For the past week, our Spyware Research team has been observing Raze Spyware being silently installed without user consent through various exploits. Raze Spyware is already a long time member of Eric Howes’ Rouge Anti-Spyware products list. Dubious installation methods are a common practice for these Rouge Anti-Spyware applications. To make matters worse, we have also found a fake keylogger being installed alongside of Raze Spyware! The program then alerts the user that they are infected with the “keylogger”. What is even more compelling was a transmission from the infected machine to Pills-Catalog.net that revealed a bot-net controller.
The WHOIS information from pills catalog shows very similar information:
RAZESPYWARE.NET
Registrant: painter co painter (
255 West 36 Street New York , NY 10018-7555
New York null,23878 US Tel. +212.3002000
PILLS-CATALOG.NET
Registrant: Pant Co Pant (
Colonnel By Hall A510
New York null,11201 US Tel. +91.2263475146
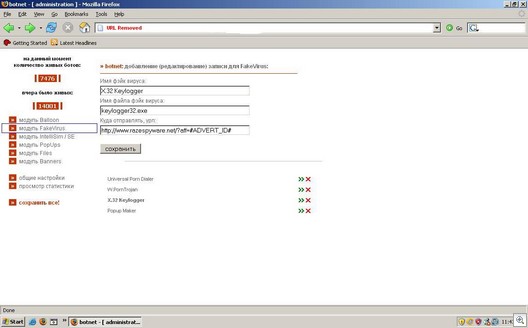
Shown below is the Bot-Net controller in action where you can upload or edit files (amongst other activities). Conveniently enough, we see keylogger32.exe which is the file that magically ends up in the WINDOWSsystem32 directory.
I think RazeSpyware has some explaining to do.
Adam Thomas
Spyware Research