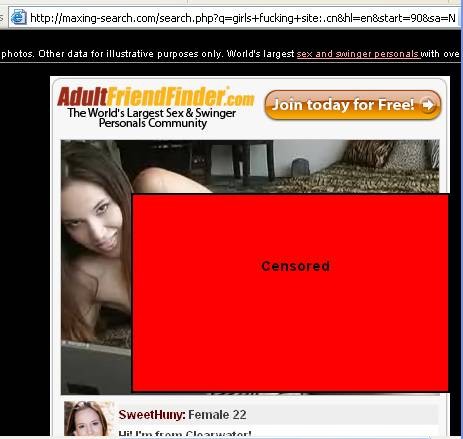
Today, the FTC announced a settlement with Adult Friend Finder:
The settlement bars the defendant from displaying sexually explicit ads to consumers unless the consumers are actively seeking out sexually explicit content or unless the consumers have consented to viewing sexually explicit content. It requires the defendant to take steps to ensure that its affiliates comply with the restriction, and end its relationship with any affiliates who do not comply. It also requires the defendant to establish an Internet-based mechanism for consumers to submit complaints. Finally, the settlement contains bookkeeping and record- keeping requirements to allow the Commission to monitor compliance.
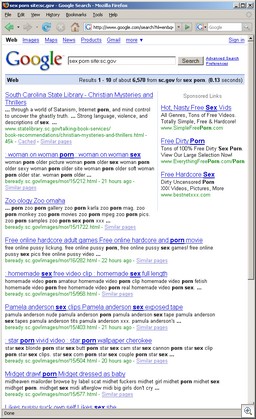
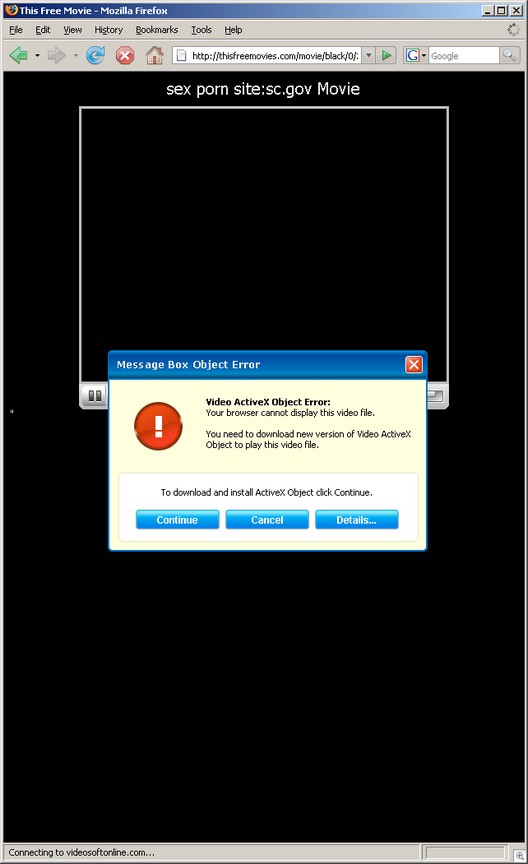
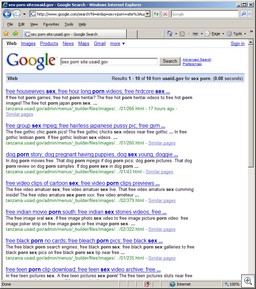
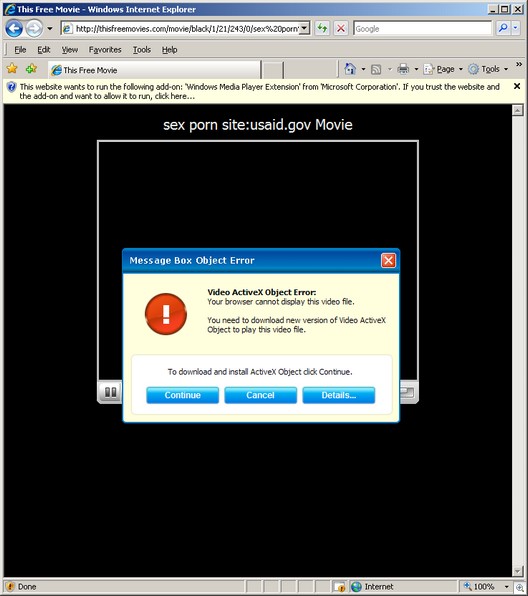
(Note that it was just a few days ago that we documented a very graphic AFF video.)
Some comments: A major reason for AFF’s problem with this type of advertising is its extremely aggressive affiliate programs, providing high payouts to affiliates who recruit subscribers to AFF — or even simply refer people to AFF (pay-per-click programs). While AFF may no longer provide materials to their affiliates which are sexually explicit, this company will need to pay particular attention to its affiliate channels. There’s just too much money there.
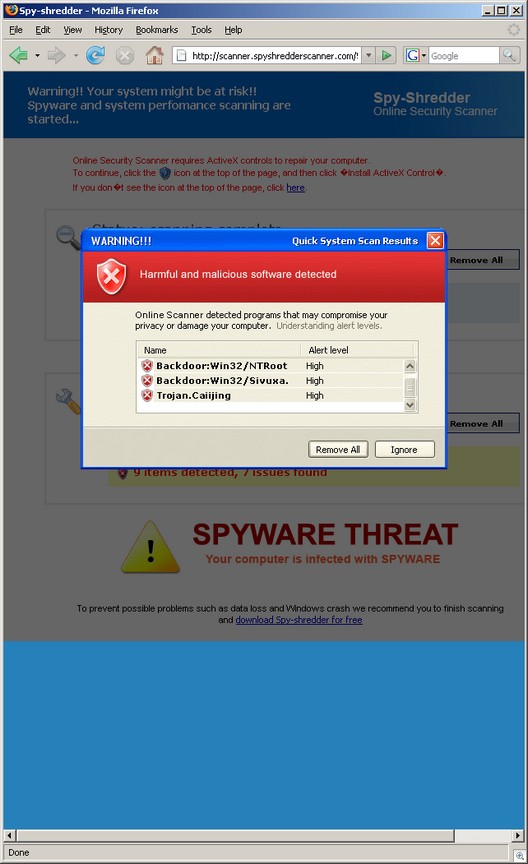
And any malware researcher has also seen AFF ads in spyware. Whether this is through affiliates or not, it is still the responsibility of the company to advertise through legitimate channels — not through malware.
Their advertisements have also been seen extensively in fake pages on social networking sites (MySpace, Tagworld, etc.), and there’s been plenty of fake “Friend” invites through these networks — which are only designed to feed the site with more subscribers. Again, this may or many not be done directly by AFF, but it’s still their responsibility.
Another problem with AFF is the fact that company’s service itself is sold in a highly misleading fashion:
- The advertisements feature actresses or porn stars, who are not necessarily indicative of the women actually on the site.
- A Volicitypress study which showed that the male to female ratio is 10:1, and with about half of the women actually interested in a relationship with a man.
In short, it is highly unlikely that a man who signs up for the site will actually be able to “hook-up” with a woman, either one represented by the misleading advertisements, or any woman at all.
It’s good to see the FTC has taken some action here on the most egregious problem. But there’s still other issues with this company.
Alex Eckelberry