It seems Larry Hryb, Director of XBox Live Programming, had his account taken over at the weekend. However, there are a number of faintly hysterical headlines claiming he was “hacked” along with “are you next?” taglines (such as this one), and I thought it might be useful to look at the methods the team behind the attack might have used and how you can lessen the chance of something similar happening to you.
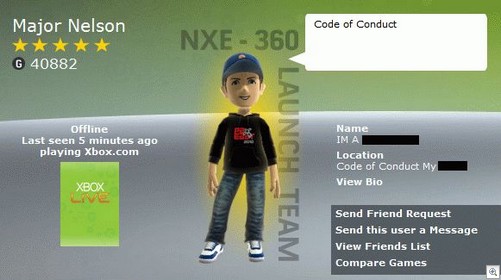
First of all – let’s see what happened to “Major Nelson” (as he’s better known). His Live account was hijacked, and numerous offensive messages were posted to the Biography section. Here’s a screenshot:
As you can see, “Code of Conduct” is in his speech balloon and Name / Location are, er, somewhat colourful. At one point it also said “Any account $100 PayPal!!!!!!!!”
Where this tale becomes interesting is the fact that the attacker has put an endless stream of information about himself onto the Net. The homepage of his crew hosts a video that reveals his Skype address, AIM account and – more seriously for him – a name and address that the URL is registered to (his Facebook page is supposedly all over forums, and he seems to have a history of console scamming dating back to at least 2008). While the information could be false, everything about this so far screams “script kiddies” and generally speaking they don’t tend to think about faking Whois data.

Script kiddies or not, they still managed to compromise the account of a Microsoft Exec. How did they do this? Well, I talked about some of the methods used in relation to grabbing XBox Live accounts in Canada last year – while there’s no way to know how they did this yet, we can explore a few of the possibilities available to the account compromisers out there:
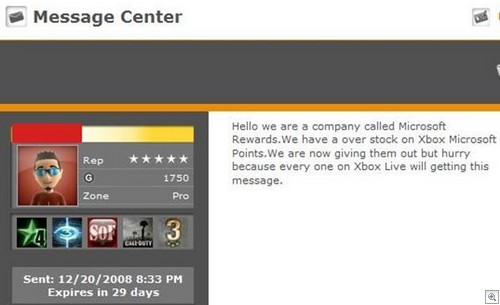
1) Phishing. This is usually the number one method for grabbing XBox Live accounts – fake XBox Live logins are a dime a dozen, and they also tie into fake XBox Live Generator programs (that claim to give you “free money” but actually steal your account details). Sometimes people will send phish links or requests for logins from compromised accounts, too:
Now, I can’t imagine Major Nelson running a fake generator and I don’t think he’d fall for a random phish. What IS interesting here is that Stephen Tolouse (the Director of Policy Enforcement) said the following on Twitter:
“Looks like this was very specific and very targeted to Major. I’ll look into the details and report back later.”
Could it have been a spear phish? It seems doubtful, given the way the individuals behind the attack have placed all sorts of personal data online for investigators to follow. Stranger things have happened, however.
2) Social Engineering. There are a number of options available here, but more often than not an attacker won’t try to Social Engineer the victim; they try to fool the support staff on the other end of the helplines. Of course, this is the one place where the victim is somewhat helpless – if the support staff falls for an individual calling up pretending to be you, there’s not a lot you can do about it.
Having said that, individuals that attempt these kinds of calls usually run into a brick wall if you take some precautions. Entering some false information into the personal info boxes for the questions attackers are most likely to know the answers to works wonders (though it goes without saying you need to remember what information you’ve put into the account!):
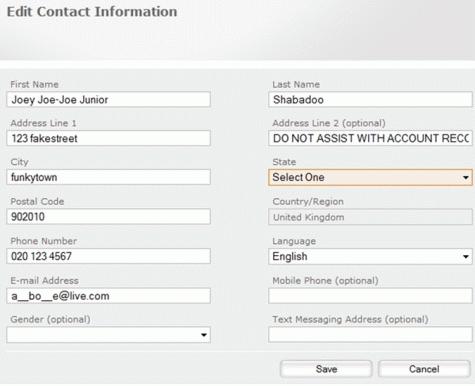
If you’re curious about the EMail address having underscores in it, there is a theory that support staff the world over will see an EMail address show up on their system with what appear to be letters “missing” and think it’s protected by some fancy pants security system. Of course, it isn’t – but if the attacker is trying to squeeze your EMail address out of the support staff and they can’t even read it back to them properly then great.
3) Live Account Password Reset. The other method is the old classic – guess the secret answer to the Live account password reset question. A good tactic here is to have a totally nonsensical (but memorable!) answer to one of the common questions. As you can see, my mother has an interesting birthplace:
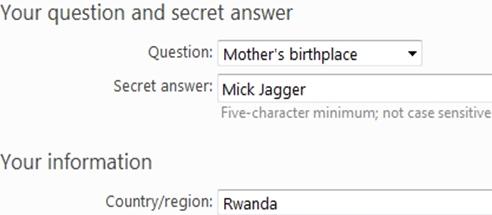
I also appear to live in Rwanda, which is probably going to confuse the attackers a little bit more. It’ll be interesting to see if Microsoft release any additional information on this high profile compromise, although you probably don’t need to start worrying just yet about the safety of your XBox Live details. As long as you steer clear of phishes, strange programs advertised on Youtube, messages from people you don’t know and apply a little common sense in relation to the information you enter on contact forms you’ll probably be fine.
Christopher Boyd