The short answer is “no, although Windows 7 is probably a little safer.
That being said, there are a number of security measures that apply to any operating system, that are vital to a layered defense. Windows XP is only a secure operating system if it is updated regularly and operated by users who have some understanding of Internet security. Below are the four vital security practices to go with Windows XP:
1. Install operating system and application updates promptly.
Malware that exploits newly discovered vulnerabilities begins circulating within days, if not hours, of the public disclosure of those weaknesses. Patches (or workarounds) are generally issued as quickly as the software company can deliver them. There may be significant delays. The dark side often is ahead of the curve with “zero-day” exploits, those that take advantage of previously unknown exposures. It is vital that patches are installed as soon as there are available.
The most important updates will be those for the Windows operating system, Adobe applications, Microsoft Office and Internet Explorer or other browsers. These are the most commonly used things on computers worldwide, thus the most widely available and cost-effective targets of malicious operators.
The number one cause of compromised machines is lack of current updates. Microsoft issues patches on a regular basis on the second Tuesday of each month. (Information here.) Adobe has begun issuing updates on the same day.
2. Updated anti-virus applications are your first line of defense.
Having a good anti-virus application running on desktop machines and network can protect the small enterprise from a vast number of threats, including the most recent ones: banking Trojans, rogue security products and bot-associated malware.
Very small businesses with a few machines probably need little more than VIPRE desktop installations and possibly the Sunbelt Personal Firewall (Sunbelt info here.)
Small, medium and large businesses with Internet-facing networks might consider VIPRE Enterprise. (Sunbelt info here.)
VIPRE can stop previously unidentified malware by using MX-V advanced “behavior-based” scanning to spot its malicious behavior in a virtual environment before it infects the machine.
3. To add one more layer of defense, enterprises should consider doing online banking from a dedicated machine that is isolated from networks and not used for any other purpose (especially the exchange of email.)
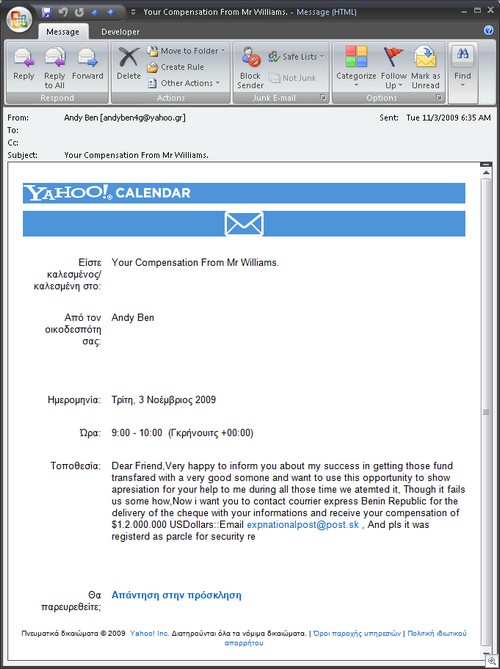
Many of the banking Trojans that were used to illegally transfer $40 million from the bank accounts of small- and medium-sized businesses in the last five years were installed when someone clicked on an attachment or malicious link in an email. (Story here.)
Also in the last few years there have been numerous spear-phishing campaigns targeting company financial personnel whose machines are used to log onto online banking sites. In some of these, the banking Trojans or their downloaders arrived in email messages with malicious attachments disguised to look like legitimate accounts-receivable correspondence.
4. Providing employees with computer security training can reduce the risk of attacks based on social engineering.
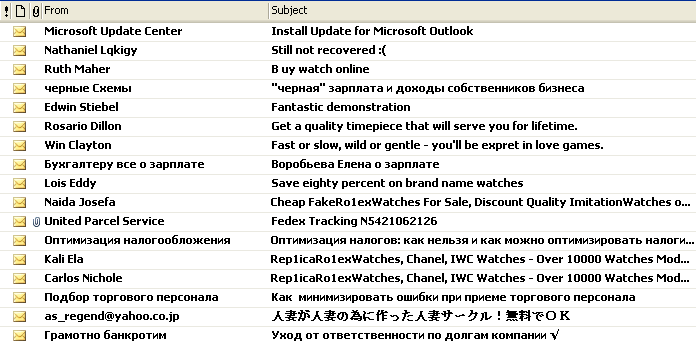
Every day an uncountable number of people are using the Internet for the very first time. Unless they have some kind of instruction, they will quickly fall victim to social engineering gimmicks. These trigger malicious applications that arrive by email or are downloaded from hacked or malicious web pages. New scams begin circulating almost on a daily basis and are aimed at millions of users through email spam originating in botnets or hacked social networking accounts. Employers need to educate employees, especially new ones, about Internet safety and give them a way to keep up with new threats.
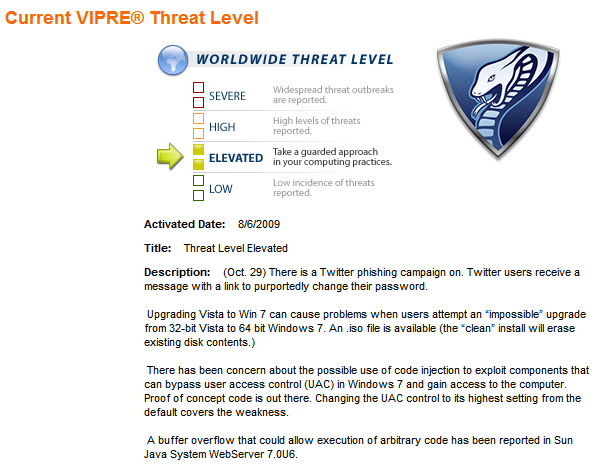
The Sunbelt Blog and the threat index on the VIPRE agent interface provide daily updates on the threat landscape for experienced and inexperienced Internet users.
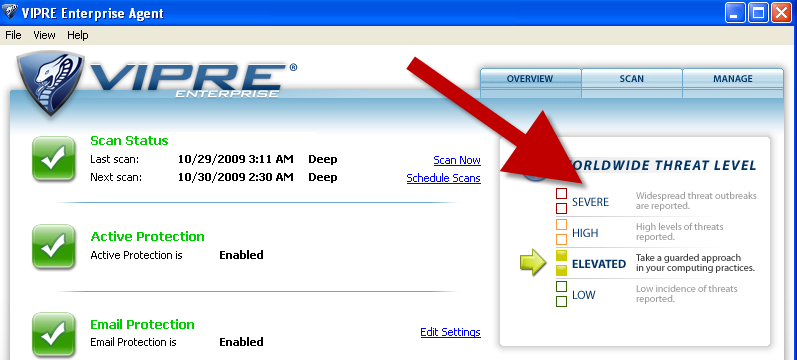
Double clicking on the Threat Index graphic takes users to the Sunbelt web site and a description of the most current threats that are making news:
White papers on security
On the Sunbelt web site, we also have white papers, some written for inexperienced Internet users, in the Sunbelt Research section.
Two of them, especially written for new users are:
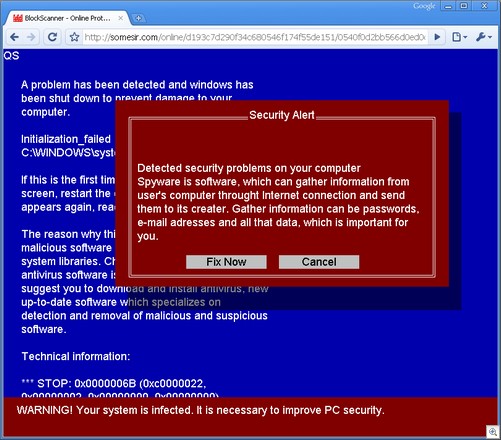
“How to Tell If That Pop-Up Window Is Offering You a Rogue Anti-Malware Product”
“What’s in your spam bucket?”
Thanks Stephen in Victoria, BC, Canada, for asking.
Thanks Alex
Tom Kelchner