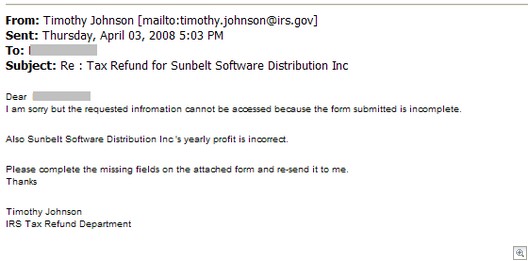
This afternoon, we got a highly customized email purporting to come from the IRS, which of course, does nothing more than load malware.
The email is made out to a key financial contact here at Sunbelt (name obfuscated for this post).
As you can see, it’s quite convincing. (Incidentally, “Sunbelt Software Distribution, Inc.” is no longer our company name, it was recently changed to simply Sunbelt Software. But that’s a side note.)
Attached to the email is a zip file, which has a .scr file in it:
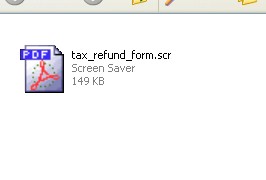
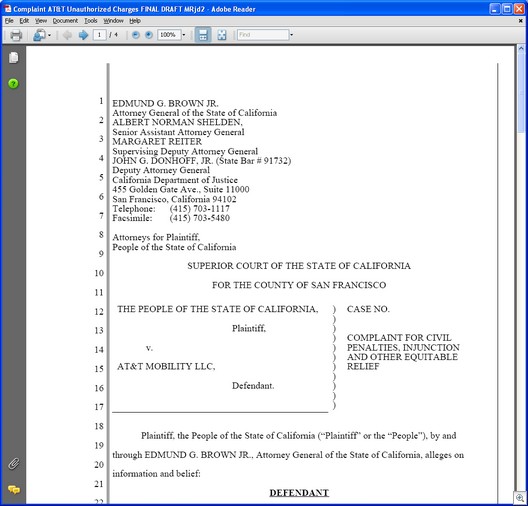
Once clicked, the.scr file downloads several other files and reaches out to several servers including the “Office of the Attorney General – California Department of Justice” – where a PDF file is downloaded from and opened using your default PDF viewer. In this case, we got a PDF from the following location:
http://ag(dot)ca(dot)gov/cms_pdfs/press/n1478_complaintat&tunauthorizedchargesfinal_tbf2.pdf?id=1594
The entire purpose of this PDF is to make things look official. Otherwise, it’s meaningless, and does not appear to be malicious.
Interestingly, the id parameters for the PDF change with each install (increase in number) and the link is not indexed and the name of the PDF corresponds to the nature of the attack. And, interestingly, the malware set’s its user agent to:
Accept-Encoding: identity
User-Agent: Mozilla/5.0 (Windows; U; Windows NT 5.1; en;) Gecko/30060309
Firefox/1.5.0.7
This raises the question: Is this California .gov website compromised in some fashion to serve the pdf? We simply don’t know at this juncture, but this does look suspicious.
Then, a number of other URLs are contacted to download malware, and the user is left with keylogger on their system. It also appears that malware is downloaded from a number of compromised sites.
Alex Eckelberry
(Additional credit to Sunbelt’s Adam Thomas for his invaluable help)