“Etiquette” is a word that many in today’s world seem never to have heard – at least, judging by their behavior. It refers to the rules, mostly unwritten, that govern what behavior is considered proper or acceptable, especially in public or when interacting with people you don’t know well.
Those born in the baby boomer years grew up with Amy Vanderbilt and later, Miss Manners to tell us which fork to use when and how to formally address a letter. Many of that generation rebelled against the rules, and promoted the philosophy of “if it feels good, do it.” That philosophy has, in many respects, carried over into the Internet world as global connectivity created a brand new online society where we come into contact with many, many more people from all walks of life that previous generations ever did in a lifetime.
The Internet is often compared to the wild west, a “place” of freedom, where the old rules don’t apply. Efforts to impose limits on online behavior (especially by the government) usually meet with great resistance, although that’s slowly changing and it appears our “last frontier” is slowly becoming more tamed.
Is that a good thing or a bad thing? Certainly the stilted conformity of Victorian times wasn’t conducive to creativity or personal gratification. But have we gone a little too far in the opposite direction on the ‘Net, where flame wars rage, “hate speech” flourishes, and pornography of the vilest sort is readily available? Is a world with no rules really a “free” one, or do rules actually exist to prevent some from infringing on the freedoms of others?
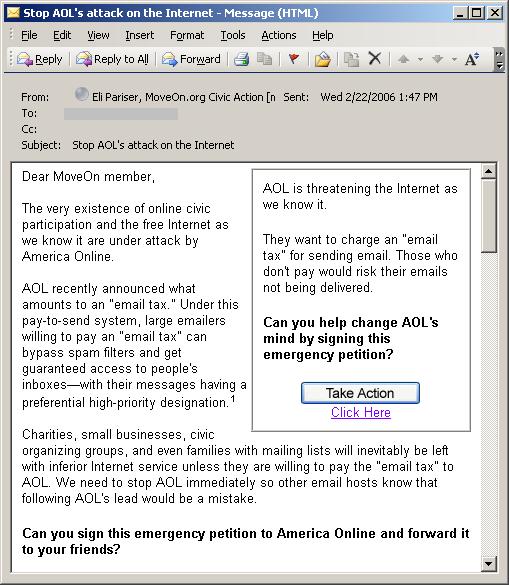
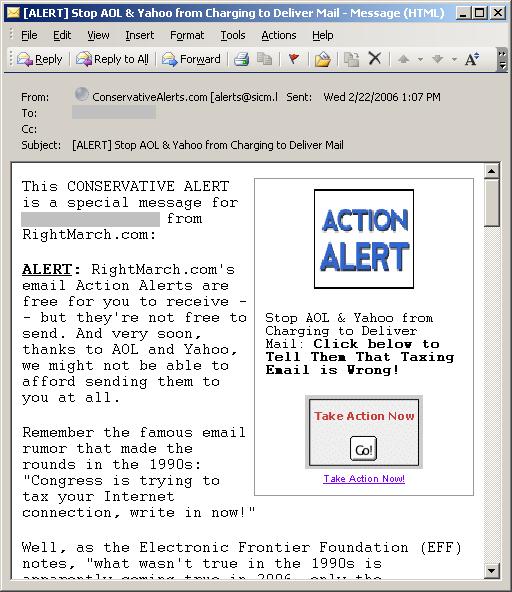
I hear many complaints, from Internet users of all ages, about the lack of basic etiquette today, online and off. It does seem that many people are much more inclined to be rude or even hateful in online communications than in “real world” face to face interactions. I guess it makes sense; there’s an illusion of anonymity online that makes folks think they can get away with saying or doing what they want without the same consequences they would face in their offline lives (it’s hard for someone to punch you in the nose or report you to the cops if you’re only a faceless email address or nickname on their computer screens).
Many of the offenses that people complain about aren’t big things: others who “shout” by typing email messages and newsgroup/message board posts in all caps, those who send HTML mail to discussion lists, and so on. These are analogous to the people who break in line at the grocery store or chat loudly on their cell phones in restaurants; their behavior doesn’t endanger anyone or cost us money, but it’s irritating and annoying and temporarily reduces the quality of life for those around them.
In law enforcement, there is a concept called “Broken Windows” that’s based on the premise that little things (like broken windows and other physical signs of deterioration in a neighborhood) lead to big problems. Likewise, little breaches of etiquette on the ‘Net and in real life can, I think, result in an overall deterioration of behavior in general.
Of course, one problem with etiquette is that the same rules don’t always apply everywhere. Just as you aren’t expected to dress, speak or act the same way depending on whether you’re at home, at a friend’s home, or attending a formal function at the White House, netiquette also depends on “where” you are in cyberspace. For example, on some mailing lists it’s verboten to include the entire quoted message to which your responding with your response. On others, that’s standard operating procedure to ensure that everyone can easily keep up with the thread as it’s evolved.
Netiquette (etiquette for the Internet) follows the same general principles as offline etiquette. It’s important to remember that all public forums (newsgroups, mailing lists, chat rooms, web boards) are, well, public. And to comport yourself as you would in any public place. If you wouldn’t run up to a stranger at a dinner party and call him a dirty name for expressing an opinion with which you disagree, why would you do it on a mailing list?
Despite the thick books on the subject and the seeming complexity of navigating through the silverware at a formal dinner party, the core principle of etiquette is very simple: behave as you’d prefer others to behave toward you. Respect people and their time and bandwidth. That means knowing whom you’re communicating with and, if they use a dialup connection, not sending an HTML message with embedded photos that will take them an hour to download. Don’t expect instant answers to your questions. Most people have an offline life, too.
Would you call up a doctor or lawyer you’ve met once and ask for a diagnosis of your complicated symptoms or an untangling of your complex legal mess over the phone for free? If not, it’s not okay to email that doctor or lawyer (or computer expert) you “met” on a mailing list and ask questions that will take hours of his/her time to answer.
Don’t waste people’s time by forwarding every joke you get or sending virus warnings that turn out to be hoaxes. Before you pass a story along as true, take a moment to check it out at www.snopes.com or other sites that deal with rumors and urban legends.
New networking technologies bring up new netiquette issues. For instance, with wireless networking, if the owner doesn’t take steps to secure it, anyone within range can hop on the signal and use the Internet connection or even, in some cases, access personal files. But something that many Internet users – especially those who fancy themselves “hackers” – don’t seem to grasp is that just because you can do something doesn’t mean you should do it. Even if there’s not a law against it. And that’s really what netiquette is all about.
What do you think? Should there be rules to play by when we’re online, or should anything go? If Internet users don’t start policing their own behavior, will the government start doing it for them to a greater and greater degree? What rules do you try to go by in your online behavior? What breaches of netiquette do you see most often, and which ones bother you the most? Let us know your opinions.
Deb Shinder