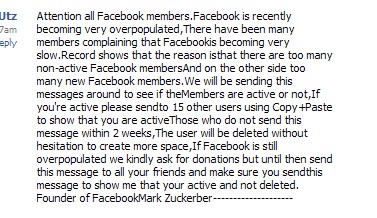
Spam currently running around Facebook spoofing Mark Zuckerberg.
Alex Eckelberry
The Legacy Sunbelt Software Blog
The Great Years: 2004-2010
Spam currently running around Facebook spoofing Mark Zuckerberg.

Alex Eckelberry
The problem of being blacklisted by a security product has spawned a new entrepreneurial activity: Lobbying security companies to become delisted.
Bill Belcamino, a former executive with Miva and Auctiva, has started a new company, called Antivirus Compliance.
The goal of this company is to get companies off the detections of antivirus/antispyware engines, and improve their ratings in places like SiteAdvisor.
He’s proud of his accomplishments:
I personally found the ALOT.com domain, defined all aspects of the new brand, defined the Antivirus Compliance strategy and ultimately delivered the clean ALOT toolbar and homepage solution. I repaired the flagged SuperHoroscopes.com website and worked with McAfee SiteAdvisor to change the RED rating to GREEN to reflect my efforts. I defined and vetted with industry experts the strategy for the cleanup of Screensavers.com (in progress). I have an unblemished track record in this space and am highly confident that I can repeat this process for any challenges that may be in front of your company.
How will being clean impact the bottom line?
As a direct result of my leadership, steady product vision and Antivirus Compliance expertise, the ALOT brand significantly outperforms the legacy Starware brand: RPMLU is 62% higher and retention is 14% improved and revenue growth is phenomenal. Every product success metric is up, while the brand is able to provide a clean, virus free and malware-free user experience.
However, let’s consider that Alot.com, SuperHoroscopes.com and screensavers.com are all owned by Miva — a company without the most perfect reputation (remember Starware?). And let’s remember that Screensavers.com has stuff still listed by quite a few folks.
While my blog headline might have been provocative, it could be argued that Belcamino may be performing a service in helping companies clean up their act. However, I do hope that security companies rely on their own networks of contacts and information to make an informed decision. Ultimately, it’s the user who will be impacted in any de-listing decision.
Alex Eckelberry
This bozo enterprising fellow actually thinks we’d pay him? Unreal.
Dear Sir,
We are starting new service for software vendors, in this this service we will inform about full version, serial , keys or any availabe method avaible to use the prouct without paying their fee on public areas like forums, sites, rfree hosting etc. as a inaugral we want to inform you that a working full version of you product is available on this site and probably others also.We have tested this and it is working without problem.
http://(obfuscated).blogspot.com/obfuscated)
http://rapidshare.com/files/obfuscated)
you have already lost 1000$.
would you like to recieve this type of alert on daily monthly basis. Our starting monthly fee is 100$ per product monthly. please send your payment to versingdictionary@yahoo.co.in Thanks any unanswered question? write us back.
We are even currently working on how to stop torrent. no domain/page has been setup to prevent detection from sharing site forums etc. You can see our payapl verification before processing fee on your browser.
Thanks
versingdictionary@yahoo.co.in forums etc. You can see our payapl verification before processing fee on your browser.
Thanks
Name: Rahul Khandelwal
Company: no
Email: versingdictionary@yahoo.co.in
Telephone: none
Country: India
Previously attempted to contact Sunbelt? No
2008082111275789233
Code: CONTACT_US
Alex Eckelberry
Can you hear this sound? If so, you’re probably a younger reader of my blog.
As people age, their ears may lose the ability to hear higher frequencies (such as above 20 or 22khz).
Mosquito ringtones take advantage of this fact for teenagers, giving them downloadable “silent” ringtones that adults can’t hear.
Cute.
Alex Eckelberry
A customer, Nigel, just sent this email on our VIPRE tutorial video:
I have just installed it and all is well except for one thing — the installation tutorial (the one labeled Welcome to Vipre). The music that accompanies the explanations is so extraordinarily irritating and distracting that I literally found it impossible to stay focused on what was being said. Had I not been a committed customer of Sunbelt, I would have been tempted to ask for my money back on the theory that I can’t trust anyone with such terrible taste in music and lack of appreciation for the customers’ feelings or intelligence.
Err. I was the one who made that video. And chose the music. And did the voiceover.
So now that I’ve been found out to be the Philistine lout that I truly am, I decided to set matters right: I made a new video for anyone who wants a more pleasing sound, using Pachelbel’s Canon, played by Ray Hutchings on the piano. You can watch it here (prepare yourself).
We’ll do almost anything to make a customer happy.
Alex Eckelberry
Our manufacturing at risk? US carmakers are up in arms over new legislation that would require an inordinate amount of tracking of container shipments, which they deem largely useless in terms of protecting the security of this country. They argue that the new regulations would disrupt “just in time” manufacturing, pretty much the only way our carmakers can actually manage production in a time when consumer whims change at the the drop of a hat (hat tip).
Inspector accidently breaks instrumentation, grounds planes. Then, the astonishing and deeply disturbing story of a TSA inspector who blunders around the outside of a number of planes, only to damage key instruments that, if broken, presents a serious safety risk. The damage is found and the planes are grounded, thankfully. What if they’d made it up in the air? No one should ever be allowed near a plane who doesn’t have the qualifications. Unbelievable. (hat tip)
Watch lists: More silliness with commercial pilots on no-fly or watch lists.
The TSA Blog also responds to allegations that it’s not putting people who don’t have ID on a list. It says it doesn’t.
I don’t get that. About a year ago, I was traveling and forgot that my driver’s license was expired (I had renewed it, my wife had put it aside for me, but I forget to put the new one in my wallet). A screener caught it, and I was sent downstairs and got an SSSS boarding pass (which means that you have enhanced screening).
No problem.
But then my next two trips, I automatically got the SSSS on my outbound boarding passes (not on the return). I must have been on some list.
None of this type of thing would bother anyone, if they felt that the security of our nation was actually being served. But these are obvious and painful examples that we are doing more to hurt ourselves than secure ourselves.
I have no grudge against TSA or border control people. I’ve talked to a number of them, and many of them are decent, good people — really. However, they are in a bad spot, following policies and a culture put in place that does not prioritize how to deal with real risks.
The solution is leadership. Invertebrate committees will always come up with these types of solutions. Someone in Homeland Security has to get in charge and say “Let’s get real about what the security priorities are in this country”. And that person has to have the gumption to take the hits internally in the vast bureaucracy.
Alex Eckelberry
Good stuff.
The TCP/IP protocols were conceived during a time that was quite different from the hostile environment they operate in now. Yet a direct result of their effectiveness and widespread early adoption is that much of today’s global economy remains dependent upon them.
While many textbooks and articles have created the myth that the Internet Protocols (IP) were designed for warfare environments, the top level goal for the DARPA Internet Program was the sharing of large service machines on the ARPANET [Clark, 1988]. As a result, many protocol specifications focus only on the operational aspects of the protocols they specify and overlook their security implications.
Though Internet technology has evolved, the building blocks are basically the same core protocols adopted by the ARPANET more than two decades ago. During the last twenty years many vulnerabilities have been identified in the TCP/IP stacks of a number of systems. Some were flaws in protocol implementations which affect only a reduced number of systems. Others were flaws in the protocols themselves affecting virtually every existing implementation [Bellovin, 1989]. Even in the last couple of years researchers were still working on security problems in the core protocols [Gont, 2008] [Watson, 2004] [NISCC, 2004] [NISCC, 2005].
Alex Eckelberry
Well, we got lots of positive feedback on the new look of the blog, but we did keep getting reports of problems in Opera. Right now, we’re back to the old look until we can get a handle on what’s going on.
Alex
Robert made a new look for the blog. Let me know your thoughts — especially how it’s looking in your browser.
Alex Eckelberry
Update: Getting reports of badness in Opera. We’ll fix it.
Tropical Storm Fay was a non-event around here. But we still saw some magnificent clouds yesterday. Robert La Follette, our creative director, took some beautiful HDR pics of the scenes.
A view from our building, no clouds yet:
Dunedin, FL at dusk:
More views from our building:



And another shot of Dunedin, FL:

Btw, check out this stunning HDR picture of the Clearwater Memorial Bridge that Robert took last weekend:
Alex Eckelberry
On the heels of the release of the new consumer version of CounterSpy yesterday, the Enterprise version was officially released today.
Alex Eckelberry
The indefatigable Rick Green of the Hartford Courant blogs about Julie Amero’s ongoing plight.
Alex Eckelberry
I hope it was not felt that my post yesterday on Fuse Kit (being used by malware authors) would in any way impugn this very cool, very useful program. This has gotten some attention since SC Mag wrote a story on the general subject of malvertisements.
The author of Fuse Kit, Moses Gunesch, sent me an email today, understandably not to happy:
Fuse Kit is an animation system for Flash. It cannot be used for malicious purposes, in fact it has no networking code in it at all. The fact that this horrible malware person used it in a banner ad is entirely incidental (Fuse is used in banner ads for animation purposes).
Sandi Hardmeier’s mirrors these sentiments on her blog here.
Fuse Kit is a very cool, useful tool that happens to be used by malware authors to create animations in malicious advertisements. It’s about the same as saying that MS Paint is being used by the malware authors — it may be being used to create the animations, but it’s not the source of the scripts, the network activity, or anything that would directly contribute to the spawning of these ads.
Alex Eckelberry
Today, we officially released the consumer version of our all-new CounterSpy 3.1 product. (It’s actually version 3, but due to having to align our version numbering scheme with our Enterprise version, it was released as 3.1).
This is a major upgrade to CounterSpy. All-new threat engine, all new technology — completely re-written from the ground-up for fast performance. As always, none of our products bundle toolbars, our trial versions are full versions, and we provide free support.
Give it a whirl and let me know what you think. You can always email me your opinions directly.
Users of VIPRE will find the interface familiar — CounterSpy is simply a sub-set of VIPRE, excluding features specific to viruses. CounterSpy customers can upgrade at anytime to the VIPRE product for a small cost.
One small note: Unlike a “silent” preview edition posted last week on our website, this version comes with the On Access feature of Active Protection disabled by default (it can always be re-enabled). This feature will invariably conflict with some antivirus programs’ real-time protection, and since almost everyone runs this product alongside their existing antivirus product, it’s not necessary. A further explanation is in our video tutorial here.
Full company propaganda here.
Alex Eckelberry
Fuse Kit is a cool utility to create animations in Flash. Unfortunately, it’s popular with malware distributors, who are using it to create malicious advertisements.
These malicious advertisements get served on sites — even mainstream sites. They push malware. (Just to make sure there’s no confusion, this is not a drive-by exploit. Typically the user will see a fake “system scan” message that “Your system is infected!”. If the user actually believes it and clicks “OK”, and then downloads and installs the “security software”, the infection will occur. However, it’s not to lighten the effect — it’s very devious social engineering.)
More from Sandi Hardmieir, who has been doing just about the best job of tracking these:
I am seeing reports of the malicious redirects remaining dormant for a week before visitors to victim web sites are hijacked and redirected to fraudware sites. Web sites simply *must* increase their due diligence checks with any new advertiser. It is going to take time, and it is going to cost money, but what alternative do web sites have if they want to protect and keep their readership, and if they want to avoid the inevitable end result of malvertizing, which is that more and more of visitors to their sites are going to block all advertising.
That being said, it is not all doom and gloom – not yet. There is something that you can watch out for, even if a particular advertisement passes the adopstools test, and passes other security tests. You see, even if the hijacking behavior of a malvertizement is “dormant” there are still subtle hints of trouble ahead that you can see if you know where to look.
For example, in the case of the newsweek malvertizement, by leaving network traffic capture software (or Fiddler) running when the advertisement displays on a web page, we see that the following URL is touched – adoptserver.info/state_.gif?url=[removed] and that the malvertizement is the referrer. adoptserver.info is a known “bad actor”. Its name servers are supplied by the now infamous “estboxes”. Any advertisement that leads to such a domain being touched should be suspended, no questions asked. Don’t wait for the complaints to start.
More here.
In an email this morning, Sandi told me that she’s “very worried” about these latest malvertisements.
Alex Eckelberry
Pretends to be Windows Media Player.
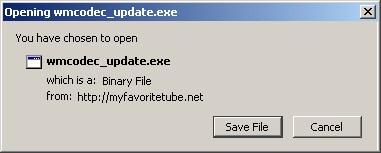
Installs a zlob fake codec with fairly poor antivirus detection, then installs the current plague, Antivirus XP 2008.
(I admit, commenting on one of these fake codecs/rogue security products is kind of like discussing a single bullet in the middle of a full-blown war.)
Alex Eckelberry
Our good friend Chris Boyd continues to report on some baffling things.
First, another site with pirated movies pushing Zango. He’s starting to suspect that there’s a ton of these types of sites pushing Zango.
But then, the mother of all confusing popups when you try to cancel Zango. It’s the first he’s seen of this.

It’s worth noting that the indefatigable Ben Edelman complained earlier about confusing Zango button placement. But this latest popup tops his earlier complaint.
Alex Eckelberry
PaperGhost goes to movietvonline(dot)com, gets pushed to install Zango, and gets to watch a horrible pirate of The Dark Knight.
The story here.
Alex Eckelberry
Antivirus XP 2008 delivers a malware certed from GlobalSign. I’ve sent them an email.
Alex Eckelberry
Off topic, but the predictions of this blog — that the oil prices were a speculative bubble soon to burst, and that the dollar would rally — have come to pass.
(Ok, ok! I’ll get back to writing about security issues.)
Alex Eckelberry