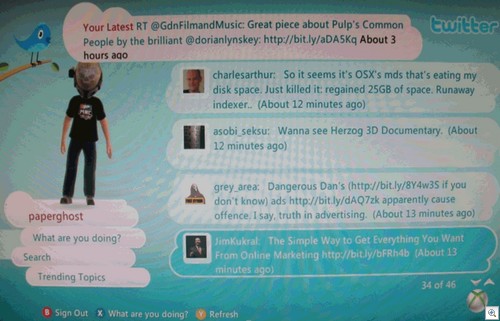
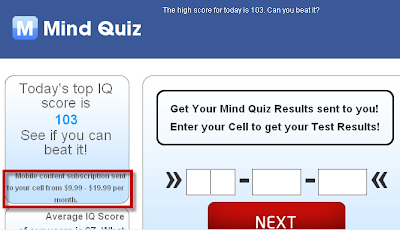
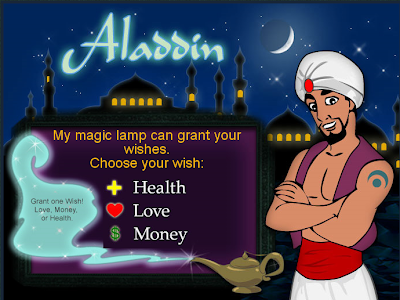
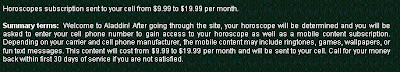
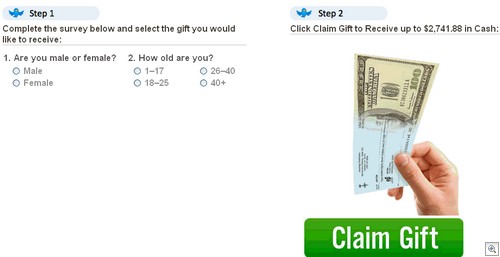
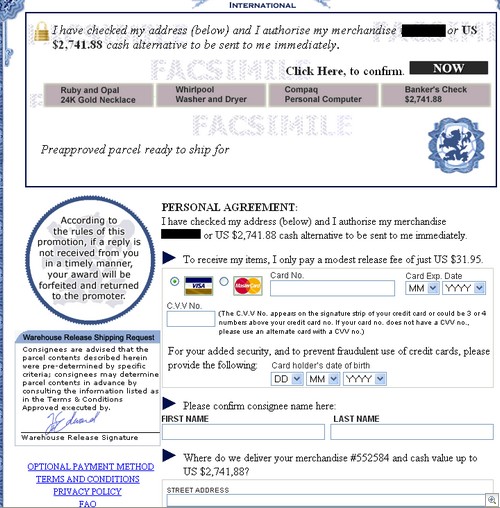
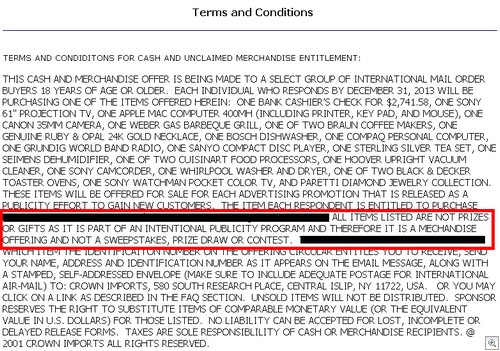
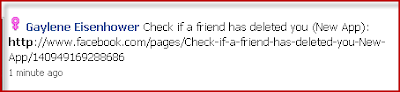
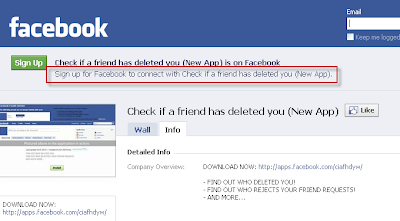
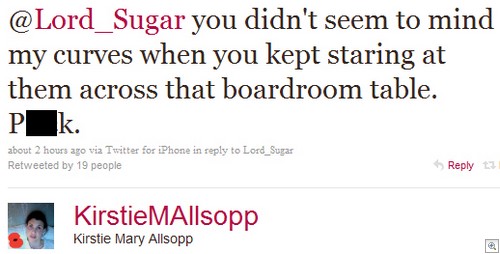
When it comes to Two Point D’oh, do you want to be like this guy:
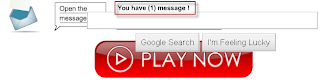
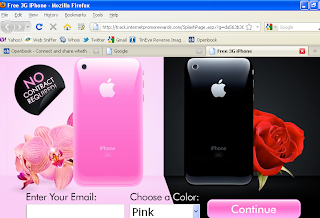
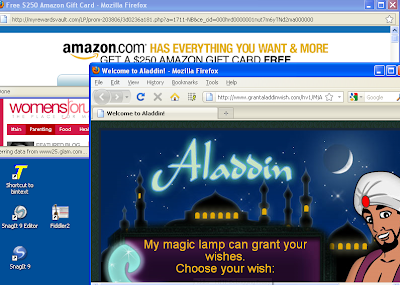
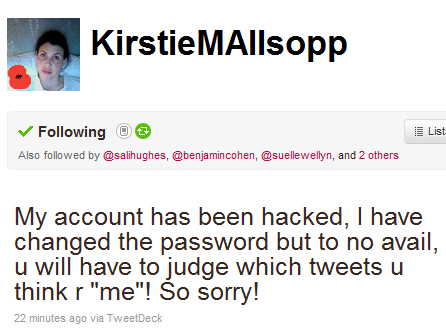
Or do you want to be like this guy:
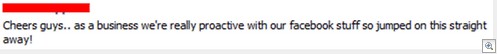
I think we can all agree that approach number one is the place to be. With that in mind, I recently gave some hints and tips at IRISSCON 2010 in relation to protecting your brand / company / employees from shenanigans. We have lots of business-centric sites such as Linkedin, Yammer, Present.ly, companies flocking to Facebook and employees doing their thing on Twitter. While you may not agree with all of the sentiments expressed here, I have to say that in my experience companies tend to focus on complaints, compliments and competitors in the 2.0 space while forgetting about our old pal “security”.
Here come the tips, feel free to add your own but I’ve found the below to be quite helpful in recent years…
What are we most worried about? For me, it’s malicious pages / profiles pushing badware in your name, unofficial pages from fans & well meaning employees, dodgy data gathering and compromised accounts. Additionally, geolocation services mean that it isn’t just employees throwing up a page connected to you being a problem anymore; depending on the service, any random individual can happily come along and stick you on a map, or a location service, or a ratings portal.
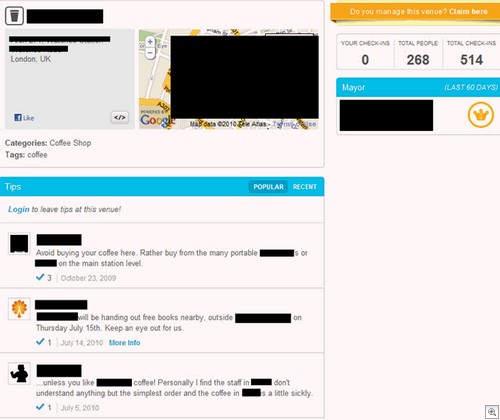
1) Think Facebook Places, Foursquare – do you have an official page there? Is there a page “in your honour” with comments filling it up?
Here’s one with people not only complaining about the quality of coffee on offer, but also slating rival firms. We all know how grumpy companies can be where random accusations of awfulness are concerned; better to engage, hit that “Do you manage this venue? Claim here” button and talk to people.
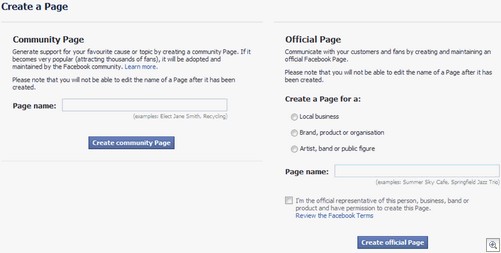
Similarly, you should go check out Facebook and create a brand presence there before some scallywag starts pimping viagra and fake handbags from “Your Company INC”. Hit the “Create a page for my business” button at the bottom left side of any Facebook page, then start filling in the blanks.
Additionally, claiming your spot on Facebook places is easy – if you’re in the US, follow this handy guide. If you’re in the UK, I believe it is much the same procedure except they phone you up and you give them a PIN number along with the usual paperwork. Apart from the more obvious sites, be aware that plenty of other services exist and even Yelp is getting in on the act. Finally, here’s some advice in relation to setting up on Foursquare.
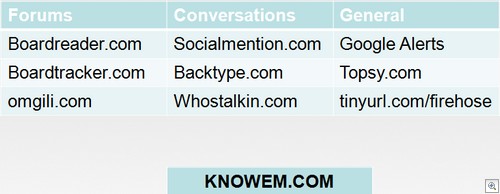
2) A common problem: how do you dig through all of those sites to see if anyone is up to Internet shenanigans with your good name? Easy, you load up this collection of websites and start digging:
Two things to note: many “social discussion / conversation tracker” sites will claim to pull up results from across the web, but in my experience only ever give you pages of results from Twitter. Your mileage may vary with those, but the ones listed seemed to serve up information from a variety of sources. The forum trackers are particularly useful if you suspect individuals of performing random drive-by spam on sites with your name plastered all over them. I know one person whose company was targeted by such a campaign and the forum search portals were great for getting Admins to hose the spam quickly.
Knowem.com is a favourite of mine, as they they allow you to search for your name / brand on lots of social networking sites for free, which is extremely useful from a security perspective (they will also register you on those sites for a fee).
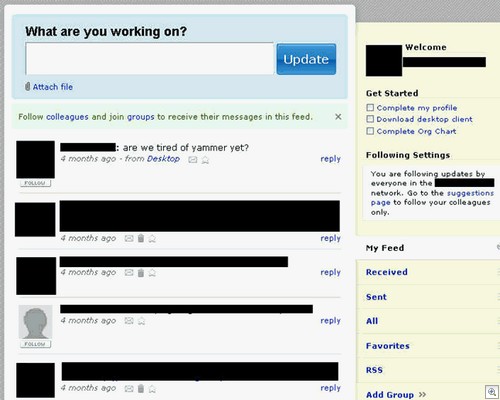
3) If your company has a Yammer account, put someone in charge of making sure the account isn’t left lying around with lots of data posted to it:
“Last post: four months ago”? Whoops. There’s always the danger that we might sign up to a hot new service only to get bored and abandon it completely a few months later. But what about the data posted – is someone ready to go in and hose the lot?
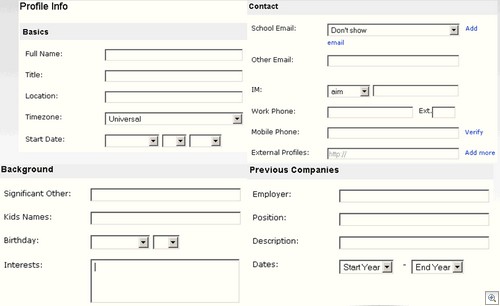
While you’re at it, consider coming up with a few basic policies in relation to how much personal info you really need in your account:
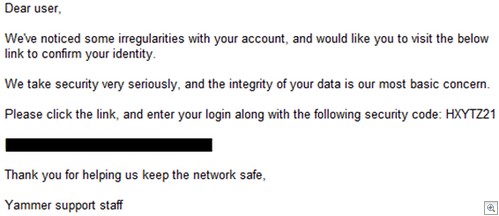
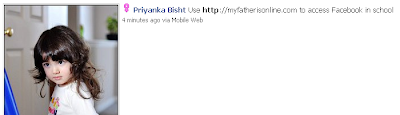
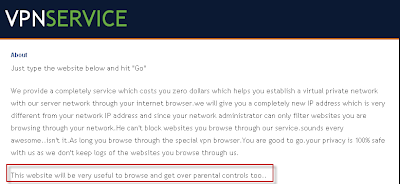
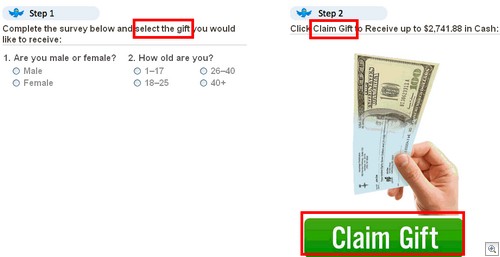
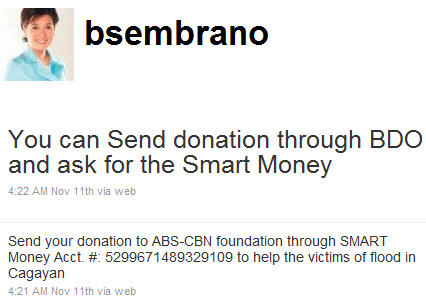
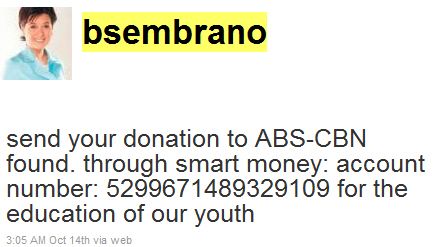
Just think: if “Employee A” falls for a phish mail like the one below, the phisher has access to all of the information posted to your internal wall AND any information posted about themselves in the profile. A lot of said information could easily be password reset clues to other services they’re registered with, which makes things worse.
Finally, you should ensure ex-employees can no longer access your Yammer portal, especially if they’re one of those angry disgruntled chaps determined to grab a bunch of “secret” information six months down the line and paste it all over the internet.
4) If you’re hip and trendy – and we know you are – you might be tempted to stick a videogames console in the office recreation room along with the pool table nobody uses and the broken basketball hoop in the corner. We gave a survey to 200 senior IT decision makers in both public and private sector organisations around the globe. The results? 4 in 10 had no idea of the problems posed by consoles, 8 in 10 kept no record of who was using said consoles and 49% of them had a console in the workplace (with 44% of them connected to the net).
Just think, you’ve locked down your social networks in the workplace. You have granular controls to allow or deny individual applications on Facebook. You have an elegant compliance solution in place to ensure nobody is posting sensitive work information to Twitter.
Then I stick my console on with a bunch of Twitter / Facebook / Last.fm apps built in and OH NO IT’S ALL GONE WRONG SOMEHOW.
Hear that? It’s the sound of your carefully thought out network controls flying out the window. While links aren’t clickable on an XBox so there’s no danger of infections via Twitter, it’s worth noting that you may well find your boss walking in and wondering why the Last.fm application has a picture of a popstar with their “modesty” shaking all over the screen via a user uploaded photograph.
Do you have an XBox Live account bearing the company name? Keep in mind people record game sessions and upload them to Youtube – you might find your employee swearing loudly at the 14 year old Halo master that spent the last half hour shooting him in the face. Bit embarrassing, that one.
This is also a good reason why you should keep track of who is using the console, in preparation for “Sweargate” or other similar gaming kerfuffles. In fact, given the wide range of ways people want to mess with you in console land you might not want to put the thing online in the first place. As strange as it sounds, the many parental controls available on consoles may well be useful in terms of locking things down a bit. For example, if you want to be really watertight on the “Who used it?” issue, enable the XBox Live Passcode and change it after every use.
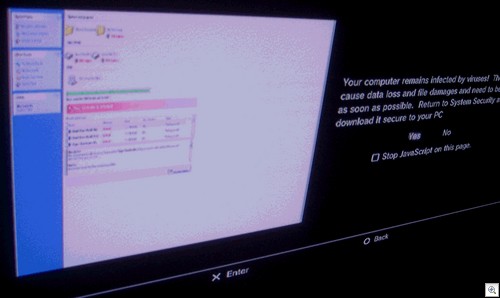
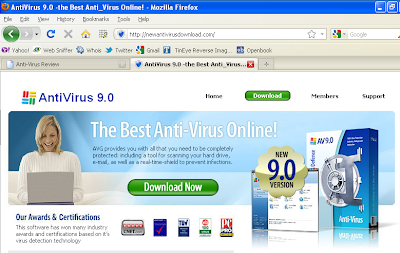
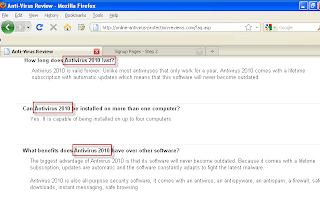
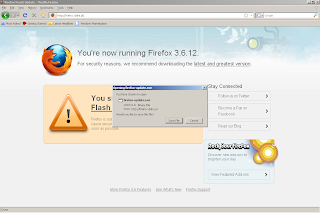
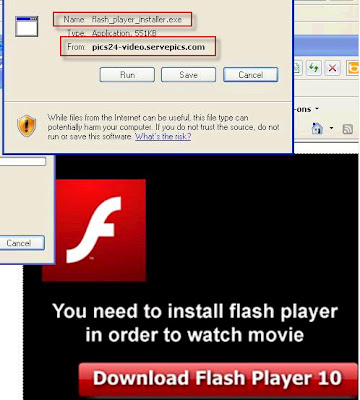
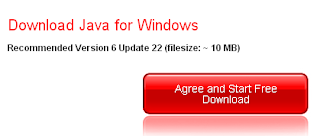
One final thought – the Playstation 3 has a built in web browser, which takes a decent stab at rendering websites. An interesting side issue? A Fake AV site which looks like this on your PC:
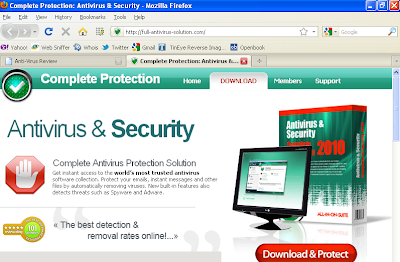
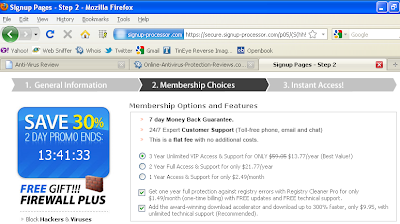
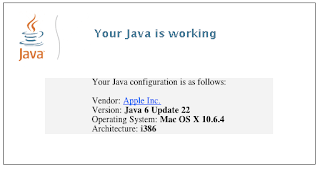
…will look something like this on your Playstation:
Note the “virus warning” down the right hand side. Yes, I know it says “computer remains infected” and not “games console”. But given that so many people don’t really think about these problems where consoles are concerned, it’s not surprising that I know of at least one case where a similar “warning” ensured an IT guy spent about three days messing around looking for a non existent network infection.
What’s written above certainly isn’t everything I covered at IRISSCON, but hopefully there’s a few things in there to get you thinking about some areas of day to day networking that need to be considered.
Christopher Boyd