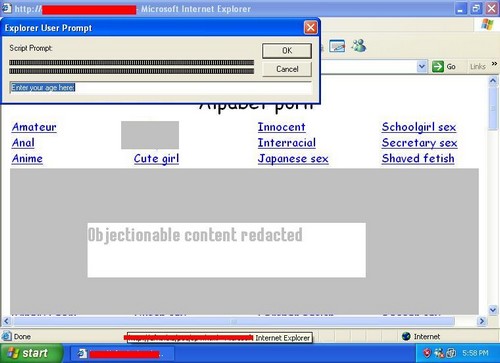
Recently, Microsoft listed a new exploit, IE Javascript Window() Remote Code Execution. eWeek discusses it here. CNET raises threat level here.
Take heed. This exploit attacks fully patched Windows XP systems and is quite nasty. The exploit looks something like this:
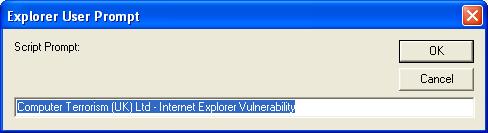
Monday, Sunbelt spyware researchers Patrick Jordan and Adam Thomas saw the first such instant of this exploit being used in the wild to download some really ugly spyware (we held off publishing the details of this exploit until after we gave Microsoft security researchers a full debriefing).
However, we are only seeing it in a limited number of very nasty spyware sites (professional researchers requiring more info can contact me).
We did a quick check with McAfee (JS/Exploit-BO.gen) and Kasperksy (Exploit.JS.CVE-2005-1790) and both detect this exploit. We haven’t checked other AV engines yet but I assume that most have detections for it. Obviously, having updated AV definitions is a must.
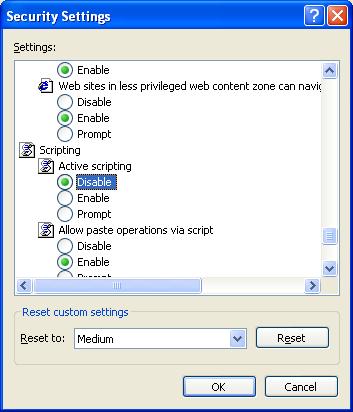
Another way you can secure yourself against this nasty is to turn off Active Scripting in the Internet Zone:
So here, in all its glory, is a real live nasty spyware infestation occurring on a Windows XP SP 2 system. I simply went to the site and was off to the races.
(Sorry for the edits, but the content of this page is pretty raunchy).
At any rate, it’s now confirmed, in the wild and two things MUST happen:
1. Microsoft must patch exploit immediately.
2. Get your security essentials in — at the very least an AV product. Tight on cash? Read my article, Security on the Cheap, here.
Alex Eckelberry