Changing some code in Firefox to make it store passwords without notification isn’t a particularly new trick; indeed, code to do just that has been around since at least 2009. What’s interesting is the appearance of malicious files automating the process – back in October, Webroot uncovered a file that used this technique to collect logins, while using added functionality to send the stolen details back to base.
Here’s a timely reminder to always be wary of public terminals, because we have another executable that forces Firefox to store logins locally while removing any notifications to the end-user:
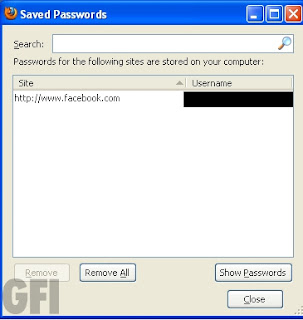
Hitting the “Enable” button alters “nsLoginManagerPrompter.js”, replacing some bits of code and adding others like the Trojan-PWS-Nslog file from October did. At this point, the unwary user will log in without any “Do you want Firefox to remember this password” prompt and go about their merry business. The moment they leave, all the attacker has to do is access the same PC, go into Tools / Options / Saved Passwords and retrieve whatever has been stored there from the list of sites, usernames and passwords.
Unlike Trojan-PWS-Nslog, the executable we tested doesn’t appear to send the logins elsewhere – it’s a local threat only, which is better than nothing I suppose. If a public terminal seems a little insecure or you didn’t see a “save this password” prompt from Firefox, it might be a good idea to check if your logins have been stored. In all likelihood, they probably just have the “save passwords” feature disabled but better safe than sorry.
Detection rates on Virustotal at the moment are quite low – 8/43 – and we detect this as Backdoor.Win32.FFGrab.A.
Thanks to Adam Thomas and Francesco for additional research.
Christopher Boyd