Avid readers of this blog can attest that we’ve been writing about FakeRean for, oh, quite a number of months now. In case you missed out on those posts or you no longer remember them, I have for you here a short list of what we’ve written about this rogue AV family so far:
- What’s in a (rogue) name? VirusTotal 2010
- Malicious warez site offers Firefox 4.0 beta download scam
- Rogue downloads look real: read the fine print
- Obama, birth certificates, and Rogue AV
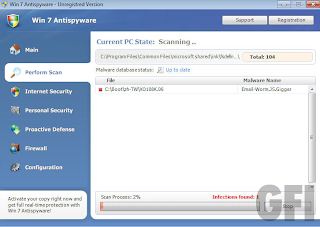
FakeRean is initially discovered by Microsoft a couple of years ago. Like all rogue AV families, it displays fake scanning results to users in an effort to dupe them into coughing up cash in order to register the software and clean their systems supposedly. This family also alters the infected system’s registry quite extensively and drops lots of component and shortcut files, among other things. What sets FakeRean apart from the usual rogues is its ability to hijack a file association for executable (.EXE) files, which allows it to reappear every time an application is run.
Our intrepid rogue AV hunter, Patrick Jordan, spotted new ways on how FakeRean is currently being distributed online, and by the looks of things, the bad guys behind it have not only casted a wider net but also went, erm, hard-core. Case in point:
Click to enlarge
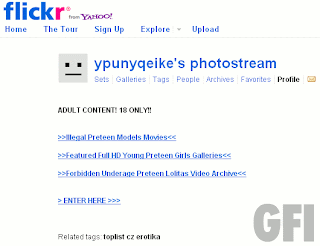
The above page is found on SourceForge.net, a prominent repository of open-source software, as a profile page. Of course, it wouldn’t matter whether you’re 18 or not, you still get a free but malicious software to download and run on your systems once you click any of the buttons there. This software is a PDF exploit that, once installed, drops and also installs FakeRean. We detect the exploit as Exploit.PDF-JS.Gen (v).
Click to enlarge
Doing a simple search yields results that show a prevailing problem within the said domain.
Click to enlarge
This SourceForge profile URL, and some 100+ other varying Web page URLs, is contained on imonline(dot)nl(slash)ukabefijac.
Click to enlarge
Click to enlarge
Some of Jordan’s finds regarding these Web pages involve prominent domain names, which includes (but are not limited to) the following:
- Flickr
- Yahoo!
- Scribd
- TED
- Formspring
- Posterous
- Box.Net
Click to enlarge
Click to enlarge
All URLs are redirect via seoholding(dot)com. Fortunately, VIPRE users are already protected from this domain if they are accidentally diverted to it.
Click to enlarge
We advise Internet users to be careful when clicking image and text links online. Be extra careful, if not steer clear all together, when visiting online profiles hosted on any site that look suspicious.
Jovi Umawing (Thanks to Patrick for finding this and Chris for the assist)