We have not seen any cases of this exploit in the wild, but there’s a proof of concept at the Secunia site and it’s something to be aware of.
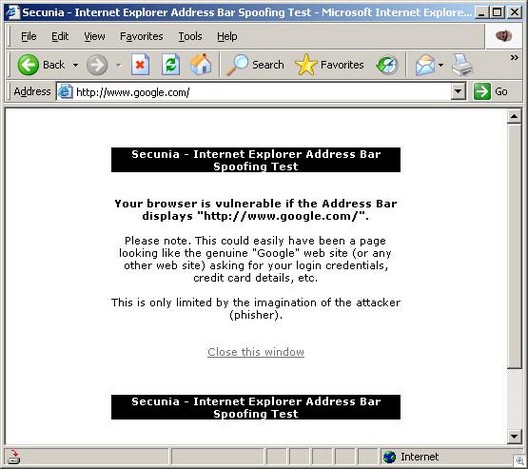
There is a new exploit which allows hackers to obfuscate the real URL being shown, useful for phishing attacks. This is a practice called address bar spoofing, and enables the hacker to make an address bar show a different URL than what is actually loading. This particular exploit creates a race condition between a Macromedia Flash file and web content being loaded.
In a test available at Secunia, Google is showing, but the page is different:
The way to mitigate this exploit is to turn off active scripting, which is also a valid mitigator for the currently active “createTextRange()” vulnerability (in fact, turning off Active Scripting in general is a very good idea, if you can handle the hassle).
Suzi over at Spywarewarrior told me that she had success mitigating the exploit by simply setting “Allow sub-frames to navigate across different domains” to Disable (or Prompt). Screen shot below:
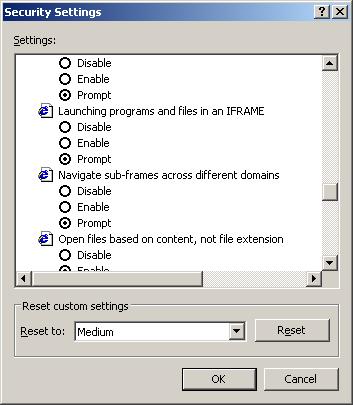
I tested this fix and it works on this test case, but there are no guarantees. Disabling Active Scripting is your best bet.
Secunia advisory here via CNET.
Alex Eckelberry