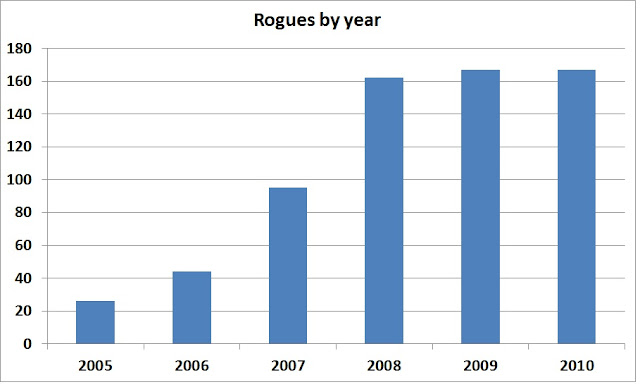
GFI Labs documented 167 rogue security products in 2010 – exactly the same number as 2009.
(Click on graphic to enlarge)
Number of rogues by year
Year Total
2005 26
2006 44
2007 95
2008 162
2009 167
2010 167
Total 661
According to GFI Labs statistics, the number of rogue security products appearing annually has been stable for the last three years. After increasing from 26 in 2005 to 162 in 2008, we’ve seen about the same number of variants each year since: 167 in both 2009 and 2010.
New “utility” look appears in 2010
Late in 2010 Researchers at GFI Labs noticed that at least one group of rogue writers had started a new deceptive tactic: creating graphic interfaces that impersonated utility software — such as hard drive defragmentation applications — instead of anti-virus products.
UltraDefragger — the new “utility” look
The UltraDefragger rogue appeared mid-November and was quickly followed by a number of clones.
FakeAV-Defrag family history:
11/15/2010 Ultra Defragger
11/16/2010 ScanDisk-Defragger
11/30/2010 WinHDD
12/9/2010 HDDPlus
12/12/2010 HDDRescue
12/12/2010 HDDRepair
12/13/2010 HDDDiagnostic
We blogged about the new look about the middle of December.
From 2005 to 2007, the rogue creators had static web sites to distribute their clones. Internet enforcement wasn’t up to speed, so the rogue sites were taken down less frequently than they are today. The rogue distributers weren’t pushed to create as many clones.
The number of rogues increased in 2008 largely because the rogue creators needed to evade stepped-up detection by anti-virus companies, according to researcher Patrick Jordan.
By 2009 the pace continued. In that year, the FakeSmoke family of rogues saw a new clone distributed almost every 24 hours, Jordan said. The FakeSmoke family of rogues began in October 2008 with WiniGuard,
(Click on graphic to enlarge)
SpySheriff: longest surviving rogue
Rogue distributors usually create their malicious software and server infrastructure then clone their malcode often in order to escape detection by legitimate anti-virus products. They count on making money in the days (or hours) that the new rogue clones go undetected.
The longest-surviving rogue was SpySheriff. It lasted from July 2005 until its site was finally suspended in August 2008. SpySheriff and its 31 clones included:
7/6/2005 SpySheriff
8/6/2005 SpyTrooper
1/30/2006 PestTrap
8/16/2006 DiaRemover
10/3/2006 PestCapture
12/18/2006 MalwareAlarm
12/18/2006 MrAntiSpy
12/18/2006 SpyMarshal
5/22/2007 DrAntispy
7/16/2007 MagicAntiSpy
7/16/2007 SpyShredder
9/12/2007 SpywareNo
3/16/2006 BraveSentry
8/13/2007 LiveProtect
11/30/2007 DrProtection
11/30/2007 GuardCenter
11/30/2007 LiveAntiSpy
11/30/2007 OnlineGuard
12/6/2007 LiveProtection
12/21/2007 Immunizr
11/28/2008 Extra Antivir
Second generation
6/3/2008 System AntiVirus 2008 (Sav)
6/3/2008 Vista AntiVirus 2008 (Vav)
6/3/2008 Windows AntiVirus 2008 (Wav)
6/9/2008 Ultimate AntiVirus 2008 (Uav)
6/18/2008 Advanced Antivirus 2008 (AAV)
7/30/2008 Antivirus Master (AVM)
8/22/2008 Power Antivirus(PWA)
8/26/2008 Spyware Preventer (SPP)
9/11/2008 Micro Antivirus 2009 (MicroAV)
10/28/2008 AntiVirus Sentry (AVS)
11/3/2008 Ultra Antivirus 2009(UltraAV)
Thanks Patrick
Tom Kelchner