Scammers who don’t appear to be native speakers of English, are trolling for Battle.net passwords with a spam campaign. The spam emails contain messages that appear to be invitations to an “event.”
Battle.net is Blizzard Entertainment’s online service on which vast numbers of members play Starcraft and World of Warcraft. These are games in which characters have teeth like 400 pound Shih Tzus, VERY improbably hair styles and weapons that make top-level Pentagon officials salivate. Blizzard has been saying World of Warcraft has “more than 11 million” monthly subscribers for about two years now.
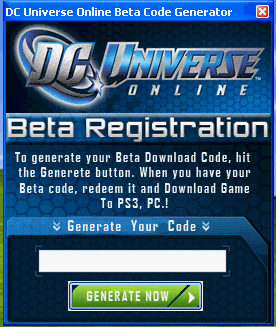
“Blizzard billing Cataclysm will support in the near future, thanks for users of Blizzard, we have an event as long as you participate in the opportunity to participate in the Cataclysm CDKEY use Activation, you use the following link to obtain the user login…”
Ok. Well, that isn’t the way you use commas in real English (or words either), but we’ll follow the link anyway. (Kids, don’t try this at home.)
Ah yes, just a few letters off from the real thing:
And the phony Battle.net site domain was set up when? Oh! Today!
Whois Record
Registrant Contact:
Ji XiaoWei
xiaowei ji
+86.5787245132 fax: +86.5787245132
LiShui Dengtalu 25
LiShui Zhejiang 323700
cn
. . .
DNS:
ns1.4everdns.com
ns2.4everdns.com
Created: 2010-08-11
Expires: 2011-08-11
A spam troll using a similar site using “battrlie.net” was blacklisted several days ago.
Domain name: battrlie.net
Registrant Contact:
Ji XiaoWei
xiaowei ji
+86.5787245132 fax: +86.5787245132
LiShui Dengtalu 25
LiShui Zhejiang 323700
cn
. . .
DNS:
ns1.4everdns.com
ns2.4everdns.com
Created: 2010-08-06
Expires: 2011-08-06
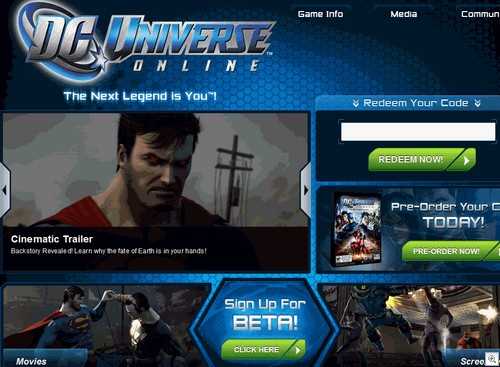
And if you don’t have a real Battle.net account, the “create account” button on the phony site takes you to the REAL Battle.net site so you can set up a REAL account and THEN the scammers can steal it.
Thanks Douglas. Thanks Wendy.
Tom Kelchner