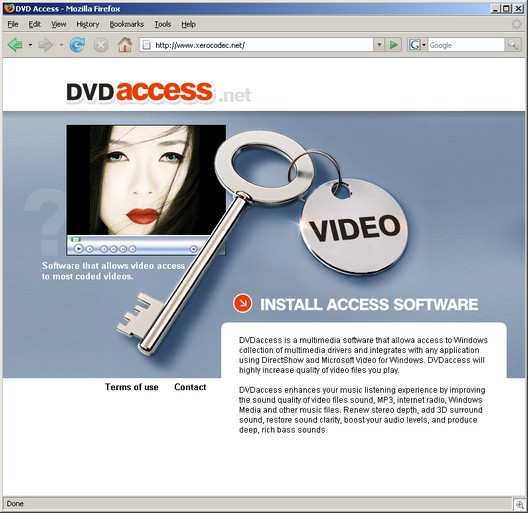
Our friends over at Secureworks, who have done some great research on Storm, pointed out some very interesting information to us recently. The spam template (which typically includes data such as a peer list, addresses to spam to, spam message content and some other data), was updated to include a list of over 1,000 Geocities domains.
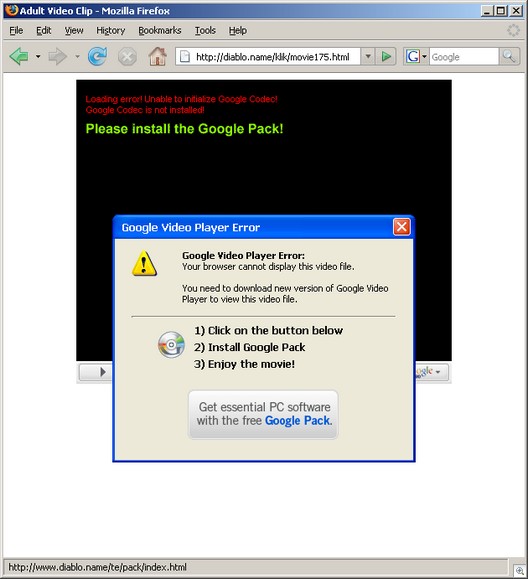
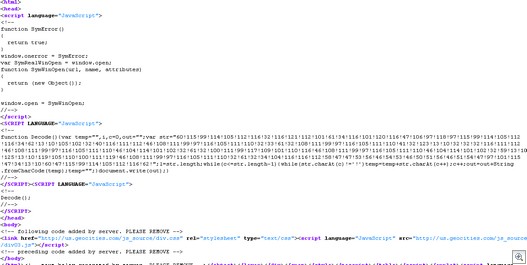
These domains include a small piece of Javascript code that re-directs to a malicious webserver:
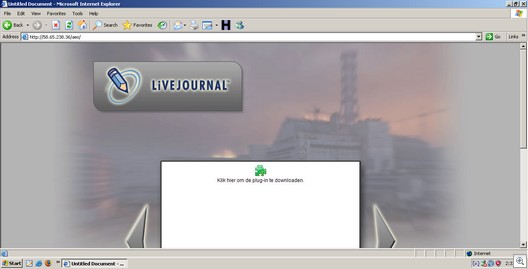
This page informs you that it is necessary to download and install a plug-in in order to view the content.
In reality, the “plug-in” is a variant of the dangerous information stealing malware called Backdoor.Win32.Smalll.lu, which was first found back in late 2006. Many variants have spawned and as a result: Infostealer.Monstres, Infostealer.Banker.C, NTOS, PRG, and GPCode/Glamour (which included a file encrypting/ransomware function).
Stolen data from this Trojan is actively being uploaded to a server located in Turkey.
This particular attack only appears to target Dutch/German users and doesn’t appear to be widespread. However, it is not typical for the Storm botnet to be used to spread other malware in this manner. This could indicate that the Storm herders are making the power of their massive botnet available to other malware groups.
Adam Thomas
Malware research


![Lovenote_ss%5B1%5D[1]](http://sunbeltblog.eckelberry.com/wp-content/ihs/alex/lovenote_ss_255B1_255D%5B1%5D_thumb.jpg)