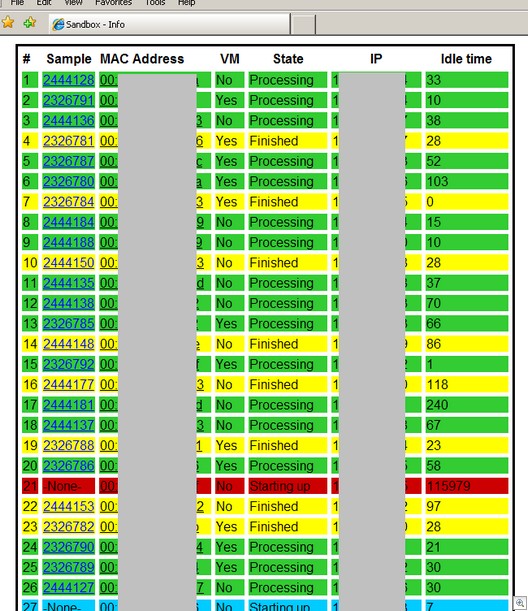
Robert LaFollette, our creative director and a professional photographer, took some great pictures during the holiday.
He made an HDR photo that’s one of the best I’ve ever seen – shot on Christmas Eve on nearby Honeymoon Island.
Here’s his description of the picture:
Photomatrix was really quite easy to use, but to get the best results, one needed to get some specifics done right while out capturing the scene. Over the holiday break, I decided to study some more in HDR, so I set out to see what I can find.
While hiking on the trails at Honeymoon Island, Florida, I came across a scene that I have seen a hundred times before, but never attempted to capture it, for I knew the results would not be as good as I saw them. This time however, I met the challenge head-on. Typically, when one tries to photograph a landscape that has a lot of detail, and if the light is not right, the results look like it was taken with a point-n-shoot that we all have seen.
One of the tricks to a successful HDR photo, is of course knowing what you need. So, in this case, I had several tools to call upon to get the shot I was looking for. Those tools of course was my camera, wide angle lens, tripod, bubble level and remote release. The next trick is to set your camera at f/22, ISO 100, and once I get everything set up and the lens focused, switch the lens into manual focus so that is won’t change the focus point during your captures.
The reason for all this preparation is that you need to take at least 3 different shots, but the more the better. To do this, there are several different ways to accomplish this. The first, and perhaps the easiest, is to us your cameras AEB (Auto Exposure Bracketing) setting, whereas you will take 3 different exposures. Another way is to use your cameras Exposure Compensation, where when you take each frame, you expose the scene differently. Lastly, you can take the exposures manually. The end result will be one frame -1, the next at 0 and the last at +1 in exposure reading.
Of course, a steady tripod so that each frame is exactly the same, which is also true for the focal length, so one you get everything set up, the only thing you need to do is expose each frame differently. Also, keep in mind the Rule of Thirds for your composition, for without it, the shot will not be as dramatic!
For my shot, I used 5 frames, -2, -1, 0, +1 and +2, for the more frames you have, the more data you have to work with. Once you take all your shots, you are ready to assemble them in Photomatix.
I took all 5 of my frames (which I shot as RAW files), and ran them through Photomatix. Here, you can tweak the settings to get the desired results, which after you play around with them a bit, you can get the hang of just what they do and how they affect the output.
To learn more about how to use the software, here is a great tutorial on HDR photography that will explain everything. So the next time you want to try something new, give HDR a try, for once you see it’s powers, you will be addicted for life!
We’ll start with the shot with just one exposure:

And here are the five frames used to generate the HDR:

And here is the final image, produced in Photomatix:

(Another link here.)
There’s no special photoshopping going on here. Other than some small modification to the clouds (to compensate for their movement during the shot), it’s just Photomatix doing the work. It makes my playing around with Photomatix look infantile.
Robert also took some other great pics on the same day:
![2931[1]](http://sunbeltblog.eckelberry.com/wp-content/ihs/alex/2931%5B1%5D.jpg)
![2928[1]](http://sunbeltblog.eckelberry.com/wp-content/ihs/alex/2928%5B1%5D.jpg)
![2932[1]](http://sunbeltblog.eckelberry.com/wp-content/ihs/alex/2932%5B1%5D.jpg)
![2930[1]](http://sunbeltblog.eckelberry.com/wp-content/ihs/alex/2930%5B1%5D.jpg)
Incidentally, Robert did teach me one trick which has made me (a rank amateur) a much better photographer. I have a Canon Rebel XTi, and he taught me to simply shoot in Aperture Priority Mode (AV mode), playing with the ISO settings to compensate for light. It’s a wonderful trick that will enable you to consistently take great pictures, without worrying yourself over a lot of the technical details. It works for well over 90% of the pictures you might take.
And shifting off on a slight tangent — I like my Rebel XTi, but one camera I seriously considered when I was shopping last year (again, as a rank amateur) was the Nikon D40. I found out recently that Nikon’s ad agency, McKann Erickson, gave out 200 D40s to the residents of Georgetown, South Carolina and then put the results up on a website. It’s a great piece of PR (I’m not recommending one camera over another, I just found the effort interesting).
Finally, I hope all of you had a wonderful holiday!
Alex Eckelberry



![2931[1]](http://sunbeltblog.eckelberry.com/wp-content/ihs/alex/2931%5B1%5D.jpg)
![2928[1]](http://sunbeltblog.eckelberry.com/wp-content/ihs/alex/2928%5B1%5D.jpg)
![2932[1]](http://sunbeltblog.eckelberry.com/wp-content/ihs/alex/2932%5B1%5D.jpg)
![2930[1]](http://sunbeltblog.eckelberry.com/wp-content/ihs/alex/2930%5B1%5D.jpg)
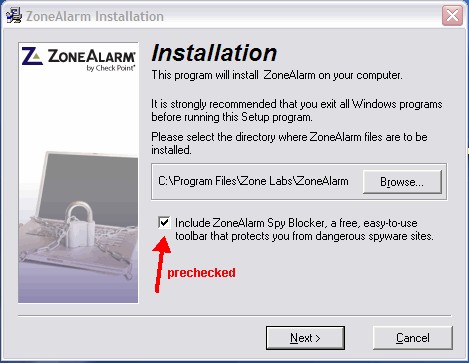
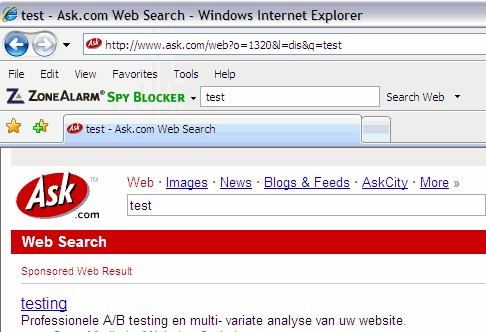
 If you enjoy a bit of irony, have a gander at the Amazon.co.uk reviews (and comments) on the inexpensive
If you enjoy a bit of irony, have a gander at the Amazon.co.uk reviews (and comments) on the inexpensive