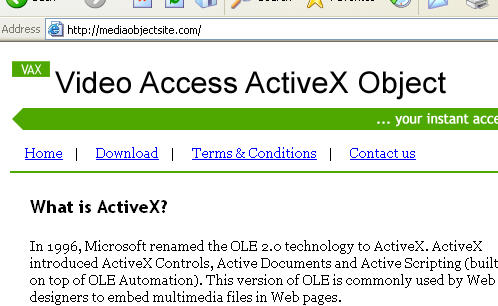
New scam sites. As always, avoid these sites and the software they peddle like the plague:
IP:85.255.117.194
activexsite.com
IP: 85.255.117.194
generateskey.com
IP: 69.50.188.102
mediaobjectsite.com
Patrick Jordan
The Legacy Sunbelt Software Blog
The Great Years: 2004-2010
From lawyer David Fish:
Yesterday, DirectRevenue closed out another case filed against it. The lawsuit filed on behalf of California residents was granted final approval by a Federal court in the Eastern District of California. …My understanding is that DirectRevenue is still litigating against the New York Attorney General. I am aware of no other consumer-based lawsuits.
I have noticed a trend. It seems to me that as American-based “adware” companies are being sued by consumers and being sued by government agencies and being criticized by bloggers, they are changing their behavior.
Link here, with copies of the settlement and more.
Alex Eckelberry
One of the biggest issues with fighting malware and other internet crime is cross-border jurisdiction and information sharing.
There was a good push ahead in this area with the recent passage of the US SAFE WEB bill. From the summary of the bill:
Authorizes the FTC, upon written request, to provide investigative assistance to a foreign law enforcement agency that states it is investigating or enforcing proceedings against violations of laws prohibiting fraudulent or deceptive commercial practices or other practices substantially similar to practices prohibited by laws administered by the FTC, other than federal antitrust laws, without requiring that the conduct identified constitute a violation of U.S. laws. Requires FTC consideration of specified factors in determining whether to provide assistance, including whether the requesting agency has agreed to provide reciprocal assistance to the FTC. Authorizes the FTC to negotiate and conclude an international agreement for providing such assistance, materials, or information. Stipulates that this Act does not authorize the FTC to take any action or exercise any power with respect to a bank, savings and loan institution, or federal credit union. Prohibits FTC investigative assistance to foreign law enforcement agencies from foreign states which repeatedly provided support for acts of international terrorism.
And, CDT link here.
Alex Eckelberry
There’s was an interesting article in yesterday’s MercuryNews about venture capitalists (VCs) who become entrepreneurs.
“Some people who came into the venture business between 1999 and today have observed that no one has made any money, unless you happen to have invested in Google and YouTube,” said Jon Holman, a venture capital recruiter in San Francisco who works closely with more than 50 firms, including Mayfield Fund and Accel Partners. “Those same people are now saying, `Maybe this will get better, but it may be time to try something else instead.’ ”
I think every VC should have experience actually working in a company. The problem? I can’t understand how they’d want to be a VC after having been in an operational role. It’s so much more interesting and fun than investing. But everyone has a different viewpoint on the matter.
After a career in the software business, I moved into the VC side in 1999, working as a private equity investor for a large investment fund.
For a while, I was a genius: Every investment I made was golden. Then April 2000 happened. And everything changed. Things got really hard. I learned a whole heck of a lot about distress financing, company and asset sales, turnarounds and the like.
In 2002, after my firm’s major operations were sold to the Monitor Group, I went to head up software at Sunbelt. And haven’t looked back.
Maybe one day when I have more time, I’ll elaborate about my experiences on that side of the business. But I’ll end with this note: Being a VC is looked on as a some kind of wonderful experience. To me, it wasn’t. I’m much happier making things, rather than trying to make money from money.
Alex Eckelberry
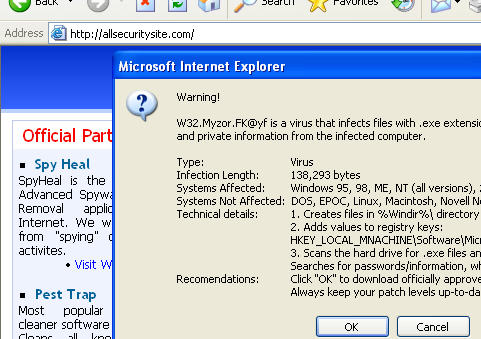
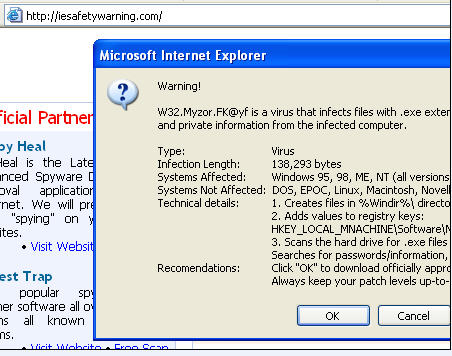
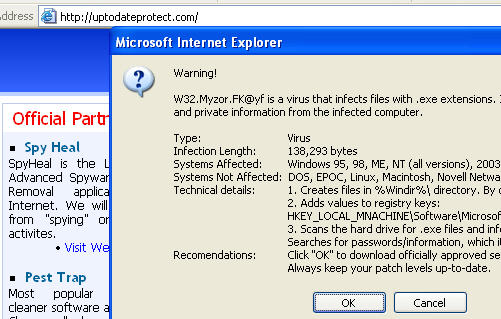
New scam sites. As always, avoid these sites and the software they peddle like the plague:
IP: 85.255.117.196
activexmediaobject(dot)com
IP: 85.255.117.194
multimediaobject(dot)com
IP: 85.255.116.210
iesafetywarning(dot)com
IP: 85.255.116.210
uptodateprotect(dot)com
IP: 85.255.116.212
alldnserrors(dot)com (404 Error Page Redirect Site)
IP: 85.255.116.212
allsecuritysite(dot)com
Patrick Jordan
What’s coming up on Patch Tuesday
Patch Tuesday is today and we’re expecting six security bulletins. Five pertain to Windows and one is for Visual Studio. Two of the patches are listed as critical. There are also four non-security updates scheduled for release. On Wednesday, December 13, Microsoft will host a TechNet webcast with more information about the December security bulletins. To register, click here.
Can Vista’s Anti-Piracy Mechanism be Cracked?
Rumors abound this week of cracking tools that are designed to defeat the Vista product activation feature, which would allow software pirates to use illegal copies of the operating system. The tools are out there, but sources say they won’t work on consumer versions of Vista, just those distributed through volume licensing. And the crack would have to be reapplied every 180 days. The worst part, for consumers, is that Microsoft’s natural reaction to such cracks will probably be to make product activation more burdensome. As usual, those of us who abide by the rules will pay the price because of those who don’t. Read more here.
Windows Live Book Search
Microsoft has recently made available an online search service for searching the contents of books. Publishers can add their content through a free participation program, and a number of universities (including Cornell, the University of California and others) and other publishers have already signed on. To try it out, click here.
Geek’s Guide to Gift Giving
They say most folks give the gifts they’d most like to get. If that’s true, then the “Geek’s Guide to Gift-Giving over at eWeek is aptly named. Some – in fact, most – of the suggested gifts are a bit pricey; you have to really like the recipient a lot to leave an $800+ chair or an $1100 monitor under the tree for him/her, not to mention a $900 espresso machine. But it makes for a great wish list to send your favorite rich aunt or uncle.
Loving and Hating Vista
Some folks love it, some folks hate it, and many seem to have a love/hate relationship with Microsoft’s newest operating system. Robert Vamosi recently gave his five reasons for loving and hating Vista. You can read my rebuttal.
 People Near Me: New Vista Collaboration Feature
People Near Me: New Vista Collaboration Feature
People Near Me is a new feature in Vista whereby other Vista users on the same network are made visible and available for collaboration sessions. Others on the People Near Me list can see and join these sessions if they know the session password (you can also hide sessions from view if you want). The Windows Meeting Space (also known as Windows Shared View) works with the People Near Me feature to allow you to invite others to meetings and give presentations, share handouts and send private notes to participants. For more info on how it works, click here.
How to stream digital music with Windows Media Connect
Windows Media Connect (WMC) is incorporated into Windows Media Player 11. If you don’t already have it, you can download WMP 11 here.
Using WMC, you can play the music on your XP computer in another room, anywhere on the network. You’ll need to connect a digital media receiver or Xbox 360 to your home network. Once that’s done, download Windows Media Connect if it’s not already installed. When you start it, you’ll see the WMC wizard.
Follow these steps:
For more detailed instructions on setting up a digital media receiver, click here.
Word Vulnerability Can Put You at Risk of Zero Day Attack
Most versions of Microsoft Word (2000, 2002, 2003 and 2004 for Mac) are vulnerable to an exploit that’s making the rounds, whereby opening an affected document can put you at risk. Microsoft issued a high-risk alert about it, but no patch has been released at the time of this writing and anti-virus vendors hadn’t been able to create detection signatures. For more information, click here.
Help! How Can I Keep IE7 from Reinstalling Itself?
A few weeks back, I gave instructions as to “How to roll back to IE6“. However, you may end up by getting IE 7 put automatically put back into Windows Update.
There is a way to block the IE 7 automatic download and installation without having to disable auto updates completely. Anticipating that many companies might not want to deploy IE 7 immediately, Microsoft released a blocking tool, which you can download. It works on XP with Service Pack 2. This is a command line utility. Link here.
Another way to block the installation is to create a registry key. As always, be careful and back up the registry before editing it. Here are the instructions:
Finally, there is a free GUI tool by IntelliAdmin that you can download. It’s a little application that just requires you to click an option button to disable IE 7 auto install (direct link to .exe).
How to use a handheld PC as a mobile Remote Desktop terminal
If you have a Pocket PC or Windows Mobile device, you can connect to your XP Professional Remote Desktop or a Windows 2000 terminal server using the Remote Desktop Connection (RDC) client. For information on how to set up both the handheld client and the server, see KB article 314537.
Can’t map a network drive under different user credentials
If you get an error message when you try to connect to a network share via the Map Network Drive Wizard using different user credentials, it may be because the folder is currently mapped using a different user name and password. There’s a hotfix available for this problem, which you can get by following the instructions in KB article 812793.
Can’t expand shares with the Ntbackup tool
If you are unable to click the plus sign (+) and expand computer shares when using the Ntbackup tool in the Entire Network location, there’s a workaround for the problem. To find out the resolution, see KB article 316929.
Until next week,
Deb Shinder, MVP
It’s an old American tradition: we stuff ourselves with turkey and pumpkin pie on Thanksgiving Day, then rush out the next day to work off all those extra calories by engaging in a strenuous exercise called “Christmas shopping.” Some particularly devoted souls have even been known to line up outside stores in the wee hours to ensure that they get in early on the sales. And each year, more and more stores accommodate them by opening earlier and earlier. This year, some electronics stores opened their doors at midnight and many others at 5:00 or 6:00 a.m.
Despite the best efforts of retailers to woo customers on “Black Friday,” (the Friday after Thanksgiving, so called because it is traditionally the day that retailers start operating “in the black,” or at a profit), after an initial increase in sales over last year, there was actually a decrease from last year on the following day. This is according to statistics from the ShopperTrak Retail Traffic Index as reported here.
Other reports indicate that shopping traffic at some major retailers such as WalMart have actually dropped; in November they experienced for the the first time since 1996 a decline in sales at established stores compared to the previous year. Not that it’s been a bad holiday season for retail outlets so far; according to the Washington Post and other sources, although shopping traffic is down, those who are out there in the trenches are spending more than ever before.
I just wonder how many people are foregoing the holiday shopping madness altogether and spending their money from the comfort of their desk chairs – making purchases online.
Forrester Research predicted back in October that this year’s online holiday retail sales would hit $27 billion. On the anecdotal evidence front, many folks I know told me that they stayed far, far away from the malls on Thanksgiving weekend, having done as much of their shopping as possible early – and online.
One thing I’ve noticed about online shopping, including my own, is that there’s no need to pack all your buying into one (or a few) special “trips.” Although many etailers (electronic retailers) have attempted to promote Cyber Monday, the Monday after Thanksgiving, as the online equivalent of Black Friday, it hasn’t really worked out that way. This shouldn’t come as a big surprise. After all, one of the big advantages of online shopping is that you can do it when and where you want. See Cyber Monday, You’re No Black Friday.
Another big advantage is that doing it online makes comparison shopping so much easier. After hours on your feet, fighting the crowds, you might very well suspect that the cool gadget you just decided to buy your aunt’s daughter’s neighbor’s dog (number 287 on your shopping list) might be had for a few dollars less at another store across town, but a small savings isn’t likely to seem worth the drive. Online shoppers need only click around to different web sites to find the best price.
There are other logistical benefits to buying online. No more need to haul a big bunch of gifts home from the store (risking the theft of those already purchased if you stop at another store along the way), laboriously wrapping and labeling them, and then hauling them across town or across the country to deliver to their recipients. When you order online, you can have the present wrapped and sent directly to the giftee.
Of course, there are drawbacks to online shopping, too – for both customers and retailers. The latter experienced the problem of network congestion on Black Friday itself, when WalMart and Macy’s both had their web sites slow down to a crawl on that day. You can read more about that here.
For shoppers, online buying requires at least a little planning ahead – if you want to make sure the gifts actually arrive on time. And of course, you can’t plop down cash; shopping online generally requires you to use a credit or debit card or some other method such as PayPal whereby you have to establish an account. There’s also going to be a record of your purchase, something that makes some privacy advocates uncomfortable.
If you’re worried about the security risks of online purchases, though, you probably shouldn’t. A recent Gartner report finds that most e-commerce sites are more secure than the average physical retail establishment’s Point of Sale (POS) systems. Makes sense to me. I’ve always worried when a sales clerk or waiter disappeared into a back room with my credit card, much more so than when I entered the card number on an encrypted web site.
Security and practicality aside, some people say all the convenience and efficiency of online shopping takes some of the holiday spirit out of Christmas, and maybe it does. Do my gifts really deserve to be appreciated if I didn’t suffer appropriately to procure them? Will I feel guilty if I don’t go through the rituals, especially that glazed-eyed last foray through the aisles on the day before Christmas, frantic that I’ve surely forgotten something for someone? Will my life be less full if I don’t experience the pushing and shoving and standing for hours in line?
I’m willing to risk it. Much as the commercials and ads have tried to convince me, I never quite bought the idea that shopping ’til you drop is an integral element of the season. At this point in my life, I pretty much have all the “things” that I want or need. And the kids are all grown up, no grandchildren are on the horizon, so there are no little ones to shower with toys. This year, in fact, we took a different tact and instead of giving nicely wrapped presents, we paid for a Christmas-time vacation for ourselves and the kids. We’ll have lots of good dinners, see the sights (without the big crowds), and there’ll be no messy house to clean up afterward. And of course, we made all the reservations and bought all the tickets online.
Time together is always the most precious gift of all, and this year that is more evident than ever. My daughter, who’s in the Navy, just found out that she’s being deployed to Afghanistan. She leaves in January, so this Christmas season is a special one, and I don’t want to waste any of it shopping.
Tell us what you think about online vs. “bricks and mortar” shopping, especially during the holidays. Do you do your Christmas shopping “out there” in the retail jungle, online, a combination of both, or neither (maybe you’re lucky enough to have someone else do it all for you). Do you have concerns about the security of online transactions? Is it easier or more difficult to find what you want online? Do you think less of a gift you receive that was delivered directly from an online vendor?
Deb Shinder, MVP
There are a couple of vulnerability assesment tools that are free to run. Of course, the simplest and most obvious assesment (and absolutely most essential) is to simply run Microsoft Update. It will scan your machine and tell you if you need updates on Microsoft software. Or, you can run Microsoft’s MBSA, a lightning-fast way to check for vulnerabilities.
However, MBSA and Microsoft Update are both Microsoft-specific, so you won’t be able to scan for vulnerabilities in other platforms and software.
You could try the free open source Nessus scanner (the Nessus license holder, Tenable, makes its money by charging for support and training, otherwise the feeds are delayed by a week), but it’s might be too complex for the average user. (We sell a vulnerability assesment tool, SNSI, for corporations. It scans both Windows and Linux systems, routers and printers for vulnerabilities. It’s a commercial-grade scanner and has done well. However, even though it’s a ridiculously inexpensive scanner, I realize it costs a bit more money than my average blog reader wants to pay. Plus, it’s geared for enterprise security, not home use.)
If you want something quick and simple, Secunia has just released a vulnerability assesment tool, called Secunia Software Inspector (via Donna). It will check for vulnerablities in a broad range of software programs on your machine.
Remember to be careful when applying patches. Always do them one at a time, with System Restore enabled. Sometimes, a patch can screw things up on your system (that’s a technical term for a night of pain trying to get your system back and running).
Feel free to comment if you have any other suggestions.
Alex Eckelberry
The community has answered my question: We don’t like short feeds! From now on, this blog will stay on full feed.
Thanks to all, and apologies for any hassles.
Alex
Readers of this blog through RSS may notice that I have gone to a short RSS feed. So, the articles you’ve been reading in RSS are not the full thing. If you find yourself irritated by this, let me know. I do prefer the short form but I can always switch back to the full feed.
Alex Eckelberry
A new CounterSpy 2.0 beta is up. If you haven’t tried it, please do and give us your feedback.
This new version is a major evolution in antimalware scanning and remediation. It is basically a hybrid antispyware engine with antivirus technologies (although it is not an antivirus product per se). It’s quite powerful and I’ll be writing about it in more detail next week.
The CounterSpy Beta 2.0 download page here.
Note that the malware database size is very large for the beta, so don’t be surprised at the large download size. This is only temporary. By the time we release it, it will be considerably smaller.
And you can always contact me directly with feedback as well.
Alex Eckelberry
Apparently we got some Russians a bit upset about the blog post yesterday on hotmail.ru. Patrick was just having a bit of fun — sorry we didn’t make that clear. Hotmail.ru is not a malicious site (as best as we can tell). And it’s been around for a while.
If we get anything more on the site, we’ll post more info.
Alex Eckelberry
We engaged Osterman Research to survey organizations that are using five different email management systems. The Osterman report presents the results of those findings, comparing Sunbelt Software’s Messaging Ninja with four other systems.
The research shows that Messaging Ninja is rated very highly by users, relative to other email management products with which it competes and Ninja can be managed at a lower cost per user. Ninja was compared to:
Ninja is easier to manage, has excellent anti-spam functionality, and is rated highest as “extremely reliable”. The time in person-hours spent deploying Ninja is 2.3 hours per 1,000 email users versus 7.4 hours for other products, and the time spent managing messaging security for 1,000 email users per week with Ninja is 1.1 hour versus 2.3 hours for other solutions.
This finding is significant: Messaging Ninja requires one-half of the IT time during a typical week to manage, compared to an average of the other systems. Extrapolate that, and you will find Ninja has a labor cost of $2.25 per user per year versus $4.50 per user per year for the average of the other systems. The full Osterman whitepaper is here.
Alex Eckelberry
We’ve had a feature for years in our desktop antispam product, iHateSpam, which attempts to send a fake “bounce” bounce message back to the sender.
We’ve always felt a bit concerned about this feature, primarily because it’s largely useless (what, you’re bouncing back to a spam zombie or a spoofed address?). However, it remains one of iHateSpam’s most popular features (in other words, if we took it out, there would be shrieks and howls of protest). We’ve kept it in the program but with plenty of caveats when you run it.
One purpose of this type of feature, however, is to “fake” someone with a bounce message. Sick of getting an email from someone? Send them a fake bounce.
On the same philosophy, BounceBully also promises to send a fake bounce email back to the recipient.
From Steve Bass:
The truth is that bouncing spam back to the creeps who sent it just isn’t worth the trouble. Too often the spammer’s address is bogus–and my guess is they wouldn’t take the time to remove you from their list. (“Oh, my, Steve Bass’s address isn’t working any more. I’ll just spend my time removing the dear boy.”)
But what if you have a bozo or two constantly sending you dumber-than-dirt jokes? You know, the kind you didn’t find funny even when you were in the fifth grade.
You could politely ask to be removed from their list. I usually say I use my PC primarily for work, my boss snoops in my e-mail (he probably does), and I don’t want to get into trouble.
More fun, though, is to use a program that bounces e-mail back to the putz, showing that your e-mail address no longer exists. And guess what: You can do it with BounceBully. It’s a freebie that takes the e-mail you receive and fires it back with all the right language–saying, essentially, that your e-mail address is no more.
Try it out by sending yourself a test e-mail–cut and paste the mail into BounceBully and hit Send–and see what happens.
Here’s the link:
BounceBully
Alex Eckelberry
Whonu was launched about a year ago as a metasearch tool (meaning, it searches multiple search engines) by developer Derek Franklin. It’s been evolving.
One thing caught my eye: His choice of a name (one letter away from adware maker Whenu) is unfortunate. Of course, the name means “Who knew”, and I suspect Derek simply never realized he was so close to WhenU in name. Kind of reminds me of famous marketing misnomers, like the Ford Pinto (meaning “small genitals” in Brazil) and Chevy Nova (meaning “it won’t go” in Spanish). Correction.
Anyway, putting all that aside, I ran a few quick searches on it and it’s not bad, although I certainly have not done any exhaustive analysis of it.
Whonu link here.
(Oh, and Derek’s not the only one. Here’s a few other unfortunately named products that are close to adware products in name: Zengo and Clario. Feel free to add others you can think of in the Comments section.)
Alex Eckelberry
(Hat tip)