A while back, Cassava Enterprises asked us to remove detection of one of their products, CasinoOnNet, from CounterSpy’s detection database. (Cassava Enterprises is a Gibraltar-based company that operates a number of online gambling web sites and makes and distributes software applications that allow customers to access and use its online gambling services. These gambling applications include CasinoOnNet, PacificPoker and ReefClubCasino.)
As is our practice, we subsequently performed an exhaustive review of their installation practices; methods of system reconfiguration; data collection, transmission and sharing practices; and notice, disclosure and consent.
Our conclusion was that, in fact, Cassava’s installation practices trip several of Sunbelt’s Listing Criteria, specifically in the areas of “Distribution and Installation” and “Notice, Disclosure, Choice and Consent”.
However, at the time Cassava submitted its request for a software review to Sunbelt, CasinoOnNet was classified as “Adware,” with a threat level of “Elevated” and a default action of “Quarantine.” Given the non-intrusive functionality of CasinoOnNet (as well as Cassava’s other gambling applications), this classification was unwarranted.
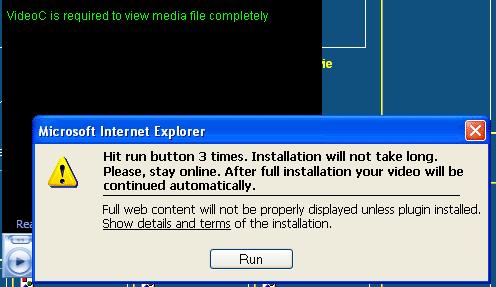
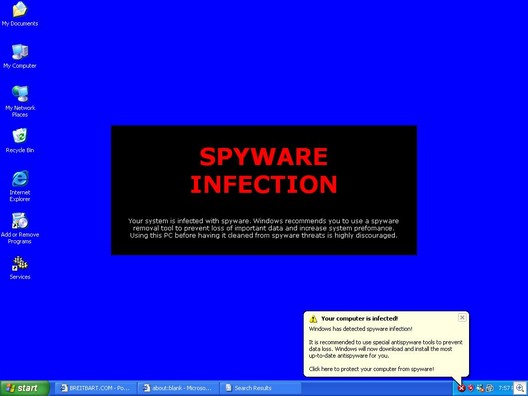
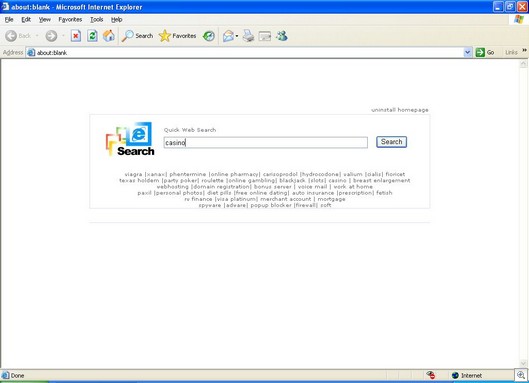
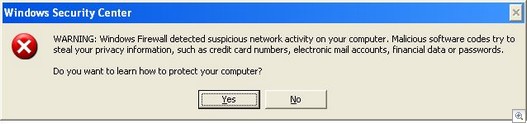
Nonetheless, Cassava’s unacceptable installation practices do make Cassava’s gambling applications a legitimate detection for Sunbelt to offer its CounterSpy users and customers, given that these installation practices make it possible that users could have unwittingly installed one of Cassava’s gambling applications.
In addition, CasinoOnNet was the only gambling application from Cassava to be detected by Sunbelt’s CounterSpy anti-spyware application (setting aside cookies). There are two others that also trip our listing criteria: PacificPoker and ReefClubCasino.
Thus:
1) We have reclassified CasinoOnNet as a Potentially Unwanted Software, with a threat level of Low and a default action of Ignore. (A default of action of “Ignore” does not mean that CounterSpy will not detect an application. It simply means that the choice of removal is left up to the user, as opposed to the program automatically offering to remove or quarantine an application.)
2) We have revised the description of CasinoOnNet in the CounterSpy database to more clearly define the characteristics and behavior of the program.
3) We will also add Cassava’s other gambling applications (PacificPoker, ReefClubCasino) to the CounterSpy database and handle these other applications in the same manner as CasinoOnNet.
In reclassifying Cassava’s gambling applications as “Low risk,” Sunbelt can continue to offer these detections to users, while still requiring users to affirmatively elect to remove Cassava’s gambling applications by changing the selected action in CounterSpy’s scan results from “Ignore” to “Quarantine” or “Remove.”
As a result of our classifications, users who knowingly installed Cassava’s software can continue to use the software without fear that it will be removed by default by CounterSpy, while users who want to remove the software can do so.
A full writeup from our research center is available here.
Alex Eckelberry