Earlier this week, I blogged about a site doing a bunch of different exploits, depending on what you are running.
One of the things the site will do is detect if you have Firefox, and attempt to exploit it, using the InstallVersion.compareTo() vulnerability.
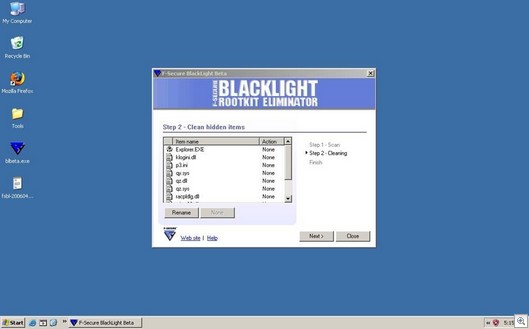
There are actually a number of sites running this exploit, and one of our researchers, Adam Thomas, was kind enough to take some pictures. Going to a site with an older version of Firefox got him just a bucket-load of spyware.
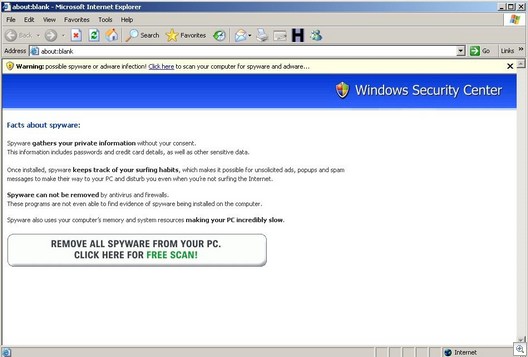
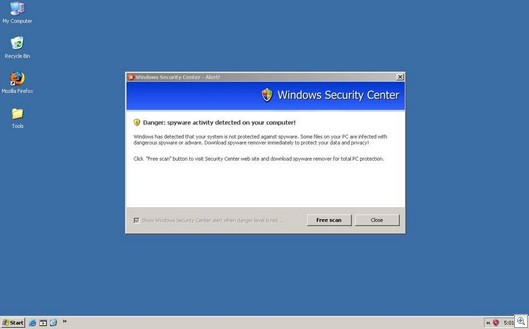
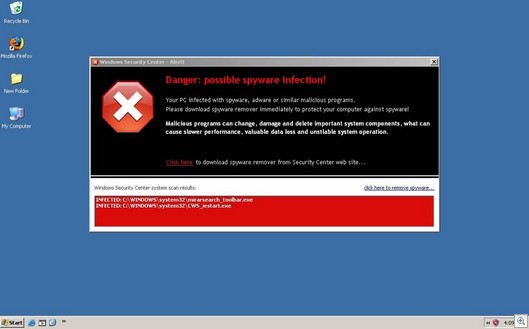
A Haxdoor variant was installed (seen above as detected by F-Secure’s Blacklight)… and a typical rogue-antispyware security install with a bunch of fake security messages.
Hijacked browser…
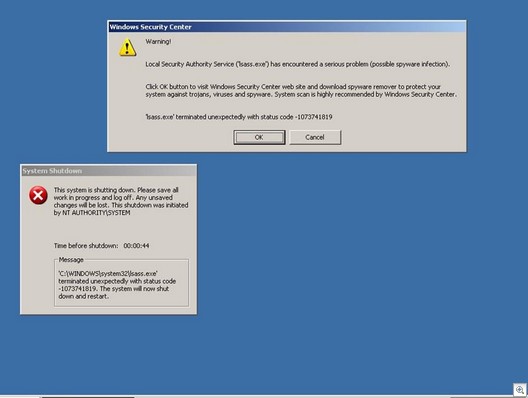
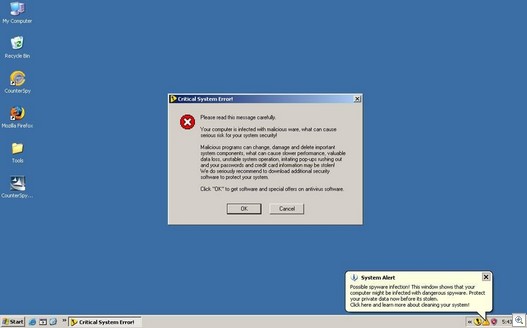
And this is nifty — there’s even this Local Security Authority Service pop-up message (above). Clicking OK aborts the system shutdown and…brings you to this page:
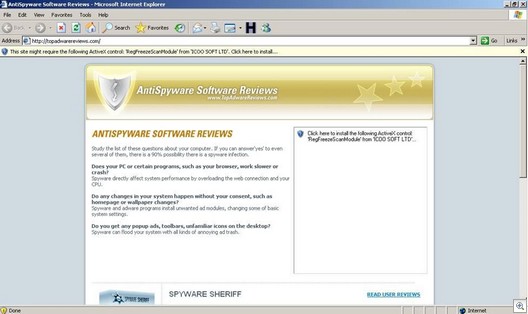
And you get the usual fake and hysterical security messages:
As a final dash of spice, the malware is redirecting attempts to navigate to security relates websites such as Kaspersky.com, Symantec.com, F-secure.com, etc.to Microsoft.com!
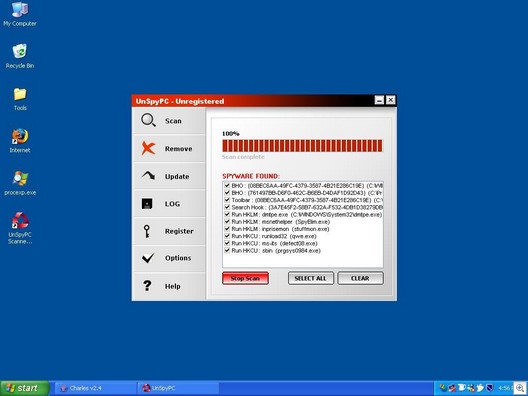
On another test system, Adam got UnSpyPC (a rogue antispyware application) and a Haxdoor install, among other things.
Now, the Faithful (and admittedly few) Readers of My Blog are demigods when it comes to security, so most of you are running a patched version of Firefox (basically, any version 1.05 or higher). But checking browser stats on this site does show that there is a very small number of you that aren’t updated to a safe version. Very, very few AV vendors detect this exploit, as you can see by clicking here.
Alex Eckelberry
(And, thanks again for the tip from some French friends)