If you like downloading or installing programs on your PC related to XBox gaming, you might want to take note of this writeup. There’s a DIY kit in circulation that allows an attacker to create a website claiming to be an XBox Live application for your computer. We’ve grabbed the kit and had a poke around inside to see how this operates – all it takes is two pages of HTML, a fake graphic and a Java archive to set this one in motion. This is the kit in question:

Upon visiting any site related to this scam, the end-user will see a blank webpage with nothing other than a Java notice and a fake Softpedia award at the bottom of the screen:
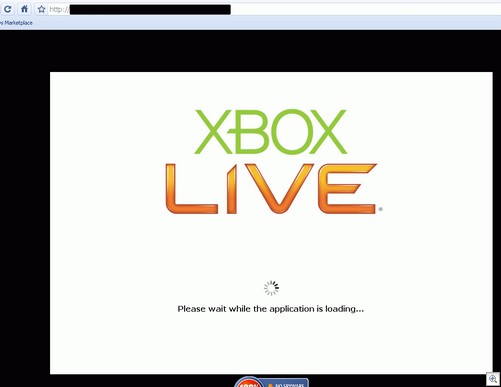
After a second or two, things become a little more lively with a splash page claiming “the application is loading”:
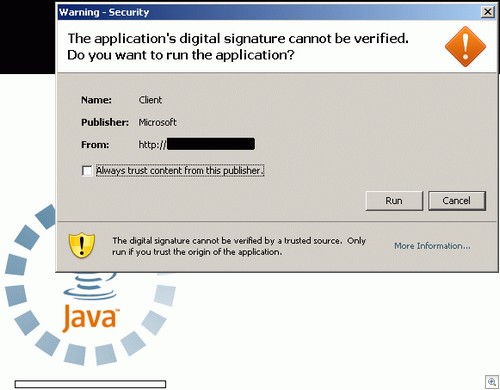
At this stage, the end-user will be presented with the following Java Application Digital Signature Permission Screen:
Note that they list the publisher as “Microsoft”, which is always going to make potential victims a little bit easier to trick into hitting the Run button. As a counterbalance, notice also the message in large text that reads “The application’s digital signature cannot be verified. Do you want to run the application?”
The smart answer, of course, is “no”.
If the end-user hits “Run”, the applet will download whatever file it’s configured to grab then execute it. At this point, things have gone horribly wrong for all concerned (apart from the creator of the fake application page).
If we download the file offered up by the above prompt separately, we can see that the end-user installs a file that looks a little bit like an art program.

It isn’t an art program.
After running the above file, the end-user will find “Crypted.exe” in their Temp folder. This is actually something called Trojan-PWS.Win32.Fignotok.A, a password stealing program that targets applications such as Firefox, Steam, DynDNS and various IM clients.
It’s worth remembering that the DIY kit allows the attacker to change the infection file offered up by the applet to be anything they desire. Talking about unsigned applets and hijack files is making me feel a little bit 2005, but I guess what goes around comes around.
* ALWAYS be cautious when presented with an unknown application. Don’t just run it; go Google it first and see if anyone else even mentions it.
* In the same spirit, be very wary of unsigned applications on random websites you’ve never heard of.
* Anyone can grab an award badge from a website and claim they’re the “Best thing ever”.
We detect the executable launched by the applet as Trojan.Win32.Generic!BT. Thanks to Adam Thomas from Sunbelt’s Malware Research Team for additional testing.
Christopher Boyd .