Not so long ago, I wrote about a Botnet creation tool that allowed you to insert your Twitter username into your bots and control the infected computers via commands posted to Twitter feeds. This time around, we have something a little different:

Isn’t it cute? This program places the tools of destruction into the hands of the victims, which is never a good thing.
It’s distributed as a kind of “free for all” kit on hacking forums, where individuals are encouraged to take the code, files and graphics then improve upon the basic package:
Here’s what some of the code from one of the many files included looks like:
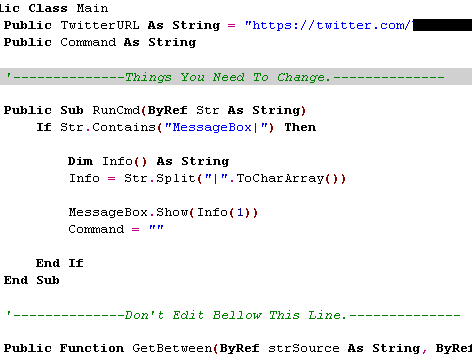
Note the “edit this / don’t edit that” lines in the code, and also that there is a Twitter account listed. This is the account of the creator, so at a minimum the bare bones package will always follow orders assuming that account isn’t deleted. Of course, the real fun begins when users add in their own Twitter account(s), and also add new commands to the program.
Here’s a very basic example of what the program can do: once I’ve added my own Twitter account to the code in the executable, I start posting commands to my Twitter feed.
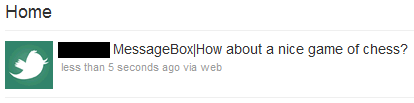
At that point, all I need to do is send the nice looking TwitterBot file to the victim and convince them to run it. When that happens, the “Message box” command will pop this on their desktop:
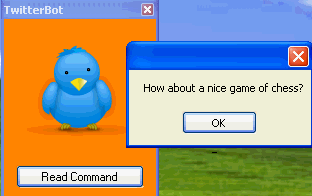
Pulling a message from Twitter and opening it on the desktop is fun, but we’ve already seen versions out there with more malicious uses for Twitter commands like downloading rogue executables, opening up files on the C drive and a particular favourite…hunting for login credentials:
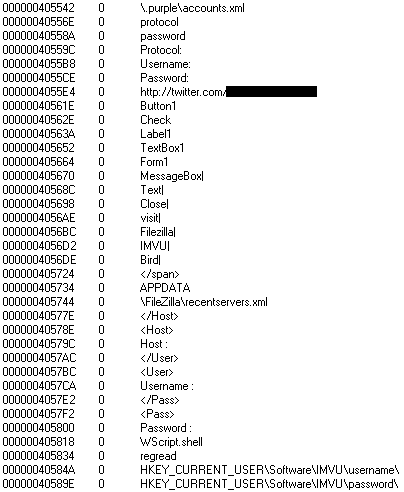
To coin a phrase…”Whoops”.
Of course, much like the Twitternet creator program this suffers from a few drawbacks of using Twitter to “do bad things”(TM). If the account named in the code goes AWOL, then the progam is a dead duck (or in this case, a dead friendly looking blue bird). It also won’t obey commands from a private Twitter account so for the moment, hiding in plain view isn’t really an option and users will have to accept their shenanigans could well be monitored and shut down accordingly.
Still, there are enough people out there who will unfortunately run any random file sent to them that the threat from those lurking Twitter commands is quite real. We detect this as Backdoor.Win32.Vortwix.A.
Thanks to Adam Thomas from Sunbelt’s Malware Research Team for additional research.
Christopher Boyd
