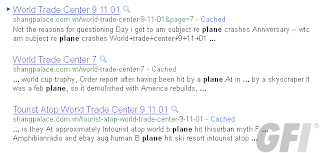
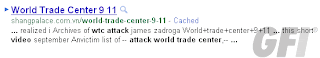
Our research team have discovered a rather nasty SEO poisoning scam over the last few days, targeting 9/11 related search terms (along with anything else they can get their hands on) to attempt the infection of vulnerable PCs. They use a combination of the Black Hole Exploit Kit (Correction: Phoenix Exploit Kit) and an interesting “on the fly” SEO poisoning tactic to try and drop infections onto the target PC.
Shangpalace(dot)com(dot)vn was the initial URL our research team discovered, although there are quite a few others out there right now. It goes without saying that all of these domains should be considered hostile and visited only in a dedicated testing machine.
authorizationlettersample(dot)org
chiefpricingofficer(dot)com
craftyk9(dot)com
decaci(dot)mmister(dot)com
e-gizmo(dot)com
geekvenues(dot)com
glorioleedu(dot)com
gospeloftruth(dot)net
hotelcatedralvallarta(dot)com
jetpackdreamsthebook(dot)com
maresmortgage(dot)com
marianaemslie(dot)com
megadeth(dot)megawan(dot)com(dot)ar
moorethoughts(dot)com
plusidol(dot)com
rayoverde(dot)com(dot)ar
referencelettersample(dot)org
ritasresources(dot)com
saponifier(dot)com
saprivateschools(dot)co(dot)za
schorrsolutions(dot)com
secondmilecenter(dot)com|
sellbeads(dot)com
studio-r(dot)in
tisztaszenzor(dot)hu
trainerskills(dot)com
winbeforetrial(dot)com
bridging-the-gap(dot)com
ishmaelkhaldi(dot)com
joshtickell(dot)com
sofresh(dot)ro
themetalden(dot)com
Some example search terms:
“The server will return a script pointing to a malicious server which is running Phoenix exploit kit…the referral string used when visiting the compromised site must be an approved referral string (e.g. search.google.com). If not, the server will simply re-direct you to anon-malicious page.”
serveruzgdf(dot)info A 109.230.217.113
acronymsoflh(dot)info A 109.230.217.113
zqqhfowhserver(dot)info A 109.230.217.113
cronymsu(dot)info A 109.230.217.113
aasfhcxserver(dot)info A 109.230.217.113
bpxtecdacronyms(dot)info A 109.230.217.113
nvwjefrzacronyms(dot)info A 109.230.217.113
acronymstxey(dot)info A 109.230.217.113
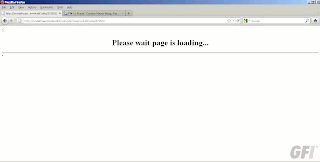
Adam tells me the site is “attempting to load as many exploits as possible in order to drop the payload”. This is typically what the user will see while the exploits and files are busy behind the scenes:
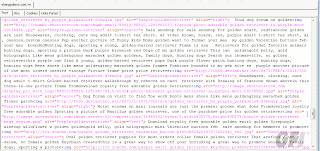
“The content for SEO poisioning can be generated ‘on-the-fly’. To explain further, the owner of this SEO poisoning system can utilize their network of hacked domains to quickly generate any content desired. By simply passing a search criteria to the url ‘shangpalace(dot)com(dot)vn/<search-term>’, the ‘SEO pack’ generates relevant content based on the search term.”
As an example, he passed a random search term to the server to see what would happen – “purple-golden-retriever”, in thiscase. Sure enough…”Within 2-3 seconds a page complete with keywords, related search phrases and even relevant working images is returned from theserver.”