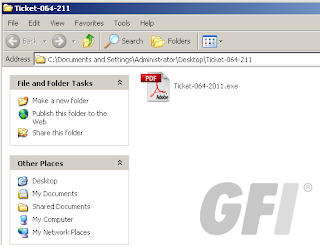
Our engineers over at the AV Labs have spotted recently a deluge of spam about a “traffic ticket” that purports to come from a state department in New York. The said spam has a compressed file attachment that, once extracted, contains a file that bears the icon of a normal Adobe .PDF file. Mimicing file icons, of course, is a common tactic used by criminals to appease any doubts or worries from recipients of such emails, which are actually malicious in nature.
“The malware appears to be sent from a botnet of unknown origin.” says GFI Spyware Researcher Adam Thomas.
When this supposed .PDF file is “opened,” it connects to sfkdhjnsfjg(dot)ru (a server in Ukraine) to download and execute the file, pusk3.exe. This .EXE file, detected as Trojan.Win32.Generic.pak!cobra, is a dropper/downloader. As of this writing, it drops/downloads a rogue AV and TDL rootkit variants.
CNN has written an article about this ticket spam early last month. Seeing that it’s still getting attention, we can surmise that it still is very much at large.
VIPRE users are already protected from ever accessing and downloading interesting “goodies” from the .RU site. And you can protect yourself from nasty attachments pretending to be something else by enabling file extension names of all files on your system. It’s a simple thing to do, yet it can save you from computer security disasters.
Jovi Umawing (Thanks to Adam Thomas for the analysis)