Two more things we’ve learned about Leo Stoller, the so-called “Trademark Troll” (he likes to go after companies to get money to license trademarks that he’s registered, and is currently going after our good friends at Castlecops for their use of the word “castle”).
1. He really likes pretty women. This is apparent in the fact that he plasters pictures of women all over his blog, often for no apparent reason.
For example, on this story about the Supreme Court’s decision on Guantanamo Bay, we have an inexplicable image of a model. Why? I have absolutely no idea.

In another example, we have a picture of Paulina Porizkova on a blog entry about toy company Mattel.

Then, there’s this model next to an article about Adenna, a company that makes…um… latex medical gloves (more than I want to know).

Ok, so maybe that’s nitpicking. After all, he has every right to put pictures of famous and beautiful women on this blog, right?
Well, I’m not so sure about that, which brings me to point 2.
2. Leo Stoller might just be misappropriating copyrighted material.
You see, a number of these images are arguably protected by copyright. For example, we have this picture of Jessica Simpson that Leo has used:

Notice the upper right-hand corner? Nice photoshop work Leo, because the original is at Art.com:

And, of course, Art.com makes it clear that these images are not to be used:
All content included on this site, such as, but not limited to, images, text, graphics, logos, and button icons, is the property of Art.com or its content suppliers and is protected by United States and international copyright laws. All content on this site that is not the property of Art.com is used with permission. The arrangement and compilation of all content on this site are the exclusive property of Art.com and are protected by U.S. and international copyright laws. All software used on this site is the property of Art.com or its software suppliers and is protected by United States and international copyright laws. Display and use of certain images on the site are subject to additional conditions as set forth in the “Special Conditions” section below.
And we have this other mysterious piece of artful photoshop work. I wonder what’s supposed to be there?

Then there’s a picture of Pamela Anderson.
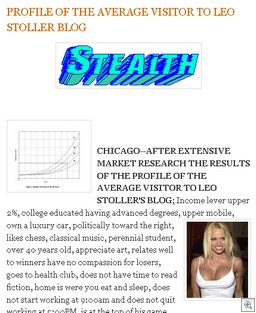
Salma Hayek

And so on.
As reference, we have this from Bitlaw on copyright concerns on the web.
Taking images from third-parties. The simple rule is, “Don’t steal someone else’s images.” The moment an original image (or string of text) is fixed on a hard drive for the first time, it is protected by copyright. Any unauthorized copying of a protected image is an infringement of the creator’s copyright, unless the use falls within one of the very limited exceptions to the copyright law, such as “fair use.” In most cases, it is unlikely that the incorporation of an image into a commercial web-site would be considered a fair use.
He could argue fair use, but on a commercial blog that is actively promoting his business, I think that’s a difficult argument.
However, nothing in the law is cut and dry on fair use. A lawyer friend of mine also took an interest in Leo’s blog and made these comments about Loe’s use of pretty women:
If Leo is reporting a news event or making some satirical or political comment about the picture (as opposed to the celebrity), it could be OK. But since it’s a blog, it is likely that he is just making personal use of the photo, and that’s a copyright violation. That said, as a non-commercial use, the damage from the infringement would be pretty minimal (unless the shot has commercial value and could be downloaded from the client’s blog), but I’d say the photographer could still have a potential copyright claim.
Going a step further, his violation depends on the use being made of the picture and whether that use falls within the fair use exceptions to copyright (criticism, commentary, research, scholarship, etc.). If the blog is for criticism or commentary rather than simple personal use it’s more likely to be a fair use. Also, copying of a photo has been held by at least two circuits to be permissible because the use was “transformative”. The key cases in this area are called Kelly v. ArribaSoft and Bill Graham v. Dorling Kindersley – both dealing with the transformative use of photographs (Kelly had to do with posting photos on a website).
Like I said, it’s a gray area.
But why do I care? Why should anyone care? Well, in my view, Leo’s entire business model is based off of abusing intellectual property law to his benefit, with frivolous, baseless legal actions that effectively extort companies. And yet he finds no problem taking a Jessica Simpson picture, altering it and then posting it as his own on his website.
And so the point is this: Is Our Dear Friend Leo, who argues vehemently and passionately about ethics, intellectual property protection (he even has a whole blog post with his terms of use) and the like, practicing a double-standard? I’ll leave that for you to decide.
Alex Eckelberry
(With credit to Leslie who assisted me greatly in putting this material together.)


















![Pirt2312312312_small[1]](http://sunbeltblog.eckelberry.com/wp-content/ihs/alex/pirt2312312312_small%5B1%5D.jpg) The
The