live.sysinternals.com is a great resource for ad-hoc use of Mark Russinovich‘s very useful set of tools.
For example, consider working on a system, and needing one of Mark’s tools, but simply not having them readably accessible.
In this case, all you have to do is remember the following URI:
live.sysinternals.com/tools
If the machine has internet connectivity, simply type that text into the address bar:
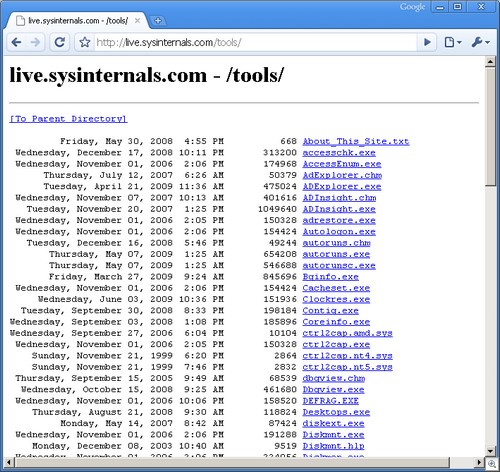
All of the tools you might want to use are right there.
But it gets better. Because this site is available directly from the command prompt, or Explorer.
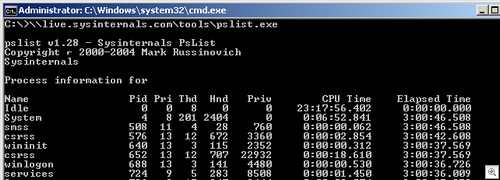
For example, let’s say you wanted a list of all processes running on a system. Mark has a useful tool for that, pslist.exe (similar to the Unix ps command).
Open a command prompt, and type
live.sysinternals.comtoolspslist.exe
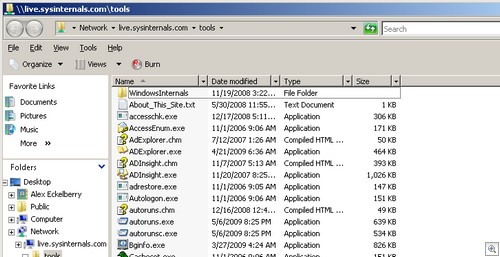
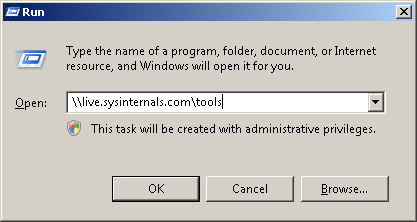
Or, if you want to open the contents of the site in Windows Explorer, you can just put the following text into Run:
And you get the contents in Windows Explorer:
Now, if you’re working on a system that has a DNS Changer, or has a modified hosts file, either of which redirect sysinternals.com, you’ll obviously need to handle that problem first before getting to this site. While a hosts file redirect should be bypassed at the command line, that wouldn’t be the case with a DNS Changer. (Incidentally, the first thing I would recommend doing when you get on a badly infected machine is check the DNS entries and kill the hosts file — a lot of people don’t do that, and end up by spending hours hitting their heads against a wall.)
Update: Silly me, of course you could still access this site by IP, even if the hosts file or DNS server had been changed. Example: \207.46.140.150toolspslist.exe
With thanks to Randall, and the SANS Forensics blog.
Alex Eckelberry