New trend in rogue security products
Since last week the rogue security products (also called scareware) that we’ve posted on the GFI-Sunbelt Rogue Blog have had a new look. Instead of impersonating anti-virus products, these new ones are claiming to be applications that fix disk errors on a victim’s machine: HDDDiagnostic, HDDRepair, HDDRescue and HDDPlus. They’re basically clones and together they are members of a new family of rogues: FakeAV-Defrag.
Of course, they actually do nothing except throw up phony warnings and demand that the victim purchase them before they “fix” the fictional problems they warn about.
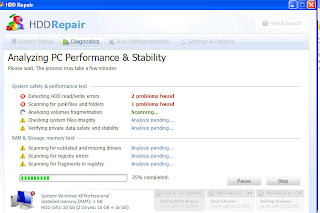
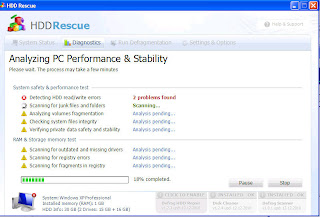
FakeAV-Defrag rogues:
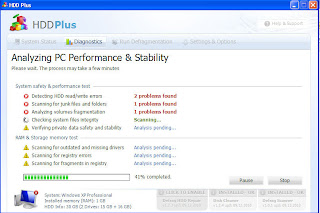
(click on graphic to enlarge)
Since rogues began to circulate seven or so years ago, they’ve always pretended to be anti-spyware or anti-virus products, imitating the look of many legitimate anti-virus products and even the structure of their product names. In the last two months, however, it has become clear that the rogue writers are trying something new to confuse potential victims.
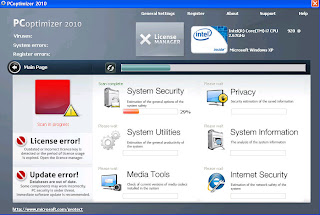
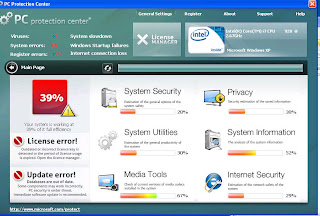
Earlier in December we had: PCoptomizer, PCprotection Center and Privacy Corrector. These were intended to look like some kind of generic security product – not anti-virus lookalikes.
Rogues that imitate generic security utilities
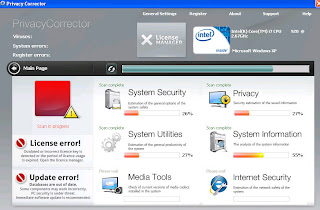
(click on graphic to enlarge)
First of the “defraggers”
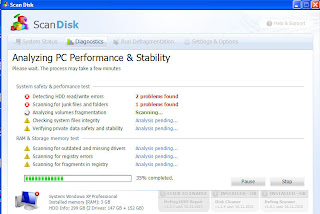
Last month we started seeing “defragger” clones that claimed to be disk utilities: UltraDefragger, ScanDisk and WinHDD. These pretended to find “HDD read/write errors.”
Defrag is a Windows utility that, at one time, substantially speeded up a PC’s performance by putting scattered portions of files in continuous sections of a hard drive. Pieces of files were scattered because applications opened and added to them over time and the operating system put them where there was space on the drive. The defrag utility “defragmented” the entire disk, assembling the pieces of files into continuous sections so the operating system wasn’t slowed by the reassembly process when accessing the files.
Defragmenting hasn’t been as much of an issue since PCs got faster, hard drives with much larger capacities became common and newer versions of Windows (with better file handling capabilities) replaced older versions. However, many home PC users have become aware of the defrag utility.
Rogues that impersonate defrag or disk utilities
FakeAV-Defrag family history:
11/15/2010 Ultra Defragger
11/16/2010 ScanDisk-Defragger
11/30/2010 WinHDD
12/9/2010 HDDPlus
12/12/2010 HDDRescue
12/12/2010 HDDRepair
12/13/2010 HDDDiagnostic
The Internet criminals who make money distributing these fakes are always changing their creations to evade antivirus scanners (at least for a few hours or days) and confuse their potential victims.
Unfortunately, since they’ve made the change from impersonating anti-malcode products to imitating disk utilities, they’ve taken away one source of help that Internet users could rely on: sites that list LEGITIMATE anti-malware products such as:
— Virus-Total (click on “credit” tab”)
— ICSA Labs:
Most legitimate anti-malcode products should show up on one of those lists.
To avoid being scammed by rogues with the “new look” Internet users should be suspicious of any application that:
— is advertised by spam email
— pops up dire warnings that your machine is affected my numerous problems (especially immediately after you click on a web page video to view it)
— tells you that you need to update your browser (often listing a version earlier than the one you’re running.)
— demands that you make a purchase before it will clean or fix problems in your machine
Like many things, if you investigate with a web search engine you will probably find some kind of discussion of the merits (or maliciousness) of the application in front of you.
Your anti-virus application should prevent rogues from downloading and installing, however, the rogue writers change their creations frequently to avoid detection for at least a few hours or days before the AV companies get them into their signature updates. Of course they also snag Internet users who don’t use on-access protection or who do not update their scanners.
You also can search for information on rogues by typing the application name in the search box on the upper left corner of the GFI-Sunbelt Rogue Blog.
(Big thanks to Patrick Jordan)
Tom Kelchner