How does it work?
It’s a simple enough attack, luring Tumblr users with the promise of “hidden” pornographic content that requires entering login credentials to view. “This page contains adult content. Please revalidate your credentials”:
The pages involved are all regular Tumblr users who have previously been compromised. Once hijacked, their pages are converted into the fake logins and then sent into the world following regular Tumblr accounts. At that point, the phisher hopes those same accounts will visit the fake login, enter their details and keep the cycle going.
What sites are involved?
A handful of domains have revealed themselves to be at the heart of this scam, domains which we’ve previously written about.
tumblriq(dot)com
tumblrlogin(dot)com
tumblrsecurity(dot)com
Tumblriq(dot)com was registered on the 15th of June to someone called “Jack Alimae”, and the other two URLs were registered on the 25th to “Mike Alexander” – however, both sets of registration use the same address which suggests potentially fake data was used somewhere down the line.
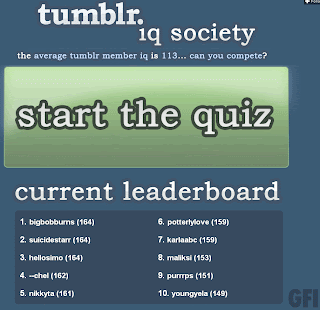
Tumblriq(dot)com started out here on the 23rd of June, serving up various adverts to users clicking on compromised Tumblr accounts promoting a “Tumblr IQ Society”.
Not long after this, the additional domains started to appear and then the full scale phish invasion took things up a level, with compromised accounts serving up a mixture of Tumblr hosted text and login credential submission forms served up by free webhosting accounts. While many of the compromised Tumblr accounts wanted you to login on the same page, many more besides were redirecting end-users to the tumblrlogin(dot)com website.
If ever a scam page had a name that implied you should do the exact opposite of what it suggested, it would be that one. The problem has become so pervasive that regular Tumblr users are setting up dedicated anti phishing sites to advise users of the problem. One of these sites actually pointed us in the direction of one of the dropzones used for the stolen logins, and the problem does indeed seem to be out of control at this point.
The data we saw contained 8,200 lines of text stretched across 304 pages of Microsoft Word, and even accounting for the inevitable duplicates and fake data that’s still quite the goldmine of pilfered login credentials.
There have been other data drops, but the scammers keep moving them around. We have of course notified Tumblr in relation to the hijacked accounts.
Why Tumblr?
What does somebody want with that many Tumblr logins? We can only guess. The stolen accounts could be used as some form of advert affiliate money making scam, or maybe we could see lots of pages with survey popups pasted over them. There is the very real possibility that the Tumblr accounts are simply a way to test if those users are logging into other services with the same credentials – at that point, everything from email accounts to internet banking sites could be fair game.
At time of writing, all three .com URLs are not resolving, although whack-a-mole has been taking place with these sites for a few days now. They could well return at some point (indeed, one of the free webhost phish pages is still alive despite countless reports to the host) and Tumblr users would do well to verse themselves in the art of phishing scams, and fast. These issues make the recent messaging spamrun on Tumblr look like a very small drop in the ocean at this point.
Christopher Boyd and Jovi Umawing
(Thanks to Steven Burn for takedown assistance and Antiphishing on Tumblr for their work in tracking the scammers).