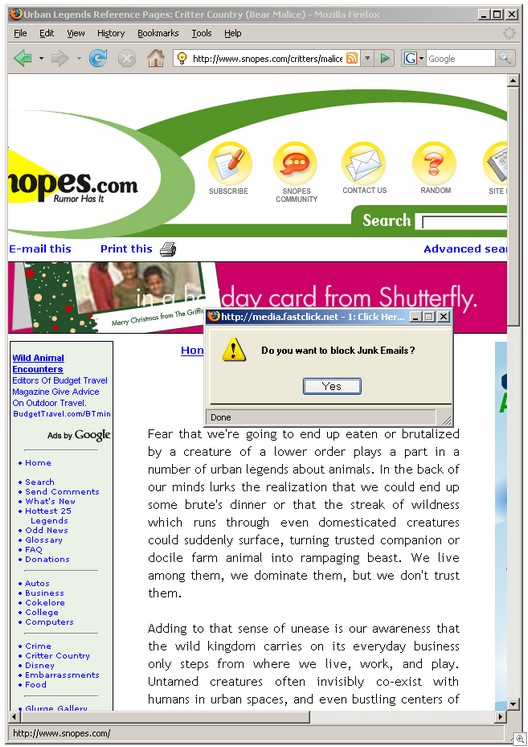
In a classic “Thank You For Smoking” spin, Zango CTO KeithKen Smith has responded to my post on Snopes pushing adware:
To be sure, Snopes was pushing Zango: in exactly the same way that it continues to “push”, oh, let’s see, umm, QuickBooks, the Oreck Air Purifier, eBay, a call spoofing service (served up helpfully by Google), and an e-tutorial service for kids who aren’t doing well in school. In other words, Snopes.com serves ads, and makes money from those ads.
This is sophistry at its best and ignores the key fact: This pop-under ad was pushed consistently (at least in my geographic region) and could have easily been turned off through the Fastclick UI. Furthermore, this was one of several pop-unders — it was not a banner ad or a Google adword (which the site has plenty of).
As I’ve said before, I have no problem with advertising. I do have a problem with constantly pushing this type of ad. I did notify Snopes months ago, and they ignored my notification. Perhaps they considered my email spam, perhaps they never saw it, perhaps they didn’t understand it — whatever — but the ultimate point is, it was an ongoing campaign that was prominent on this site.
 Later, after ending the original post with
Later, after ending the original post with “these aren’t the droids you’re looking for” ”Nothing to see here folks. Move along” (yes, he really does say that), Keith then pushes the old “we give great content in exchange for loading your machine up with crap”:
Zango uses desktop advertising to help keep the content we DO install FREE. In other words, if you install our SpamBlockerUtility, you really do get an anti-spam engine that you would otherwise have to pay money for. And yes, while you have it installed, we will show you some targeted ads, a trade-off that we describe no less than three separate times during the install process. But you really (honestly, truly) do get the anti-spam software that the ad referred to.
This is disingenous. You may get a spam blocker, but what you get in return is patently awful.
And the notice and disclosure? Zero, by today’s standards. It’s buried in a massive EULA, as Harvard researcher Ben Edelman has confirmed independantly. We’re back to 2004 all over again.
Remember that almost two years ago, Zango trumpeted it’s new notice and disclosure, promising:
It’s important to us that consumers understand our products and that they provide full, informed consent before installing our software. Is this the last of our efforts in improving the user experience? Absolutely not.
Now, apparently because this spam blocker is part of their “Hotbar” acquisition, that notice and disclosure is not required.
Zango has a real problem. By our own research, 80% of its business comes from seekmo, the porn side of its business. They need more “legitimate” customers but have an increasingly difficult time getting them. We believe that the company is having a very difficult time actually spending their ad dollars to promote their product, since so few sites will take on their ads.
And now, with Snopes no longer pushing a Zango ad, it’s even harder.
And, separately, Snopes responds:
Reader CD got a response from Snopes, which he reports as following:
Thank you for inquiring about the possibility an advertisement that violates our acceptable advertising guidelines at www.snopes.com/info/faq.asp#ads may have been displaying to some visitors to our site.
We have temporarily removed from our site *all* advertisements from the agency that handles the ad in question while we investigate if and how such an ad was indeed being served to some of our visitors.
We don’t ever knowingly run adware or malware on our site — that’s not who we are or who we’d ever want to be.
Ok, I’ll give the Mikkelsons the benefit of the doubt. It’s possible that the advertisements we observed were based on geolocation, and it’s quite possible that the they never knew that the ad was pushing adware.
I wouldn’t stop using Snopes. It’s a good service. I’ll keep checking the site, but I really doubt you’ll ever see anything like this happen again.
However, one part of the strategy of the Antispyware Coalition to reform the business is “public shaming” — that is, to shine light on bad practices. Snopes has learned a hard lesson. They’ve stopped pushing these ads, and the internet community is a bit of a better place now.
And that, folks, is a good thing.
Alex Eckelberry


 Later, after ending the original post with
Later, after ending the original post with