Over the past several months, researchers have seen a small number of phishing attempts taking advantage of a feature in older versions of IE called MIME Sniffing. It’s a weak attempt to bypass spam and phishing filters, by having a non-HTML link in an email.
It’s a pretty dumb hack, frankly. But it’s mildly interesting to observe.
Basically, a phisher takes advantage of a vulnerability in IE versions 4 through 7, where you can have the web server tell the browser that the content type is a particular type of file (jpg, png or gif), but actually render an HTML page (or whatever else).
What’s happening is that IE is “correcting” what it assumes is a mistake. The technique is explained in detail in this Heise article (thanks DJ).
Today, I saw an interesting phish, with the following URL:
acceghsh.nxt.ru/img/6.jpg?nin.ey.it/ws/e$ISAPI.dll?Sign&ru=http%3A%2F%2Fwww¬.it%2F
Or more simply,
acceghsh.nxt.ru/img/6.jpg
(the text string after the ? being simply garbage made to look like a querystring).
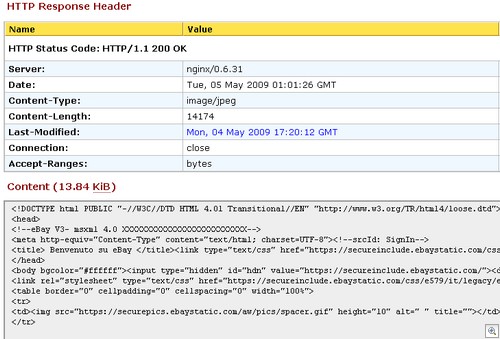
So, let’s use a simple tool like web-sniffer to see what’s going on here:
As you can see on the top of the screen, the server is telling the browser that it’s a JPEG file. But when we look at the content, it’s HTML.
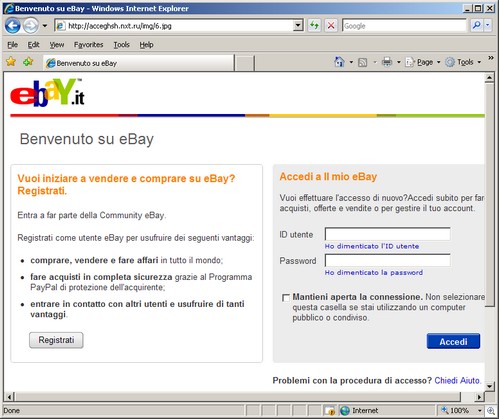
And IE 7 will render it as HTML, because it’s assuming the web server made a mistake, and is correcting the “error”:
Nifty, eh?
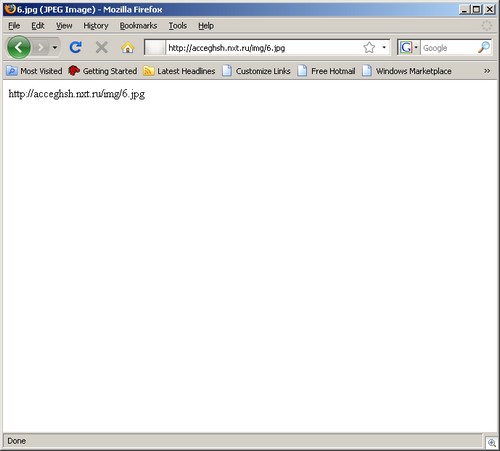
Let’s take a look at the same page in Firefox:
This whole MIME sniffing thing has been handled in IE 8. It’s the older versions of IE that display the page incorrectly.
Alex Eckelberry
(Hat tip to N)