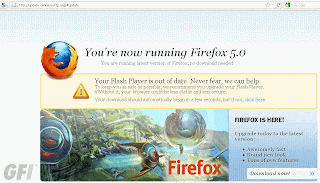
Browser specific scams have mostly been seen in the realm of rogue AV attacks, but here’s one (located at update-center(dot)myftp(dot)org) that checks out your browsing credentials then sends you to one of the below locations for a fake flash update:
IE8: Redirected to usa(dot)gov. No fake flash for IE users. It’s a different story for Chome and Firefox, though.
Chrome 12.0.742.112: You’ll be asked to run “v11_flash_AV.exe”
Firefox 5.0: You’ll be asked to run “ff-update.exe”
According to our man Patrick Jordan, these slices of Malware are 2GCash variants. Breaking out the history books, he tells us:
“2GCash began around July 2008, and started with:
A) FakeCodec sites
B) Online Scanner Scam sites
C) Fake Crack Serial sites.
The primary function has always been click fraud transmission and Search Engine Results hijackings.
Their secondary function is to potentially bring down PDF exploits, rogues, and other types of malware.
In 2010 they started monitoring for VMware so you can only install them in a normal computer.
They also tend to rotate variants almost every 6 to 12 hours as a method to try and evade detection.”
We detect these as VirTool.Win32.Obfuscator.hg!b1 (v). Steer clear!
Christopher Boyd (thanks to Adam, Wendy and Patrick for finding this one & additional research)