MS security response blog entry:
Based on our investigation, this exploit code could allow an attacker to execute arbitrary code on the user’s system. We also want you to know that we’re aware that this vulnerability is being actively exploited. Thus far the attacks appear targeted and very limited. We’ve actually been working on an update that addresses this vulnerability and our goal is to have it ready for the October release, or before if we see widespread attacks.
Link here.
Advisory 925568:
• In a Web-based attack scenario, an attacker could host a Web site that contains a Web page that is used to exploit this vulnerability. In addition, compromised Web sites and Web sites that accept or host user-provided content or advertisements could contain specially crafted content that could exploit this vulnerability. In all cases, however, an attacker would have no way to force users to visit these Web sites. Instead, an attacker would have to persuade users to visit the Web site, typically by getting them to click a link in an e-mail message or instant messenger message that takes users to the attacker’s Web site.
• An attacker who successfully exploited this vulnerability could gain the same user rights as the local user. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights.
• In an e-mail based attack of this exploit, customers who read e-mail in plain text are at less risk from this vulnerability. Instead users would have to either click on a link that would take them to a malicious Web site or open an attachment to be at risk from this vulnerability.
• By default, Internet Explorer on Windows Server 2003 runs in a restricted mode that is known as Enhanced Security Configuration. This mode mitigates this vulnerability because Binary and Script Behaviors are disabled by default in the Internet zone.
One workaround:
Microsoft has tested the following workaround. While this workaround will not correct the underlying vulnerability, it helps block known attack vectors. When a workaround reduces functionality, it is identified in the following section.
Note The following steps require Administrative privileges. It is recommended that the system be restarted after applying this workaround. It is also possible to log out and log back in after applying the workaround however; the recommendation is to restart the system.
To un-register Vgx.dll, follow these steps:
1.
Click Start, click Run, type
regsvr32 -u “%CommonProgramFiles%Microsoft SharedVGXvgx.dll
and then click OK.
2.
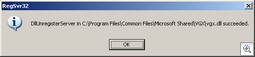
A dialog box appears to confirm that the un-registration process has succeeded. Click OK to close the dialog box. If successful, you’ll get a dialog like this:
Impact of Workaround: Applications that render VML will no longer do so once Vgx.dll has been unregistered.
To undo this change, re-register Vgx.dll by following the above steps. Replace the text in Step 1 with
regsvr32 “%CommonProgramFiles%Microsoft SharedVGXvgx.dll
9/20 revision: See revised update here.
Full Microsoft advisory link here.
On a side note, we were a bit surprised to find out that ISS apparently has had information on this exploit for some unknown period of time, but was working with Microsoft on the issue and today issued an advisory. Their thinking was that this was a responsible disclosure issue, which I understand. We discovered this exploit in the wild at around noon EDT yesterday and posted the code to a closed and vetted security list to start the research process — and this was the first that anyone in that security community had seen or heard of it. Whatever.
Alex Eckelberry