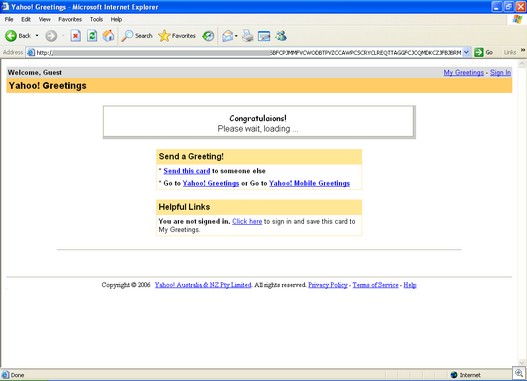
VML exploit in a fake ecard:
On our test system, the greeting card in question downloaded a number of pieces of executables: is.exe, ie.exe and cpu.exe.
One assumes this will be sent via spam, but we have not seen any samples.
Credit goes to Roger Thompson over at Exploit Labs and Alex Shipp at MessageLabs.
Alex Eckelberry