Yesterday, Yair Amit of Watchfire Corporation gave details on an exploit that was found in Google.
Now, here’s what I like about this story: Yair found it and reported it to Google. On the same day, Google responded back to him. Then, they fixed it.
He never told the world about it until it was absolutely confirmed that Google had fixed it. In the security circles, this is known as “Responsible Disclosure”. And in Yair’s words: “The author would like to commend the Google Security Team for their cooperation and communication regarding this vulnerability.”
Yup. Both Google and Yair should be commended for handling this so well.
Now, contrast this with the Internet Explorer Javascript exploit that we wrote about a few weeks ago.
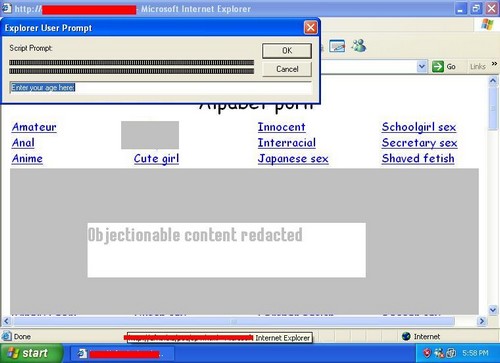
It looked like this:
This exploit attacked fully patched Windows XP systems and was quite nasty.
But here’s the rest of the story: This whole exploit started back in June, when a security researcher by the name of Benjamin Tobias Franz wrote information on a way to make Internet Explorer crash. I suppose it wasn’t considered high priority by the Microosft team because it was an incredibly obscure method of crashing Internet Explorer (it was a bug that had been fixed in IE previously but had come back).
Then in late November, an outfit called ComputerTerrorism decided to look at the exploit and figured out that it could be used as a way to hack a machine.
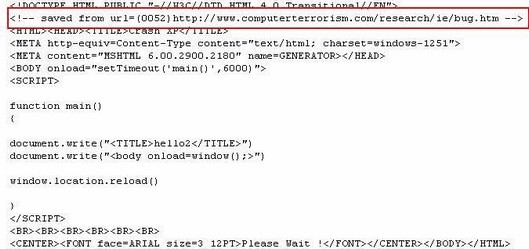
They published the details for the world and even threw in a bonus: They gave wrote the code to make the exploit actually work. It’s here if you want to see it.
Within 10 days, we started running across this exploit, inserting a trojan into user’s systems. We looked at the code and it’s clearly copied wholesale from the ComputerTerrorism site. At least in one case, the bad guys didn’t even bother to change the file name of the ComputerTerrorism file.
In other words, ComputerTerrorism did the hackers and favor and wrote the code for them. They didn’t mean to. But by their own actions, whether negligent or well-intentioned, they started the process of getting people infected with a trojan.
As an example, here is some code taken off one of the bad sites with the exploit. It even references ComputerTerrorism.
One assumes that hackers are super gurus. I hate to break it to you, but while there are some very smart hackers out there, most are script kiddies who take other people’s work, modify it a bit and then use it themselves.
Doing them a favor is the wrong thing to do.
I emailed ComputerTerrorism asking them to please take this code off their site. Never got a reply.
Microsoft ultimately patched IE on December 12th and so this exploit is solved. Microsoft should have patched the vulnerability earlier, true. But ComputerTerrorism should have alerted Microsoft of the proof of concept and waited for Microsoft to fix it first. Believe it or not, Microsoft is responsive to security holes in the products.
Only as a last resort should this proof of concept have been published.
Now, perhaps, some people in the security community may learn a lesson on it. Because by and large, the security community is incredibly responsible. A few aren’t. I don’t care if it was well intentioned. The path to hell is littered with good intentions.
Alex Eckelberry