Alas, the news was published on April 1st. But it is not a joke.
Curious, I spent a bit of time today researching it (when I really was supposed to be doing other things), and while the “lizamoon” url is down, there are still a number of other URLs active on this one.
Without a lot of effort, I found infections using other URLs, which include
t6ryt56.info/ur.php
tadygus.com/ur.php
milapop.com/ur.ph
books-loader.info/ur.php
(These are all malicious, so obviously don’t go to them unless you know what you’re doing, etc.)
However, I doubt the infection is as massive as is being stated. For unique sites, perhaps a few thousand. More pages than that, but in terms of unique domains, not a million, as might have been inferred from articles.
What’s curious is I found something else that was interesting — encoded View State with malicious URLs injected into the site.
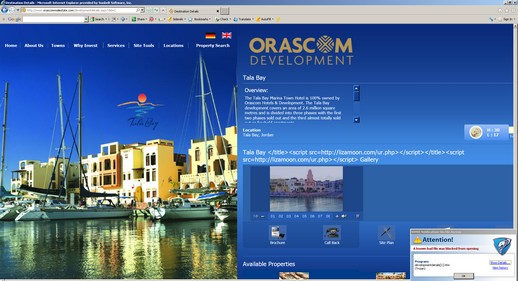
For example, here’s a screenshot of an example encoded View State that I found on one of the injected sites.
First, an infected page (with VIPRE yelling away that there’s a problem in the corner — sorry, can’t help the shameless self-promotion).
So let’s take a look at the page source:
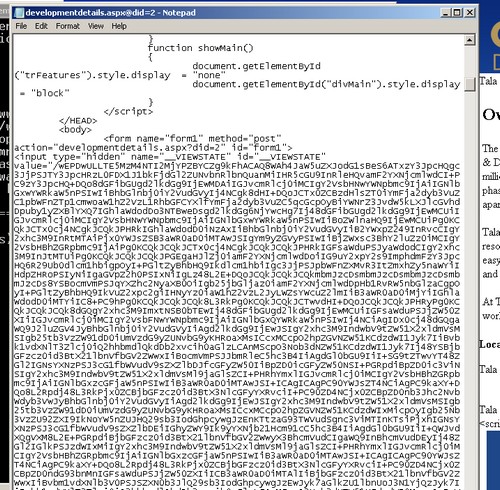
Yuck! What’s all that? It’s encoded View State.
So we go to a handy-dandy decoder, paste the offending text, do a little “where’s Waldo” and there you have it:
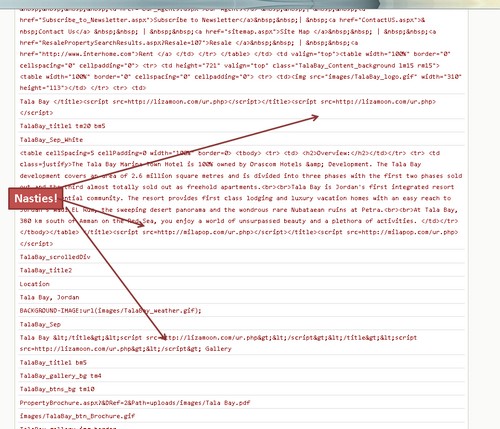
How cool is that?
And yes, that is really painfully sloppy stuff.
Alex Eckelbery
(Obligatory hat tip to Jose)
