Our security research team has observed a new zero day exploit being used to infect systems. Coming from a porn website, this particular one is a vulnerability in VML inside of Internet Explorer.
On a sample Vmware, the following behavior was observed:
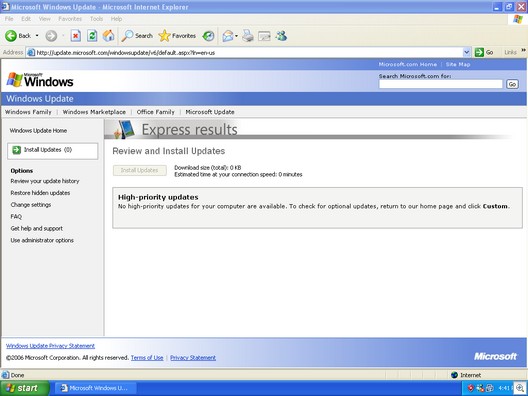
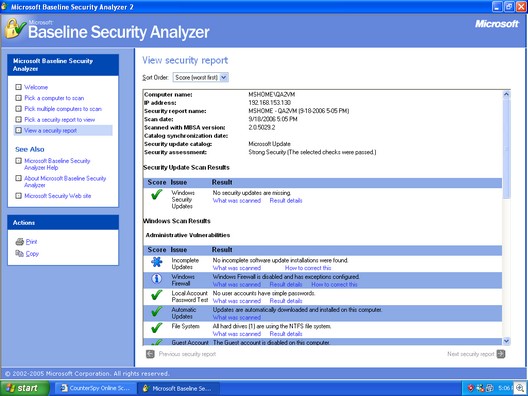
The machine was fully patched —
And just to double-check, we ran an MBSA scan which confirmed the box as fully patched:
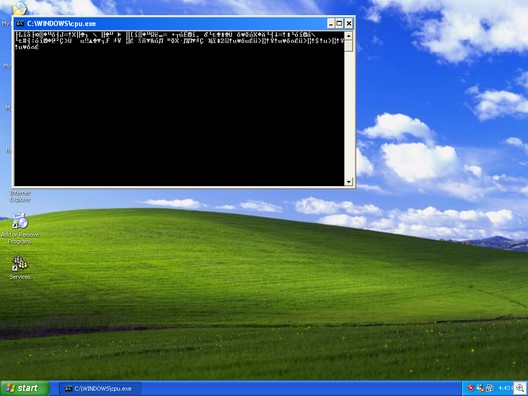
Then, the exploit code proceeds to install spyware.
The exploit uses a bug in VML in Internet Explorer to overflow a buffer and inject shellcode. It is currently on and off again at a number of sites.
Security researchers at Microsoft have been informed.
This story is developing and research is ongoing. Security professionals can contact me for collaboration or further information.
This exploit can be mitigated by turning off Javascripting.
Update: Turning off Javascripting is no longer a valid mitigation. A valid mitigation is unregistering the VML dll.
Eric Sites
VP of R&D
Update: Microsoft advisory here. See our main blog for other updates as well.