I thought it might be useful to rip a little bit out of my HacKid presentation and post it here. The section in question deals with the most popular scams that are floating around in gaming land. If your kids avoid these, they have a very good chance of hanging on to their accounts, money and other assorted spangly things.
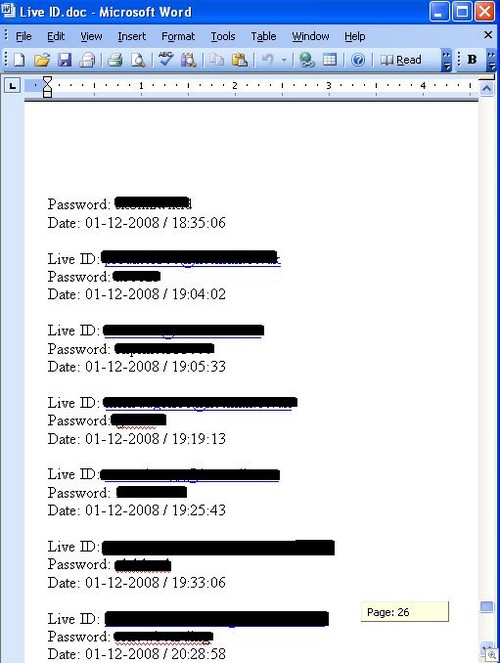
1) Phishing. Yes, I’m walking into Captain Obvious territory here but hey – it works. A typical collection of twenty seven pages worth of stolen logins will drink to that, and there’s plenty of room at the bar.
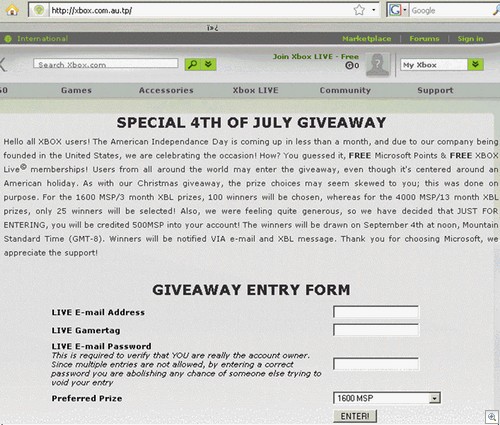
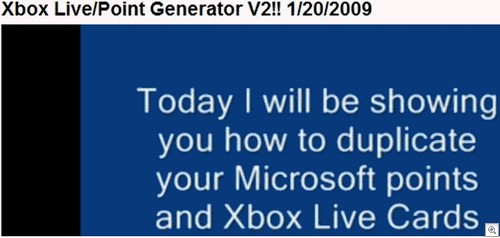
There’s a fair amount of national / public holidays coming up in many countries, and worth noting that there will be holiday themed phishes out there too. Microsoft do tend to get involved in regional deals during holiday seasons, so a carefully crafted fake email combined with a site such as the one below will work wonders:
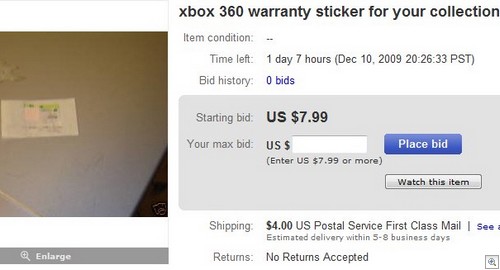
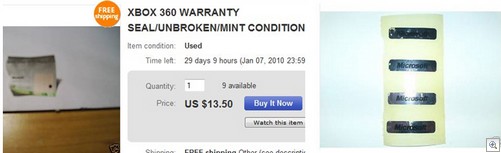
2) Used console sales. When people do naughty things with their games consoles, Microsoft hits them with the banhammer. Their expensive console is no longer able to play online, and is about as much use as a toaster. A lot of the various types of cheating means the scammer has to change parts inside the console, which of course breaks the warranty sticker in half.
What do they do? They jump onto EBay, and buy a bunch of warranty stickers “for their collection”.
I guess these replaced Pokemon cards. Anyway, they put the sticker on and take it back to the place they purchased it from – the shop may well put it back on the shelves, at which point some random person ends up buying a banned console.
Selling banned consoles is also a popular past time on EBay, so buyer beware – especially if the seller is called something like “Leetxboxhax0r” or whatever.
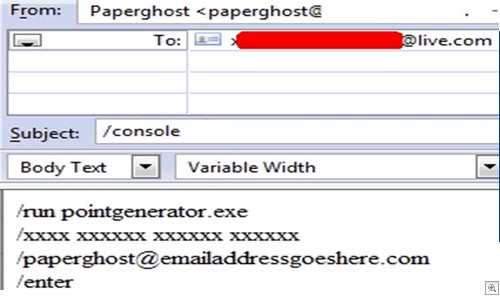
3) Fake programs. The staple diet of Youtube video watchers everywhere, fake programs have been around forever but seem to be particularly attractive to young gamers. I mean, they do look nice:
At best, your kid will fill in a survey (handing over a bunch of personal information to marketers) in return for a non functional program. Worst case scenario? The program will steal their login information, or dump infection files onto your PC and start trying to steal a whole lot more.
The other kind of fake program is the kind the scammer will tell you about, but not physically show you. They ask your child to send them information, or logins, or points that they’ve purchased legitimately so they can “double” them via some magical method only they know about.
If you bought your child 2,000 Microsoft points and they then send the scammer the redemption code, they won’t double anything – they simply enter the code themselves and keep the points.
Whenever you see a site claiming to have found a “glitch” in Microsoft servers, or a group of ex-Microsoft coders have come together to give you a bunch of freebies you can bet it is one huge scam. Example:

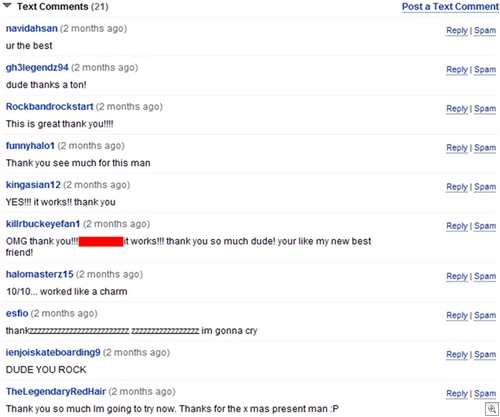
4) Big name, big target. You can set your watch to the fact that the moment a big name title is on the way, scammers will be all over it. Fake programs offering extra items, surveys to grant access to fictional Beta tests, phish mails that also promise Beta access…all of these scams will hit the ground running, usually driven by phony Youtube video campaigns (complete with the usual fake “This worked, yay” comments from Youtube users that are actually friends with the scammer).
Knowing that some users will be suspicious of freshly registered Youtube accounts singing their praises, the scammers will first steal a bunch of Youtube logins – the older the account, the better – which will look a lot more convincing to a younger user.
Additionally, we see Rogue SEO scammers pushing fake antivirus products focusing on searches related to specific elements of games (usually the most difficult ones). At that point, you could end up with programs on the PC you’d rather not want so extra caution is advised.
There are other ways of acting maliciously, of course – but the above examples are the ones I tend to see recycled over and over again. Feel free to throw in any examples you’ve seen doing the rounds.
Christopher Boyd