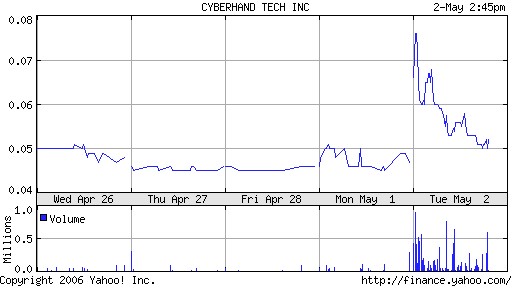
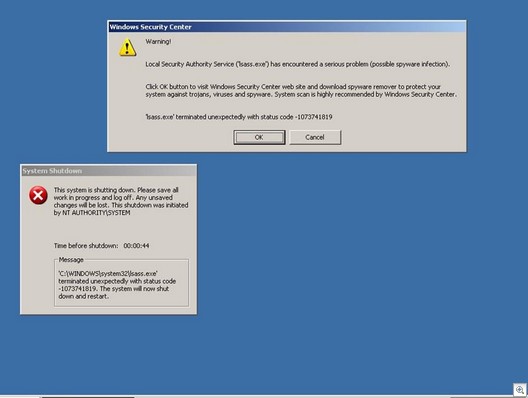
In the Brave New World of many of numerous science fiction stories, a totalitarian world-wide government uses implanted microchips to control the minutia of its citizens’ lives. Twenty-five years ago, the theme made for entertaining, if somewhat far-fetched sci-fi. Today it doesn’t seem that far-fetched at all.
The technology is certainly here. Chips are routinely implanted in animals for various purposes. RFID (radio frequency identification) tags are placed in the ears of livestock so farmers can know which cattle are theirs, replacing traditional methods of branding. Veterinarians offer products such as HomeAgain and 24PetWatch, chips that can be implanted in pets to store owner identification, medical information, etc.
In 2004, it was reported that a number of government officials in Mexico, including the Attorney General, had been implanted with microchips that function much like electronic keycards to allow access to secure areas. The difference is that you can’t forget or misplace this key, and it would be difficult (although not impossible) for someone to steal it.
That was also the year the Food and Drug Administration approved the use of RFID chips by hospitals to identify patients.
Then in 2005, Tommy Thompson, the governor of Wisconsin and former U.S. Security of Health and Human Services, announced that he was having an RFID chip injected into his arm to provide quick access to his medical history and records. Although this announcement made big news, we’ve not been able to find verification that he ever went through with the procedure.
This year, “chipping” made the news again when a company in Ohio used RFID chips implanted in workers to control access to certain rooms. The company’s CEO said the chips are no different from ID cards.
A number of bars and private clubs, in places as diverse as Barcelona, Spain and Glascow, Scotland have offered to let customers pay their tabs via an implanted RFID tag.
Most of these examples have used chips marketed by VeriChip, a Florida company that makes the chips, which are about the same size as a grain of rice and can be easily injected under the skin, usually into the fatty tissues of an arm or leg. It’s a safe medical procedure, done with only local anesthetic. They push the chips as a solution to problems ranging from lost dogs to kidnapped children to wandering Alzheimer’s victims.
The technology being used for these applications is a “passive” one – that is, the chip just stores information and transmits it over a short range (a few meters). To access it, you need a special scanner. The next logical step is a more active chip that can transmit over longer distances. Some chips can be tracked by satellite, and some companies have announced plans to incorporate a Global Positioning Satellite (GPS) transmitter into implanted chips, which would allow for the implanted person to be tracked wherever they go in the world. Chips could also record a person’s movements and activities and store the log on the chip itself or send it to a monitoring station.
Certainly this technology could offer lots of advantages. As an access control method, it would be much harder to tamper with or steal than keys, passwords, smart cards and the like. It’s cheaper than biometrics. As a medical information store, it could provide emergency workers with instantaneous, valuable information about a person’s health history that might save lives. As a law enforcement aid, it could prove or disapprove the whereabouts of accused persons. It could also make it much easier to keep track of (and thus keep safe) animals, children and mentally disabled people.
But where does it stop? How much of a step is it from allowing parents and pet owners to keep tabs on their charges to allowing employers to keep track of their workers and then to allowing governments to keep track of all of us, all the time? Of course it will happen in increments. Who’s going to argue with implanting a tracking chip in a sex offender who’s been released from prison? Or implanting chips in soldiers going to war, so they can be more easily located if they’re wounded? Or in children, for their own safety? And so forth.
As chips become more widely used for these noble purposes, they’ll also become more accepted by the public. Employers can require implanted chips that act as time cards, logging when workers start and stop work. Who could object? After all, it’s voluntary; if you don’t like it you can work somewhere else – at least until all companies are routinely using this method. Chips could also replace passports. Again, you don’t have to get one if you don’t want to leave the country. Except that if it works for passports, it will probably soon be extended to drivers’s licenses. I guess you can just not drive, but we all know we’re headed toward requirement of a national ID card. Having that info “chipped” will probably be voluntary. In the beginning. But if national security is at stake …
The problem is that it’s hard to make a case that chips are bad. Like any technology, they can be used for good or evil. Here are some of the uses (many of them commendable) that were proposed by Digital Angel, a company that makes RFID and GPS implants for pets, fish and livestock.
However, the idea of such technology in the hands of government makes many privacy advocates very nervous – especially in conjunction with other political and social trends. For instance, most babies are born in hospitals today, and all children are required to have immunizations before attending schools. Since the implant procedure is a simple injection, it would be very easy for health care personnel to implant chips immediately after birth or in early childhood without the recipient even knowing it was being done. And with many in the U.S. advocating government takeover of the healthcare system (and nationalized healthcare already in place in many countries), well, you can see where this could go.
Chips could also be used to further political agendas. Conrad Chase, director of the Barcelona nightclub that uses the VeriChip payment system, has been quoted as saying all gun owners should be required to have a microchip implanted in their hands to own a gun. A “smart gun” could be designed so that it wouldn’t fire unless in the hands of someone with a chip. This could give the government almost complete control over who does or doesn’t have the ability to ability to defend themselves with a firearm. On the other side of the aisle, the Patriot Act gives the government broad powers that bother many people, such as the ability to access library records. If an implanted chip were required to check out library books, that information would be much easier to obtain as it would always be with the individual.
In response to all this, some lawmakers are trying to ameliorate the possible damage. A state representative in Wisconsin has introduced a bill that would prohibit requiring anyone to have a chip implanted or doing it without their knowledge.
What do you think? Do the benefits of implanted chips outweigh the dangers? Are implants okay for kids, animals, and the elderly? Should implants always be voluntary or is it fine to mandate chips for prisoners and parolees? Should implanted chips be banned by the FDA? Should be government have control over implants? Under what circumstances – if any – would you have yourself implanted?
Deb Shinder