windows XP Sp2, it is intrusive and confusing. One gets one of these redirect/layover screens that directs the user to install an ActiveX control — a screen not necessarily from Zango but nevertheless confusing.
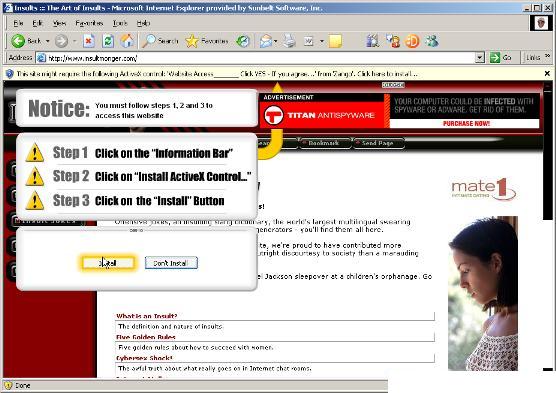
Click to enlarge
2. The ActiveX box describes this program only as “Website Access” from “Zango.” No mention or description of functionality such as pop-up advertising, installation of a toolbar, error page hijacking, etc.
3. The EULA itself likewise makes no mention of key functionality, disclosing only advertising in some vague way (redirects to partner websites) but not pop-up advertising — no mention of a toolbar at all. Click here.
4. Three separate programs are installed (with three different entries in Add/Remove Programs). There is a fourth, MediaGateway, a Zango app which is intalled if you agree to it (a different ActiveX popup).
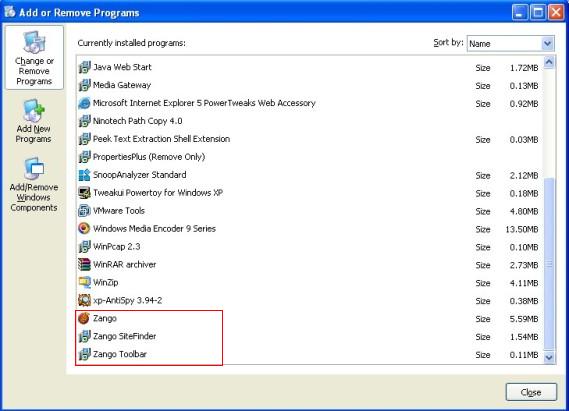
5. On one test system, a device driver capable of accessing the drive directly (ide210201.vxd) is dropped in System32. Just what this driver is being used for is unknown. See google. According to this post, “this is a legitimate file and it is used in Windows Me/98/95 computers in order to get data on the hard disk installed”.
Alex Eckelberry
(Thanks to Eric Howes for his invaluable contribution)
8:44 PM Update: 180 Solutions is fiercely defending this install, and we expect something to post later tonight or tomorrow morning.
In the meantime, here is some more information and clarifications.
The VXD file mentioned above (ide210201.vxd) comes from MediaGateway, a Zango application. I did not get this file on a re-test this evening with Windows SP XP2.
So here is how the install occurs on a Windows XP Sp2 system:
After getting the “You Must Click Yes” dialog, and you agree to install the ActiveX control, you get the standard ActiveX install warning:

After agreeing to Zango, to their credit, you then get these screens:
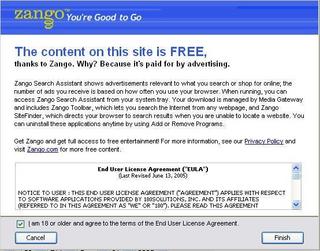
Note that this screen is pre-selected, has a big EULA stuffed into a tiny box, etc. But it is a step better than what we’ve seen in the past…

So, notice is given that Zango is being installed, and one can uninstall the programs through Add/Remove.
Here’s the key problem, though: The use of ActiveX installs is problematic, since one cannot provide adequate notice and disclosure in the initial screen — and it’s a method of install that has been heavily abused in the spyware space.
ActiveX controls are used by many reputable publishers, such as Microsoft and Trend Micro. However, in these cases, the user is quite aware of what is going on. Simply getting an ActiveX control popping up in your face (the case if you’re not running SP2) simply confuses and baffles users.
However, to 180’s credit, they do provide an install screen after the ActiveX install which clarifies what is going on.
A final note: Contrary to intimations in the installer and uninstaller, access to this website does not need Zango.