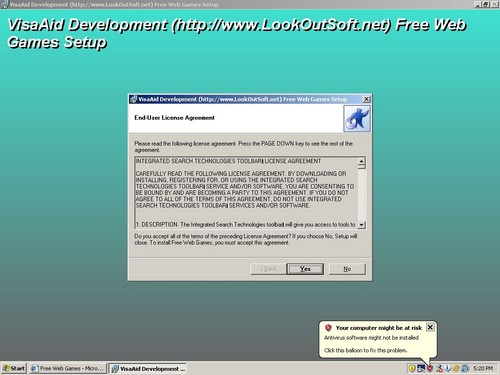
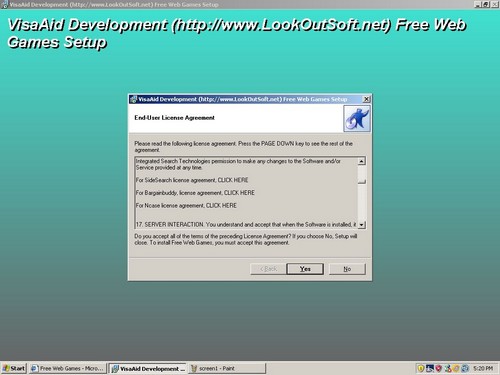
First, let’s make sure our definitions are clear. A rootkit is generally defined as software that is installed secretly and is undetectable. It provides the most powerful level of control to the system without the system owner’s knowledge. It gives “root” privileges, a term used in Unix to denote the highest level of authorization — also called superuser. A full definition is here.
Microsoft program manager Mike Denseglio talks about rootkits to ZDNET and says some surprising things:
What is a rootkit?
A rootkit is not an attack vector on its own. It is not a virus, and it is not a worm. It is a cloak or a disguise — something to hide something else. For instance an attacker might want to use a rootkit to put a virus on your system but doesn’t want you to be able see that virus.
Is a rootkit malware?
Most people think it is, but it is not always. A sys admin might want to use a rootkit to hide something from the user, to monitor the system in some way. I treat rootkits neutrally — I don’t want to class them as good or bad. You have to make your decision in each case. [My emphasis.]
The rootkit is not a virus, a worm, or a Trojan horse. It is just the code that hides something. Can it hide worms and spyware etc? Absolutely it can. The issue in the Sony DRM case is whether Sony properly disclosed that it is installing a rootkit on your system. And what Sony uses is a rootkit: it hides other things.
First is the illogic. How can Denseglio define a rootkit as something acceptable if there is full disclosure? That, by definition, is not a rootkit.
For example, you have those programs that lock down computers (you see them at retail stores like CompUSA and BestBuy). They may be hidden in user mode from the user. However, the administrator can gain access to them. Commercial keyloggers may be in the same vein — the administrator of the keylogger can get to it.
Look at what the Sony rootkit did:
1. It didn’t disclose itself.
2. It hid itself from the user.
3. It provided no means to uninstall itself.
4. Because it was hidden, it created security holes that hackers could use to gain access to a system.
5. It hooked into the kernel.
6. It provided Sony with superuser/root capabilities.
But if it was disclosed, would it still be acceptable? No.
Denseglio is watering down the definition of rootkits and that is a slippery slope.
To quote Eric Howes in a recent email on the subject:
Think of all the interested parties who will welcome the news that it is perfectly acceptable to drop rootkits on users’ PCs in order to assert control over them, as long as there is some form of disclosure.
And given what passes for “disclosure” these days, we could very well start seeing various parties who regard users’ control of their own PCs as a threat or a nuisance simply wait a bit until the Sony uproar dies down a bit and then start rolling out their own rootkits — with some notice buried in the EULA, of course.
The next step will be to invent a more “friendly” term for “rootkits” — perhaps “administrative cloaking tool,” or even “secure protection utility.” The goal here will be to hang a name on the technology so that it actually sounds like a benefit to the user.
It’s hard to see how users or consumers or citizens benefit from an approach that regards rootkit technology as “neutral, neither good nor bad in and of itself.” There is nothing “neutral” at all about the effects that this so-called “neutral” approach will have on users, who will now have to grapple with software companies, advertisers, and content providers vying to use rootkits to LEGALLY assert control over the PCs of users for whatever end.
I don’t know Denseglio and I don’t necessarily blame him for his comments and I’m certainly am not interested in attacking him or his credibility. But his statements merit discussion and debate. To me, the answer is simple and he may very well agree with me:
Rootkits are unacceptable in any situation.
Link here.
Alex Eckelberry