Not too long ago, we saw a pirated version of Kaspersky Anti-virus being downloaded onto infected machines and used in conjunction with what became known to some as “SpamThru“.
Joe Stewart published a great analysis on this operation:
Anti-Virus Scanning
Like many viruses and trojans, SpamThru attempts to prevent installed anti-virus software from downloading updates by adding entries into the %sysdir%driversetchosts file pointing the AV update sites to the localhost address. In the past, we’ve also seen malware which tries to uproot other competing malware on an infected system by killing its processes, removing its registry keys, or setting up mutexes which fool the other malware into thinking it is already running and then exiting at start.SpamThru takes the game to a new level, actually using an antivirus engine against potential rivals. At startup, SpamThru requests and loads a DLL from the control server. This DLL in turn downloads a pirated copy of Kaspersky AntiVirus for WinGate from the control server into a concealed directory on the infected system. It patches the license signature check in-memory in the Kaspersky DLL in order to avoid having Kaspersky refuse to run due to an invalid or expired license. Ten minutes after the download of the DLL, it begins to scan the system for malware, skipping files which it detects are part of its own installation. Any other malware found on the system is then set up to be deleted by Windows at the next reboot.
In other words:
1. The machine is infected with the SpamThru trojan.
2. Antivirus programs are disabled from downloading updates.
3. The SpamThru trojan runs a hacked version of Kaspersky AV to kill off any compettiive malware (while making sure to that Kaspersky’s product leaves SpamThru alone).
4. SpamThru has a field day using the infected machine to send out spam.
Now, it might appear that a rival group to SpamThru might be striking back (though we have no proof to that claim, but we are not seeing SpamThru associated with this new piece of malware). Only these guys are using Dr. Web antivirus instead of Kaspersky.
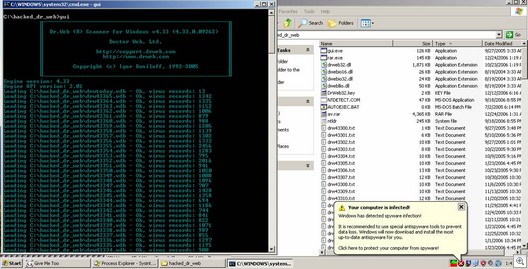
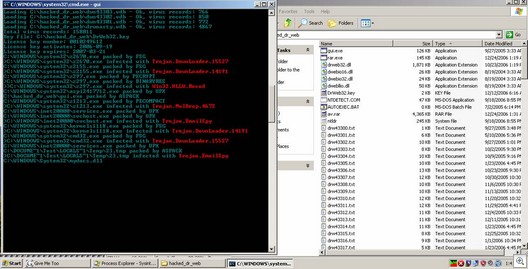
Some pictures . . . Scanner working:
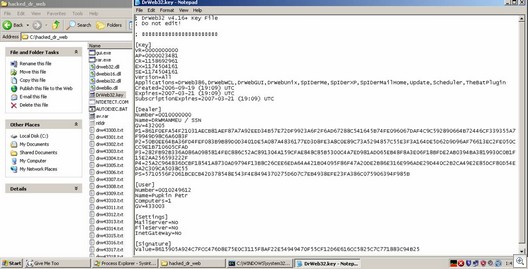
Key File. Registered to Pupkin Petr?
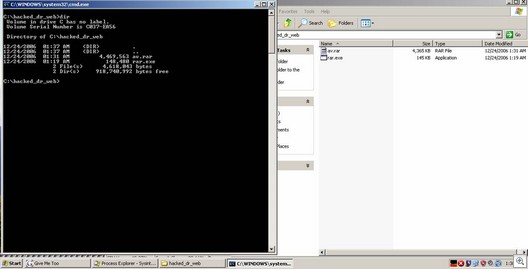
Rar.exe unpacking the av.rar archive
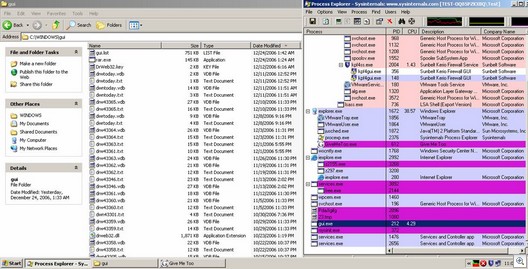
Scanner in action . . . In “real life”, it runs silently in the background:
Adam Thomas and Alex Eckelberry