It’s become the latest craze in security blogs — show how search for a celebrity or current event leads to malware through Google searches.
I’ve done it myself, quite a bit. And I do think it provides a public service.
But the reality is — it’s massive, it’s constant, and the search terms are all over the place.
For example, there is a current blackhat run on Google that is using a dizzying amount of search terms. Here’s a list of terms that I’ve found. There are more.
2010 Military Pay Charts
Aileen Quinn
Amelia Earhart
Anglicanism
Arsenio Hall
Astate
Banco Del Tesoro Venezuela
Bedava Ingilizce
Bianchini .
Bitty Schram Fired
Black Parade
blackberry storm 9520
Blast Off
Bobblehead .
Bravo project runway .
Cafe World
cfnm youtube
Charlie Manuel
child stuck in balloon
Chris Cooley Blog .
Chris Mckendry
Christian Audigier
Collin Wilcox Paxton
Collin Wilcox Paxton .
Comcast Tickets
Cookie Johnson Jean Line
Crucisatorul Potemkin
Daniel Maldonado
David belle parkour video
Deadspin Espn
Dining
Dodsworth
Donovan House Washington Dc
Download Windows 7
Droid Does
Ed Hardy
Electron configuration berkelium
En Clown I Mina Kl??der .
Facebook Live Feed Vs News Feed
Fagacious
Fbi 10 Most Wanted
Female snake charmer costume
Figure roller skating .
Florida Sex Offenders By Zip Code .
Folkston Ga
free porn tube 8
Funny halloween pictures
Gardien
Glee Episode 9 Preview
Gossip Girls .
H1n1 Vaccine Canada
H1n1 Vaccine Side Effects
Halloween Escape Walkthrough .
Hardgame2
Hide Away
Honda Center Anaheim
House Season 6 Episode Guide
Hulk Hogan
Jay Mohr
Jayson Werth Married
Jeff Dunham Tour Dates 2009
Jeffrey Chiang Texas
Jodie Sweetin .
Joe Klein Obama Thesis
Jonathan Broxton
Künstler Cutlery Knife Set By Connoisseur .
Kyrie Irving Twitter
Levi Jones
Lil Wayne Pleads Guilty
Lindsay Lohan E Namorada .
Losing It With Jillian Michaels
Marine Corps Marathon
Marni Phillips Photos
Married With Children .
Matthew Shepard Story
Mikelle Biggs
Min Lieskovsky .
Natalie Portman
New York Yankees
Obama thesis paper
Once Bitten Movie
Organic Baby Food Recall .
Orionids Meteor Shower
Patchwork Nation
Phillies
Phish Tickets
puerto rico explosion
Rajon Rondo Ripped .
Rebel Efi Crack
Secret Girlfriend Wiki
sharona monk
Somewhere Else
Sommer Thompson Missing
supernatural season 5 episode guide
sweetest day 2009 .
The Bunny Ranch
The Jeff Dunham Show
The Perfect Storm Movie .
The Vampire Diaries 7
Tnmmu.ac.in
Tourettes Pete
Uss Freedom
Villisca Axe Murders Wiki .
Wachovia Center Philadelphia
Wapa Tv
Week 7 Football Picks
week 7 football picks .
When You Have No One No One Can Hurt You
Who The Hell Is Wolf
Windows 7 Free Upgrade For Vista .
Windows 7 Release Date
Winter Time
Wombat Day
Y94
Zac Hanson
Ladybugs Good Luck
40 Under 40 Fortune
Ali Kay
California City Element
hot pussy sex
International Paper Franklin Va
Jacksonville News
Jammers
Lil Wayne Going To Jail 2009
Metal Rayonnant
Obama Mit Speech
Path Accident
Psystar
Robin Thicke Wife
Shaq
Somer Thompson Missing
Using any one of these search terms will land you in trouble.
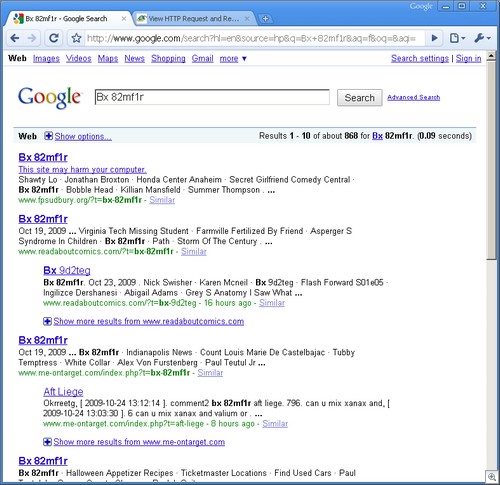
For example, let’s search for Bx 82mf1r:
First four hits are malware links, all compromised sites (the links only work with with Google as a referrer, going to them directly will just land you on a harmeless CNN page). You can see that Google catches the first site. The next three aren’t caught.
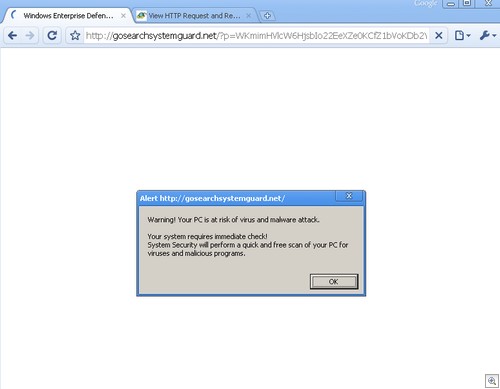
(Notice the /?p in the url? That’s generally the Windows Enterprise Defender rogue — thanks Patrick, for pointing that out.)
The rest of the search terms have varying degrees of success in getting to the first page of Google’s results. But in order to find them, we just do a little Google Dorking. Notice that all the malware sites use “/t” in the url. So, we just do a Google search, usingthe inurl operator to narrow down the malicious links.
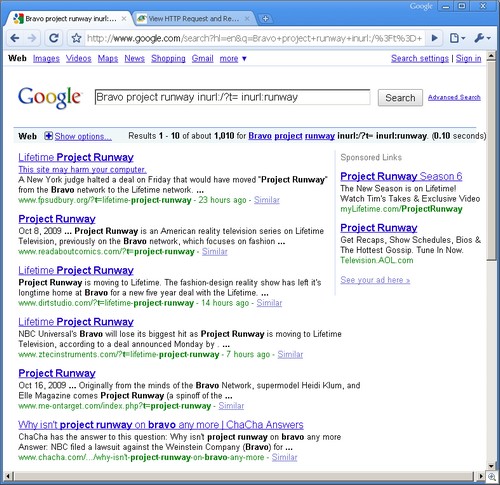
Hence, we might search for Project Runway with the following search command (just to get more malware links):
project runway inurl:/?t= inurl:runway
And we see all kinds of nasty stuff.
You get the picture. Blackhat SEO is alive and well on Google, contributing to the profits and merriment of both legitimante antivirus vendors and malware authors. Unfortunately, the user doesn’t come out that well in the whole thing.
Alex