As we’ve blogged about before, there are quite a few .edu sites that have been hacked to serve spyware or porn.
And it’s pretty easy to find: Just use Google.
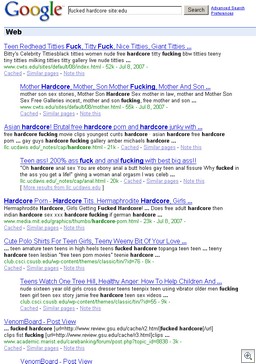
For example, the search term “f—-d hardcore site:edu” (I’ve removed the offensive language) brings back over 100,000 search results. Many have hardcore porn in them. Many have already been cleaned. And many, of course, are legitimate university web page.
But check out the search results in this image (the content is highly offensive so I’ve thumbnailed it if you choose not to expand the image):
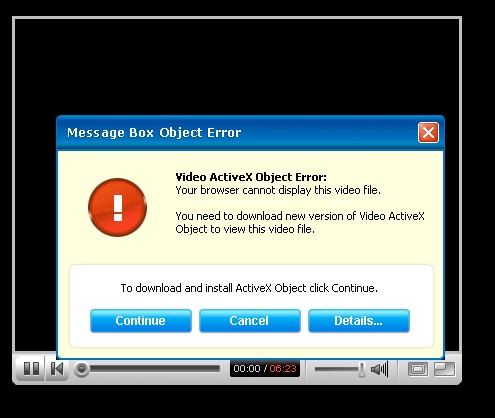
It’s all over the place. Christian Witness Theological Seminary has a redirect to a page which tries to install a fake codec (malware) from freerealitympegs(dot)com:
UC Davis has a redirect to the site findadult(dot)net (similar to Adult Friend Finder).
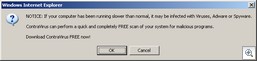
MIT has a redirect to porn, which on exit, tries to push Contravirus:
Cal State San Bernardino has a site which redirects to “teen movie galleries”, which on exit, tries to push MalwareAlarm.
Virginia Tech has several pages that redirect to “ebony porn”.
You get the picture. The list goes on and on and on. Lots of attempts to install spyware (through fake codecs) and rogue antispyware products. And lots of other nasty stuff.
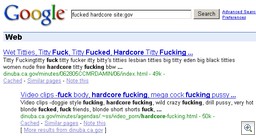
And it’s not just universities. You can try the same search term, with “site:gov”. You only get a couple of hits, but check out this from Sandia National Labs (warning, offensive content):
Click on one of those links, and you get an attempt to install a fake codec from free3xmovies(dot)com.
And the city of Dinuba, California, redirecting to an attempt to install a fake codec from freerealitympegs(dot)com (warning, offensive content):
How does this happen? It’s probably all over the place: Poorly maintained content management systems. Poorly maintained LAMP stacks. Wikis and tikis. One article to read is here.
It’s why patching and good security practices are so critical. People talk about patching Microsoft apps. Yes, that’s vital. But open source software needs to be kept updated as well.
As one security researcher mentioned to me in an email:
One problem with the edu sites is they have web applications that faculty and students use to create websites, upload content, etc. The students and faculty graduate or move on, but the stuff stays on the servers for a long time, years in some cases. Then the php apps and other server side apps become outdated and the vulnerabilities are never patched — perfect opening for hackers.
And they have forums/guestbooks etc. that are abandoned and spammed to death, or hacked. The stuff stays up forever.
I talked to one guy (by email) at a small private edu in upstate NY — he was the webmaster, professor of computer science, & head of IT. It was evident he had no clue of the state of the internet (exploits, hackers, crimeware, etc.) He seemed to think the internet was still like it was in the mid 90’s. His own site had some web apps that had been hacked. He knew there was a problem, but he had no clue why. Really sad and depressing, especially since he is teaching computer science!! I sent him some links — I hope he read them.
So there you have it: Google as a poor-man’s security scanner, which an IT administrator might use to see what might be missed in his/her own network — simply by regularly doing Google searches on their site with a few keywords. If one wants to get fancy, one can also use Yahoo Web Services APIs or Google APIs for fancy queries. It’s kind of a “jury rig” security but what the heck, it’s one more tool to use.
Alex Eckelberry