The March Madness that has become the description of the National Collegiate Athletic Association (NCAA) basketball tournament in the U.S. begins March 18. In recent years it’s turned into something of a national event with office pools, Americans glued to any source of information about the college games and, unfortunately, a spike in malware targeting corporate networks. Since most of the early NCAA games in the tournament take place during business hours, cyber criminals work hard to infiltrate corporate networks by tricking workers who are surfing the web looking for scores, live updates and streaming tournament coverage.
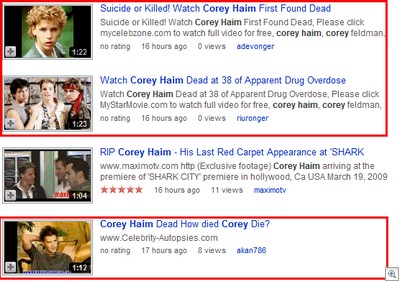
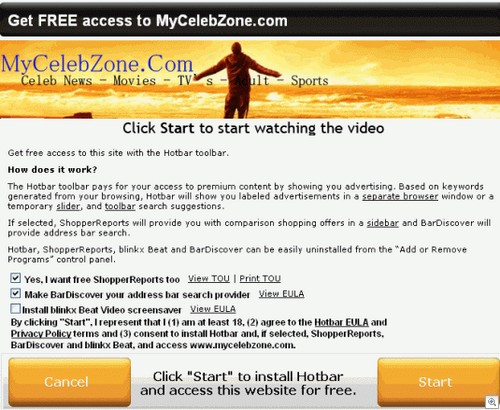
In 2007, research firm Challenger, Gray and Christmas of Chicago estimated that more than 22 million workers followed the tournament by checking scores online during work hours. Although live streaming is available on legitimate sites, some fans will undoubtedly become impatient while searching the web for instant updates and will be directed to a host of malicious websites through poisoned Google search results. These sites will look legitimate and some may even provide updated game results, but the threat is that they will also expose work-based computers to viruses, phishing attacks and other malware embedded in web pages, banner ads and fake video streaming downloads.
Sunbelt’s anti-malware researchers offer the following “5 Tips for Responsible Web Surfing” in order to limit the risk of falling prey to malware attacks:
— Make sure your antivirus and Web filtering programs and Windows patches are up to date
— Do not click on links on untrusted sites or email offers – rather, enter URLs directly into your browser
— Do not download any application or program from an untrusted source in order to view video feeds
— Do not provide passwords or other personally identifiable account data from your other Web-based accounts for any reason when attempting to watch games – legitimate sites should not require this
— Be cautious when you follow search engine results for top news stories or score updates
Tom Kelchner