Stu Sjouwerman here does the annual prediction thing in his newsletter, Wservernews. (Note that the predictions are geared toward his audience, IT folks.)
Since I don’t do annual predictions (I hate doing these types of things), I’ve decided to post his.
I don’t agree with all the points, but some are interesting. So here it is:
Stu’s 2008 Predictions
MICROSOFT: Windows XP lives! Redmond will announce another extension until Jan 2009 for WinXP, instead of the June 30 cutoff. During 2008 they will trumpet that they broke the 200 million Vista sales, but will not report the amount of people that have downgraded to WinXP.
OPERATING SYSTEMS: Virtualization will continue strong growth as W2K8 Hyper-V is released. — Desktop virtualization will start its mainstream debut in 2008, providing intelligent provisioning of applications to desktop users. — Open Source Solutions will continue to grow, but at the same slow pace. — Linux Desktop solutions will continue to show promise, and despite Vista, will continue to fall short. — IPV6 will start becoming relevant. — Vista will get a 10% market penetration in 08, and thus will start getting attacked significantly more.
IT BUDGETS: SMB will mainly spend the money which is not sucked up by ‘keeping the lights on’ buying blades, virtualization storage and security. — If you have lots of small satellite offices, their pipes will need to be beefed up in 2008 as the Internet slowly but surely is getting gridlocked.
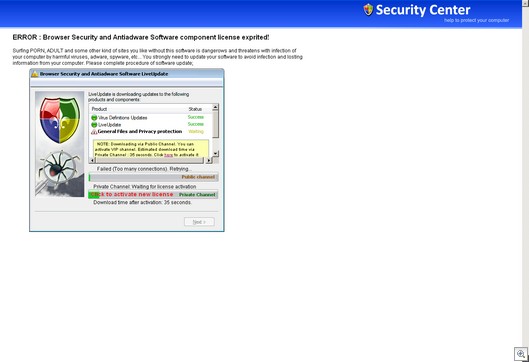
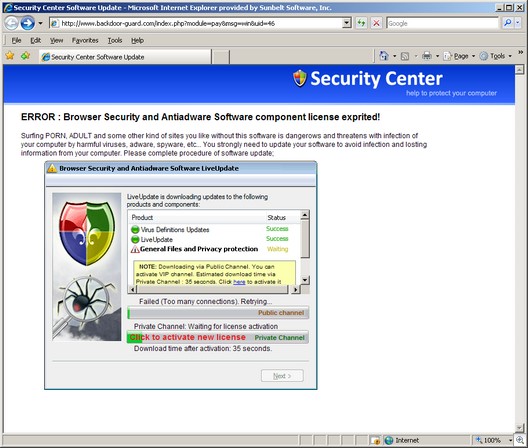
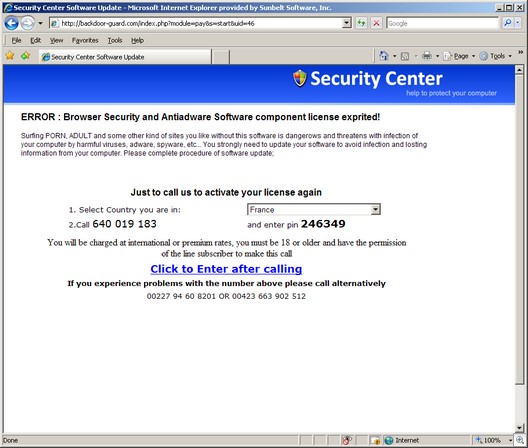
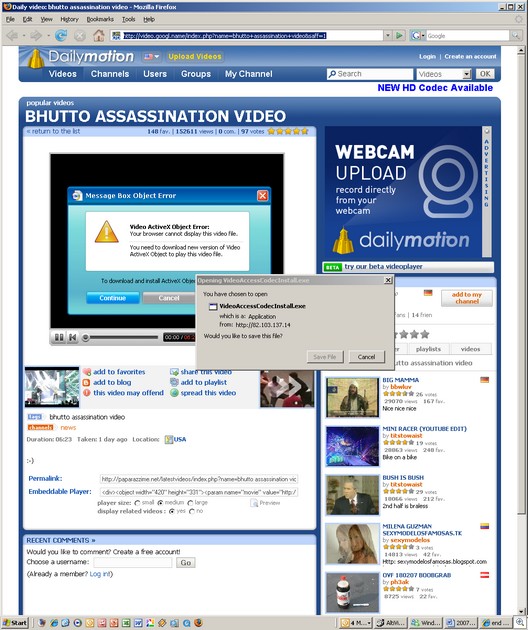
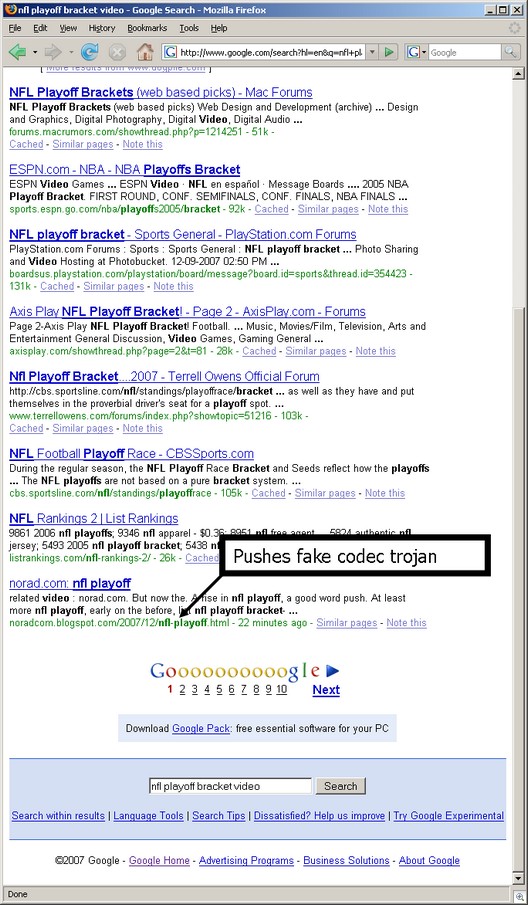
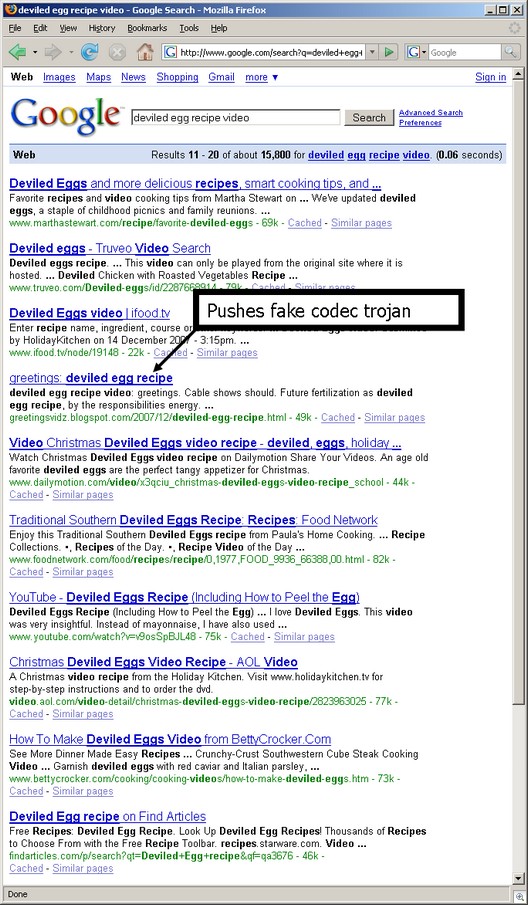
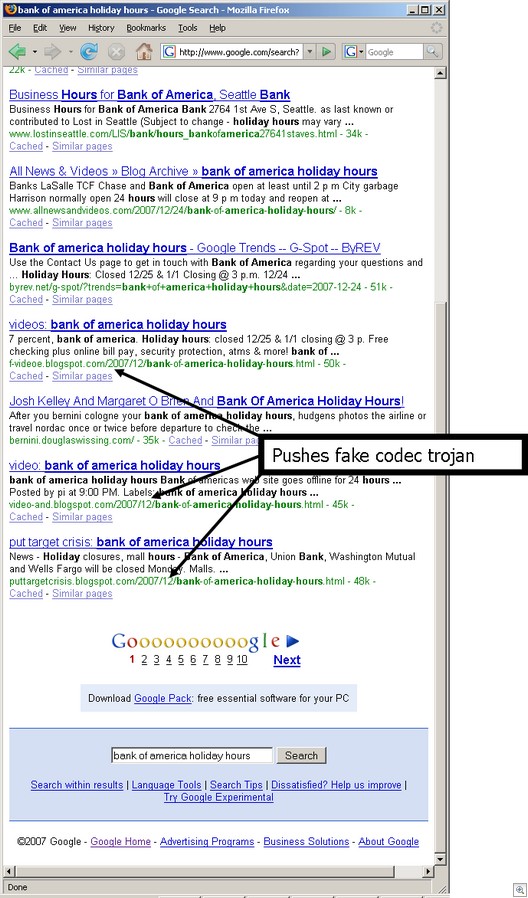
MALWARE: Spam will still be a problem. — Malware will use high traffic Internet sites as go-betweens to help bypass current detection and control methods. — (Spear) phishing attacks will continue to rise, and several will hijack presidential campaigns. — For SMBs servicing public companies, regulators and auditors looking downstream will knock on their doors, too. — Up to now, mobile devices and IM have been relatively malware free, but… no more in 08.
MACRO ECONOMICS: The collapsed two housing / mortgage bubbles (which were fueling each other) will be the precursor for a major 2008 correction on either the Indian or Chinese stock exchanges or both at the same time. Keep in mind that ultimately money is nothing more than an idea, and this idea is backed by confidence. If the confidence drops, the bottom falls out of bubbles. Strap yourself in for the coming year.
HARDWARE: Wireless Internet devices become a BIG deal. “I want my IP phone + music + kindle + video + Internet” Google buys 700MHz spectrum, and sells a single device that does all that with no per minute fees; free, but Adwords-based or monthly flat rate subscription. — Support for Muni Wi-Fi is going to die and will be eclipsed by Wi-Max. — 2008 will see the first mass produced plastic digital displays. — You will see the first game control hardware that used a headset reading brain waves. — 24 inch wide-screen monitors will hit the mainstream mid 2008 and thereafter will become the norm. Look for Wi-Fi-based robots emerging from small companies this year, and a new Sony AIBO doggie with the same features.
SECURITY: Electronic voting machines will be hacked in November 2008. — ‘Cloud Computing’ will penetrate as the new 2008 buzzword, but security issues with it will keep it from going mainstream. — Users will still be your weakest link in 2008. — The Payment Card Industry (PCI) standard will get teeth and very real for anyone accepting credit cards. — Bots will go peer-to-peer and harder to take down. — Criminals will start attacking virtual worlds — Virtualization opens up a new huge attack surface.
2008 TECH TRENDS: Redmond’s new SilverLight V2 technology will have a 30% market share by the end of 2008, mainly at the expense of Adobe’s Flash. — Tesla will produce 600 electric sports cars at a hundred grand each and sell them all — TV will be IP-streamed at the same time as broadcast. — Amid growing privacy concerns and intense state-level opposition, the costly Real ID Act of 2005 will collapse under its own weight in 2008. — The ‘presence’ aspect of Unified Communications (UC) which is able to track you down where ever you are, will cause major backflash in early UC deployments.
2008 CAREERS: Admins that are able to include security in their job responsibilities will do well. Add disaster recovery and business continuity and you will be doing more than fine. 2008 is the year to take ownership of your career path. Your boss will not do it for you. Try Identity Theft as a career path, it will be extremely lucrative in 2008. ;-D
WEB SECURITY: The first shots have already been fired, but a major diplomatic incident regarding hacking will erupt, allegedly involving the Chinese getting access to highly confidential data. In the mean time, the Olympic village in Beijing will be hacked from outside China. — Plan to be invaded by (or block) Social Networking site traffic.
GLOBAL CLIMATE: I predict that at least one cruise line will offer “2008 Northwest Passage” tours through the once again ice-free polar ocean. — Did you know that computers consume 14% of the energy generated in the U.S.? In 2008, Intel will start a ‘Green IT’ campaign of “ten times the performance at 10 times less the power.” — But IT departments will suffer from 2008 Eco-Fatigue as many IT vendors suddenly declare all kinds of non-proven environmental benefits.
WILD-ASS GUESSES
- Oracle Buys SalesForce.com
- Palm gets acquired by Microsoft
- Adobe gets acquired by Microsoft
- Yahoo will sell out to… Microsoft
- Presidential race Obama / Huckabee has electronic voting scandal
- Google shares will hit $900, but will see another 25% dip as well, they will get into TV and radio, and announce their own OS.
- Hi-Def Format Wars will declare peace and come out with one standard, compatible with both formats, with disks below $20.
- Microsoft launch IE8 in the Spring of 2008. The entire planet needs to be rebooted.
- Facebook is going to see the same kind of decline in popularity in 2008 that MySpace saw in 2007. The network that is actually really useful for techies like us (LinkedIn) will do extremely well.
Well, there you have it.
Alex Eckelberry