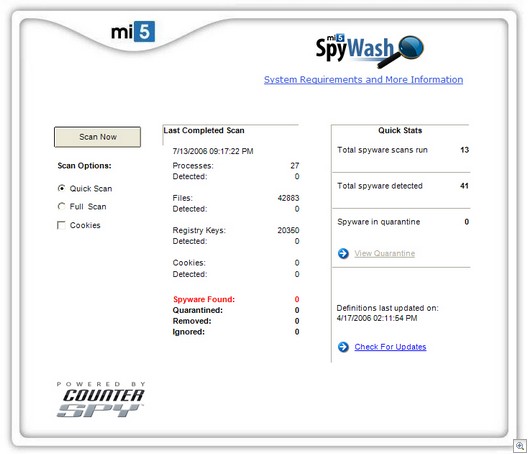
Last year, one of our partners, appliance vendor Mi5 Networks, installed one of their test systems into a fairly large university (Mi5 uses our Linux-based antispyware scanner to scan for spyware coming into the network).
Since it is a well-known fact that university students never touch spyware, porn or P2P, </irony> it was with some surprise that appliance’s outbound detection found a percentage of its students had some kind of spyware on their systems.
So what to do? The university could, as a simple measure, purchase an enterprise antispyware desktop application. However, Mi5 started talking with us about another idea: Putting in place what was later termed a “dissolvable” agent which would be deployed through the appliance. The appliance could quarantine the system in question, and force the user to run a spyware scan off of the appliance.
We firmed up the plan with the Mi5 team while meeting at the RSA Conference in February and they are now shipping this solution, which they term “Spywash”.
So what exactly is this “dissolvable agent”? In its current form, it’s an ActiveX control loaded from the appliance (a future version will also run as a Java app). A page comes up when a system is discovered to be infected, and the user is given little choice but to run a scan. Once the machine is cleaned, the machine can then access the network without further hindrance. In the future, more rigorous controls are expected to implemented to fully quarantine the box from the network.
More Sunbelt propaganda here; Mi5 propaganda here.
Alex Eckelberry