This morning, Sunbelt researchers discovered a new custom Trojan that attempts to steal money by selling a fake iPhone. This Trojan looks custom-built and has very poor coverage by AV vendors (report here).
The malware produces a popup, triggered by going to yahoo.com or google.com. There are multiple types of popups, including one saying “supported by Google” and one “supported by Yahoo”.


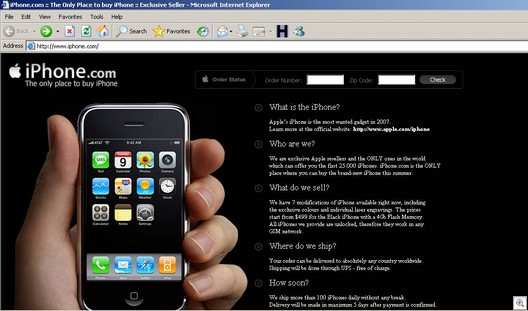
So, normally, when you go to iPhone.com, you get redirected to Apple’s site — http://www.apple.com/iphone/
However, on this infected system, you get directed to a custom “iphone.com” which actually is a fake site.
The Trojan is pulling content from your local disk in a file that has been created in %system%confg.xml.
Also, we have our BHO (Browser Helper Object) which is created:
BHO: H – {AA7F2000-EA05-489d-900C-3C7C0A5497A3} – C:WINDOWSsystem32rwera21s1.dll
They are using this BHO to inject code into Internet Explorer to make it appear as if you are on a website owned by Apple. The same technique is used by malware to target banking websites.
The site is being hosted on HOSTFRESH, which is a hotbed of malicious activity.
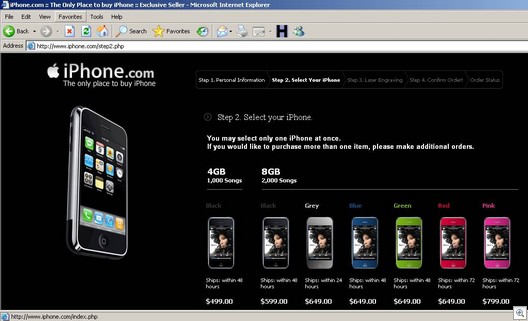
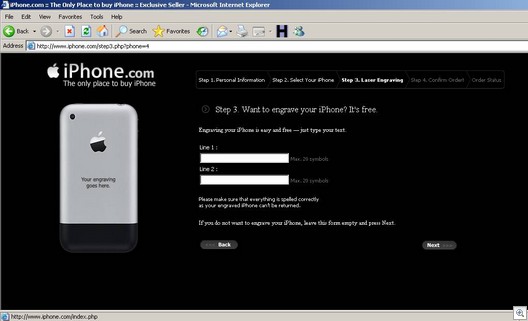
So if we were to go ahead and place an order, we would see this: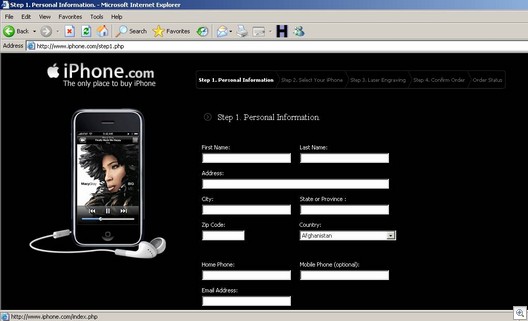
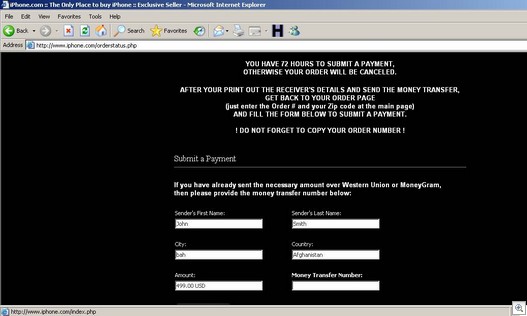
Our order status is pending and now we have to send payment via
So there you have it: A trojan that spawns a fake popup for an iPhone, using a BHO to redirect you to a fake iPhone.com. If you order this phone, you’re assuredly be contributing to lining the malware author’s pockets, and you can forget getting your iPhone.
Alex Eckelberry
(Credit to Sunbelt researcher Adam Thomas)