For many security researchers, our sandbox has become part and parcel to their daily routine.
It’s a very powerful tool — you can submit malware and get a detailed description of what it does. Some people simply upload malware and use our reports for analysis, others formally license the sandbox for their own use (customers range from corporate security departments to other security software and hardware companies). We also license data feeds that come out of our research, which can be quite valuable in creating signatures or blocklists.
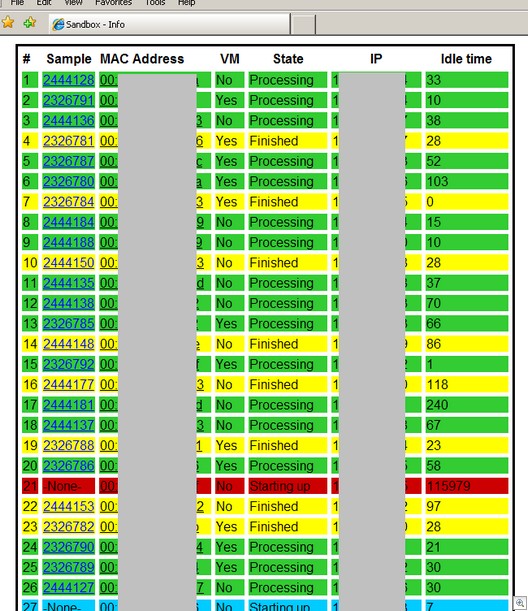
The sandbox never sleeps and it processes a lot of malware — here is a screenshot I took this afternoon of the status of our various internal sandbox systems:
(I’ve masked the MAC address and IP numbers for obvious reasons.)
It can be interesting to watch this screen and just view what’s going on. Clicking “Sample” leads to a report of what was submitted. For example, clicking #4 gives brings me a report on a submitted program. I can also see its network activity, and this particular one is chatting back to an IP that’s had a dubious history — 66.220.17.200.
So feel free to submit samples to the sandbox and use it for your own research. The main URL is http://www.sunbeltsandbox.com/
Alex Eckelberry